The decentralized mental property platform Unleash Protocol has misplaced round $3.9 million price of cryptocurrency after somebody executed an unauthorized contract improve that allowed asset withdrawals.
In accordance with the staff behind the blockchain venture, the attacker obtained sufficient signing energy to behave as an administrator of Unleash’s multisig governance system.
“Our preliminary investigation signifies that an externally owned tackle gained administrative management through Unleash’s multisig governance and carried out an unauthorized contract improve,” the corporate says in a public announcement.
“This improve enabled asset withdrawals that weren’t accredited by the Unleash staff and occurred exterior our meant governance and operational procedures.”
Unleash Protocol is described as an working system for managing mental property (IP) by changing it into on-chain property (tokens) that can be utilized as collateral inside the DeFi ecosystem.
It supplies a monetization layer via good contracts and mechanically distributes licensing and royalty income to predefined stakeholders based on on-chain guidelines.
By performing the unauthorized good contract improve, the attacker unlocked the power to carry out withdrawals, leveraging it to steal WIP (wrapped IP), USDC, WETH (wrapped Ether), stIP (staked IP), and vIP (voting-escrowed IP) property.
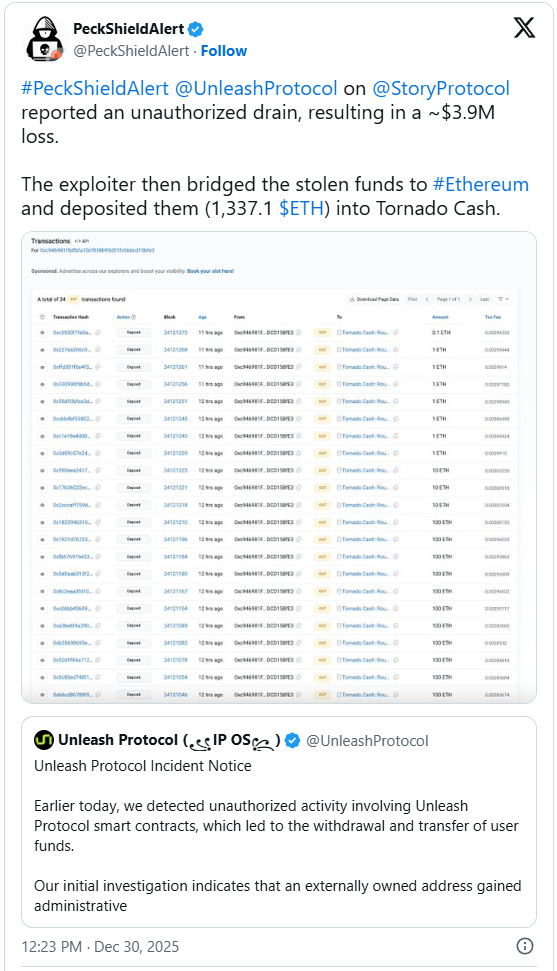
Blockchain safety specialists at PeckShieldAlert report that the unauthorized drain equates to losses of roughly $3.9 million.
After their withdrawal, the property had been bridged through third-party infrastructure and transferred to exterior addresses to cut back traceability.
PeckShieldAlert stories that the attacker has deposited the stolen quantities into the Twister Money cryptocurrency mixing service within the type of 1,337 ETH.
The Twister Money service, which was sanctioned by the U.S. in 2022 and delisted in 2025 for its function in laundering funds for North Korean hacking teams, permits customers to route cryptocurrency via obfuscation mechanisms earlier than withdrawing it to new, unlinkable wallets.
Whereas designed to offer transaction privateness on public blockchains, it has been abused by cybercriminals to evade regulation enforcement monitoring and asset-freezing efforts.
In response to the incident, Unleash Protocol has paused all operations and launched an investigation with the assistance of exterior safety specialists to find out the foundation reason for the exploit. On the identical time, they’re evaluating remediation and restoration measures.
Within the meantime, customers are suggested to not work together with Unleash Protocol contracts till the corporate publicizes publicly on its official channels that it’s protected to take action.
Damaged IAM is not simply an IT drawback – the impression ripples throughout your entire enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM seems to be like, and a easy guidelines for constructing a scalable technique.