
Google has launched emergency updates to repair a high-severity Chrome vulnerability exploited in zero-day assaults, marking the primary such safety flaw patched because the begin of the yr.
“Google is conscious that an exploit for CVE-2026-2441 exists within the wild,” Google stated in a safety advisory issued on Friday.
In line with the Chromium commit historical past, this use-after-free vulnerability (reported by safety researcher Shaheen Fazim) is because of an iterator invalidation bug in CSSFontFeatureValuesMap, Chrome’s implementation of CSS font characteristic values. Profitable exploitation can permit attackers to set off browser crashes, rendering points, information corruption, or different undefined conduct.
The commit message additionally notes that the CVE-2026-2441 patch addresses “the quick drawback” however signifies there’s “remaining work” tracked in bug 483936078, suggesting this is perhaps a short lived repair or that associated points nonetheless must be addressed.
The patch was tagged as “cherry-picked” (or backported) throughout a number of commits, indicating that it was essential sufficient to incorporate in a steady launch somewhat than ready for the following main model (seemingly as a result of the vulnerability is being exploited within the wild).
Though Google discovered proof of attackers exploiting this zero-day flaw within the wild, it didn’t share further particulars relating to these incidents.
“Entry to bug particulars and hyperlinks could also be saved restricted till a majority of customers are up to date with a repair. We may even retain restrictions if the bug exists in a 3rd celebration library that different initiatives equally depend upon, however have not but fastened,” it famous.
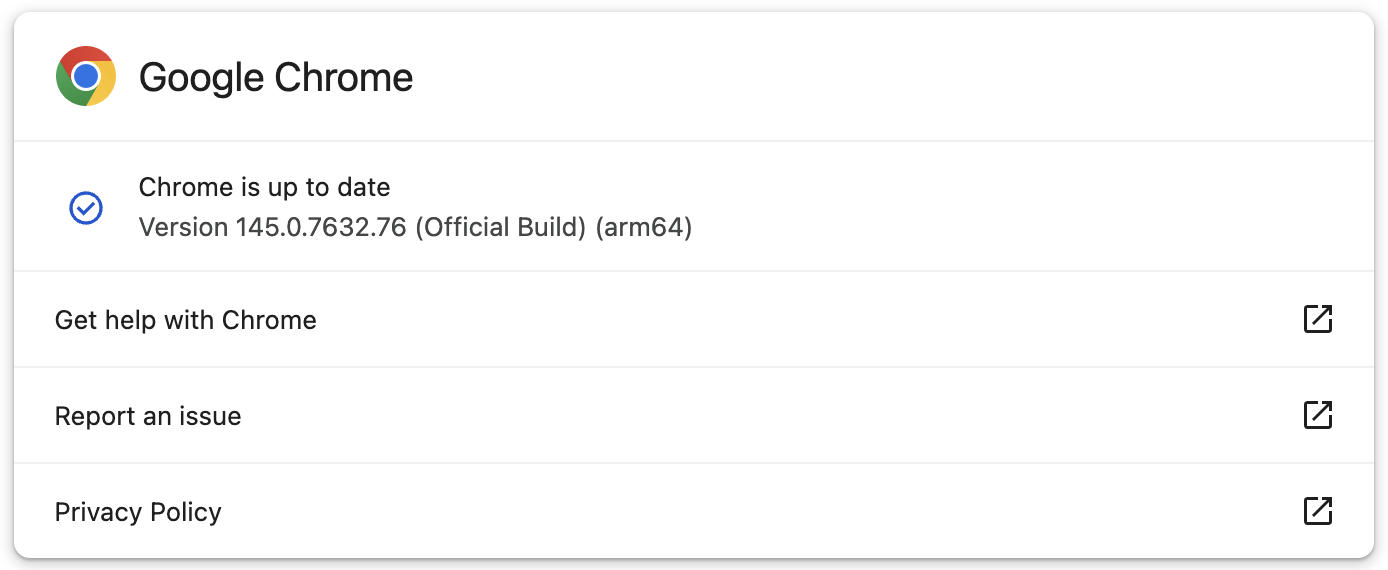
Google has now fastened this vulnerability for customers within the Secure Desktop channel, with new variations rolling out to Home windows, macOS (145.0.7632.75/76), and Linux customers (144.0.7559.75) worldwide over the approaching days or even weeks.
When you do not need to replace manually, you may also let Chrome examine for updates robotically and set up them after the following launch.
Whereas that is the primary actively exploited Chrome safety vulnerability patched because the begin of 2026, final yr Google addressed a complete of eight zero-days abused within the wild, a lot of them reported by the corporate’s Risk Evaluation Group (TAG), extensively recognized for monitoring and figuring out zero-days exploited in spyware and adware assaults focusing on high-risk people.
Fashionable IT infrastructure strikes sooner than handbook workflows can deal with.
On this new Tines information, find out how your workforce can scale back hidden handbook delays, enhance reliability by automated response, and construct and scale clever workflows on high of instruments you already use.




