This blogpost introduces our newest white paper, offered at Virus Bulletin 2025, the place we element the operations of the North Korea-aligned risk actor we name DeceptiveDevelopment and its connections to North Korean IT employee campaigns. The white paper offers full technical particulars, together with malware evaluation, infrastructure, and OSINT findings. Right here, we summarize the important thing insights and spotlight the broader implications of this hybrid risk.
Key factors of this blogpost:
- The invention and focus of the operations are on the social-engineering strategies.
- DeceptiveDevelopment’s toolset is generally multiplatform and consists of preliminary obfuscated malicious scripts in Python and JavaScript, fundamental backdoors in Python and Go, and a darkish internet venture in .NET.
- We offer insights into operational particulars of North Korean IT employees, like work assignments, schedules, communication with shoppers, and so forth., gathered from public sources.
- Native, extra advanced Home windows backdoors are an occasional addition within the execution chain and are seemingly shared by different North Korea-aligned actors.
- DeceptiveDevelopment and North Korean IT employees have completely different aims and means, however we take into account them as tightly linked.
Introduction
On this blogpost, we look at the DeceptiveDevelopment group and the WageMole exercise cluster as two tightly linked North Korea-aligned entities. WageMole is a label that now we have adopted for actions related to North Korean IT employees. Whereas the campaigns of each are pushed by monetary achieve, every performs a definite and complementary function in relation to the opposite:
- DeceptiveDevelopment operators pose as recruiters, utilizing fraudulent job affords to compromise the programs of job seekers.
- North Korean IT employees then use the data gained by the DeceptiveDevelopment operators to pose as job seekers. To safe an actual job place, they might make use of a number of techniques, together with proxy interviewing, utilizing stolen identities, and fabricating artificial identities with AI-driven instruments.
First, we offer a list of multiplatform instruments utilized by DeceptiveDevelopment, from easy however obfuscated scripts like BeaverTail and InvisibleFerret to a fancy toolkit, TsunamiKit, centered round a .NET backdoor. We additionally disclose particular hyperlinks between extra advanced backdoors utilized by DeceptiveDevelopment, AkdoorTea and Tropidoor, and different, extra APT-oriented North Korea-aligned operations. Subsequent, we describe attention-grabbing elements of North Korean IT employees’ modus operandi, obtained from public sources, largely from unintentionally uncovered knowledge, testimonials of victims, and investigations of unbiased researchers..
DeceptiveDevelopment
DeceptiveDevelopment is a North Korea-aligned group lively since not less than 2023, centered on monetary achieve. Its actions overlap with Contagious Interview, DEV#POPPER, and Void Dokkaebi. The group targets software program builders on all main programs – Home windows, Linux, and macOS – and particularly these in cryptocurrency and Web3 tasks. Preliminary entry is achieved completely through varied social engineering methods like ClickFix, and faux recruiter profiles much like Lazarus’s Operation DreamJob, to ship trojanized codebases throughout staged job interviews. Its most common payloads are the BeaverTail, OtterCookie, and WeaselStore infostealers, and the InvisibleFerret modular RAT.
Concentrating on technique
DeceptiveDevelopment operators use varied strategies to compromise their victims, counting on intelligent social engineering methods. By way of each faux and hijacked profiles, they pose as recruiters on platforms like LinkedIn, Upwork, Freelancer, and Crypto Jobs Record. They provide faux profitable job alternatives to draw their targets’ curiosity. Victims are requested to take part in a coding problem or a pre-interview activity. The duty entails downloading a venture from personal GitHub, GitLab, or Bitbucket repositories. These repositories comprise trojanized code, typically hidden cleverly in lengthy feedback displayed effectively past the right-hand fringe of a code browser or editor window. Participation within the activity triggers the execution of BeaverTail, the first-stage malware.
Apart from these faux recruiter accounts, the addition of a brand new social engineering approach often called ClickFix was noticed. ClickFix in relation to DeceptiveDevelopment was first reported by Sekoia.io in March 2025, when it was utilized by the group because the preliminary entry methodology on macOS and Home windows programs; in September 2025, GitLab noticed it getting used on Linux programs too. The attackers direct the sufferer to a faux job interview web site, containing an utility kind that they’re requested to finish. The applying kind comprises just a few prolonged questions associated to the applicant’s identification and {qualifications}, main the sufferer to place important effort and time into filling within the kind and making them really feel like they’re virtually executed, and due to this fact extra prone to fall for the entice. Within the ultimate step of the applying, the sufferer is requested to document a video of them answering the ultimate query. The positioning triggers a pop-up asking the sufferer to permit digicam entry, however the digicam is rarely truly accessed. As an alternative, an error message seems saying that entry to the digicam or microphone is at the moment blocked and affords a “The right way to repair” hyperlink. That hyperlink results in a pop-up using the ClickFix social engineering approach. The sufferer is instructed, based mostly on their working system, to open a terminal and replica and paste a command that ought to remedy the difficulty. Nevertheless, as an alternative of enabling the sufferer’s digicam, the command downloads and executes malware.
Toolset
BeaverTail and InvisibleFerret
The primary indication of DeceptiveDevelopment exercise got here in November 2023, when Unit 42 reported the Contagious Interview marketing campaign; we later related this marketing campaign with the group. Unit 42 coined the names BeaverTail and InvisibleFerret for the 2 malware households used on this marketing campaign. We documented this marketing campaign in additional element in our WeLiveSecurity blogpost from February 2025, dissecting how the risk actor makes use of those two malware households.
BeaverTail is a straightforward infostealer and downloader that collects knowledge from cryptocurrency wallets, keychains, and saved browser logins. We’ve noticed variants of this malware written in JavaScript, hidden in faux job challenges, and likewise in C++, utilizing the Qt framework and disguised as conferencing software program. Its major operate is downloading the second-stage malware InvisibleFerret. On the finish of 2024, a brand new malware household with performance much like BeaverTail emerged – it was named OtterCookie by NTT Safety. OtterCookie is written in JavaScript and makes use of very comparable obfuscation methods. We imagine that OtterCookie is an evolution of BeaverTail and is utilized by some groups inside DeceptiveDevelopment as an alternative of the older BeaverTail, whereas different groups proceed utilizing and modifying the unique codebase.
InvisibleFerret is modular malware written in Python with extra information-stealing capabilities than BeaverTail, additionally able to offering distant management to attackers. It normally comes with the next 4 modules:
- a browser-data stealer module (extracts and exfiltrates knowledge saved by browsers and cryptocurrency wallets),
- a payload module (distant entry trojan),
- a clipboard module (containing keylogging and clipboard logging capabilities) – in some instances distributed as a part of the payload module, and
- an AnyDesk module (which deploys the AnyDesk distant entry software to permit direct attacker entry to the compromised machine).
WeaselStore
As DeceptiveDevelopment advanced and began to incorporate extra groups in its operations, these groups began modifying the codebase to satisfy their very own wants and launched new malware tooling. One such instance is a marketing campaign that ESET researchers investigated in August 2024. Along with the traditional BeaverTail and InvisibleFerret malware, the workforce accountable for the marketing campaign deployed what we imagine is its personal new malware – which we named WeaselStore.
WeaselStore (additionally known as GolangGhost and FlexibleFerret) is a multiplatform infostealer written in Go, although in Might 2025, Cisco Talos reported about WeaselStore being rewritten in Python; they known as that malware PylangGhost. Because the implementation is equivalent, for simplicity, we check with each implementations as WeaselStore on this blogpost.
WeaselStore’s performance is sort of much like each BeaverTail and InvisibleFerret, with the principle focus being exfiltration of delicate knowledge from browsers and cryptocurrency wallets. As soon as the info has been exfiltrated, WeaselStore, in contrast to conventional infostealers, continues to speak with its C&C server, serving as a RAT able to executing varied instructions.
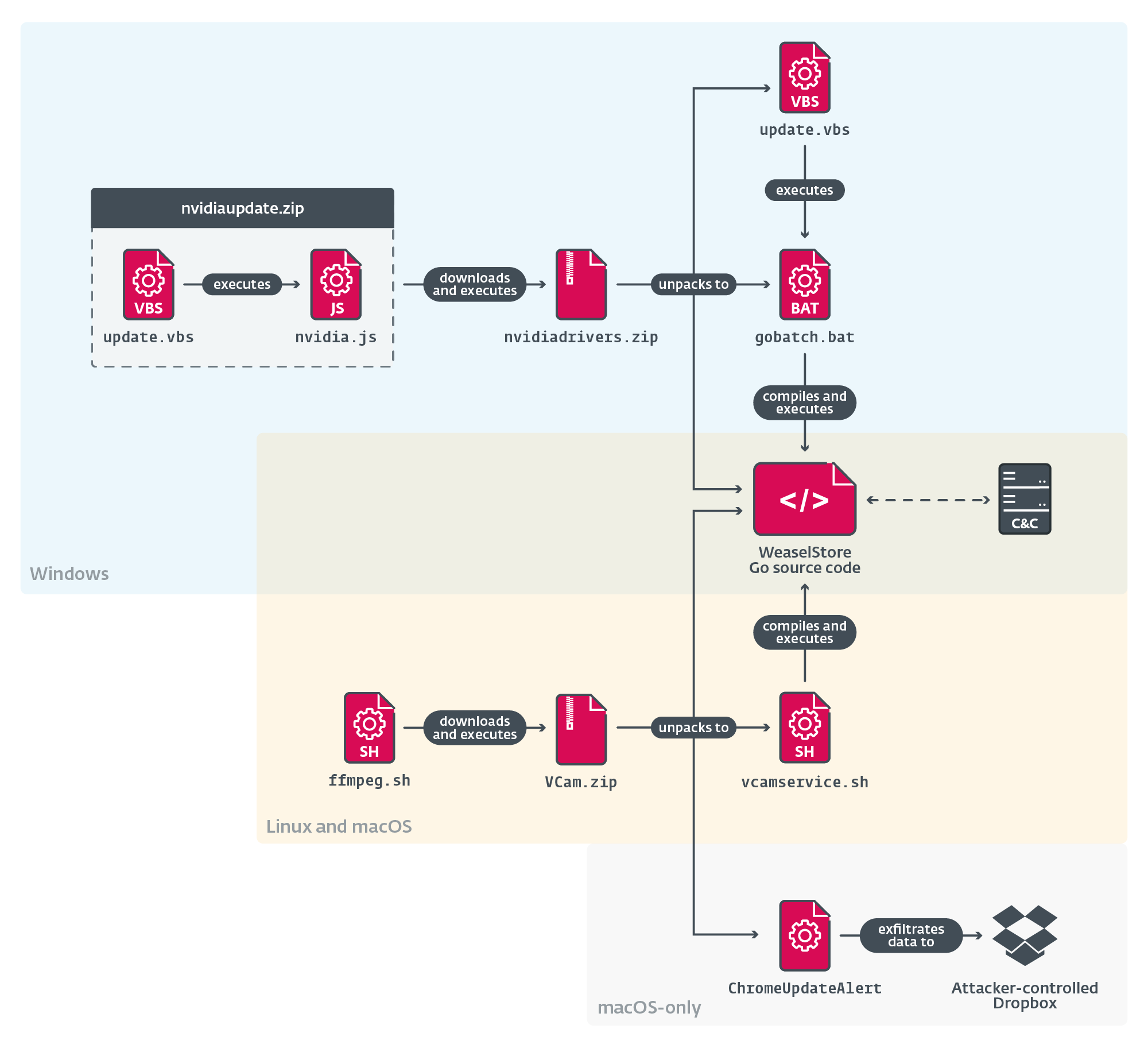
Essentially the most attention-grabbing side of WeaselStore in Go is that it’s delivered to the sufferer’s system within the type of Go supply code, together with the Go atmosphere binaries crucial to construct and execute it, permitting the malware to focus on three primary working programs – Home windows, Linux, and macOS (see Determine 1). The set up mechanism differs based mostly on the sufferer’s working system, however in all instances the chain ends with downloading the WeaselStore Go supply code after which compiling and executing it utilizing a Go construct atmosphere, which can also be offered alongside.
TsunamiKit
In November 2024, a brand new model of the InvisibleFerret malware delivered a modified browser-data stealer module. This module, along with its regular performance, comprises a beforehand unseen, giant, encoded block with the primary stage of the execution chain deploying a totally new malware toolkit, additionally supposed for info and cryptocurrency theft. We named this toolkit TsunamiKit, based mostly on the developer’s repeated use of “Tsunami” within the names of its parts (see Desk 1). The risk being publicly reported by Alessio Di Santo in November 2024 and by Bitdefender in February 2025; our white paper provides context by putting it within the total DeceptiveDevelopment modus operandi. The paper additionally dives into the small print of TsunamiKit’s advanced execution chain.
Desk 1. Elements of the TsunamiKit execution chain
| Element identify | Description |
| TsunamiLoader | The preliminary stage, obfuscating and dropping TsunamiInjector. It comprises a quote Typically you by no means know the worth of a second till it turns into a reminiscence, typically attributed to Dr. Seuss. |
| TsunamiInjector | Downloader of TsunamiInstaller. Additionally drops TsunamiHardener. |
| TsunamiHardener* | Known as TsunamiPayload within the code. Units up persistence for TsunamiClient, and Microsoft Defender exclusions for TsunamiClient and the XMRig miner (certainly one of TsunamiClient’s parts). |
| TsunamiInstaller | .NET dropper of TsunamiClientInstaller and a Tor proxy. |
| TsunamiClientInstaller* | Fingerprints the system; downloads and executes TsunamiClient. |
| TsunamiClient | Complicated .NET adware; drops XMRig and NBMiner. |
* These parts had been initially each named TsunamiPayload; now we have renamed them to keep away from any confusion.
PostNapTea and Tropidoor
Over the course of our analysis, we noticed an attention-grabbing piece of proof, additional linking DeceptiveDevelopment to North Korea. In April 2025, Ahnlab researchers reported about trojanized Bitbucket tasks containing BeaverTail and a 64‑bit downloader named automobile.dll or img_layer_generate.dll. Whereas BeaverTail, as anticipated, downloaded InvisibleFerret, this new downloader retrieved an in-memory payload that was named Tropidoor by Ahnlab. We realized that Tropidoor shares giant parts of code with PostNapTea, a Lazarus RAT distributed through exploitation towards South Korean targets in 2022. Desk 2 comprises a comparability of each payloads.
Desk 2. Comparability of Tropidoor (DeceptiveDevelopment) and PostNapTea (Lazarus) payloads (asterisks point out the nation of a VirusTotal submission)
| Tropidoor | PostNapTea | |
| First seen | 2024-11-28 | 2022-02-25 |
| Focused international locations | Kenya*, Colombia*, Canada* | South Korea |
| Preliminary Entry | Social engineering | Exploitation |
| Hash-based decision of Home windows APIs | Fowler–Noll–Vo | Fowler–Noll–Vo |
| String encryption | Plain + XOR-based | XOR-based |
| Encryption for community communication | Base64 + AES-128 | Base64 + AES-128 |
| Challenge | C DLL | MFC C++ DLL |
| Sort of instructions | Inside implementation of Home windows instructions | Inside implementation of Home windows instructions |
| Constructing atmosphere | Visible Studio 2019, v16.11 | Visible Studio 2017, v15.9 |
| Configuration format | Binary | JSON |
| Consumer-Agent (variations in reversed colour) | Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/112.0.0.0 Safari/537.36 Edg/112.0.1722.64 | Mozilla/5.0 (Home windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/91.0.4472.114 Safari/537.36 |
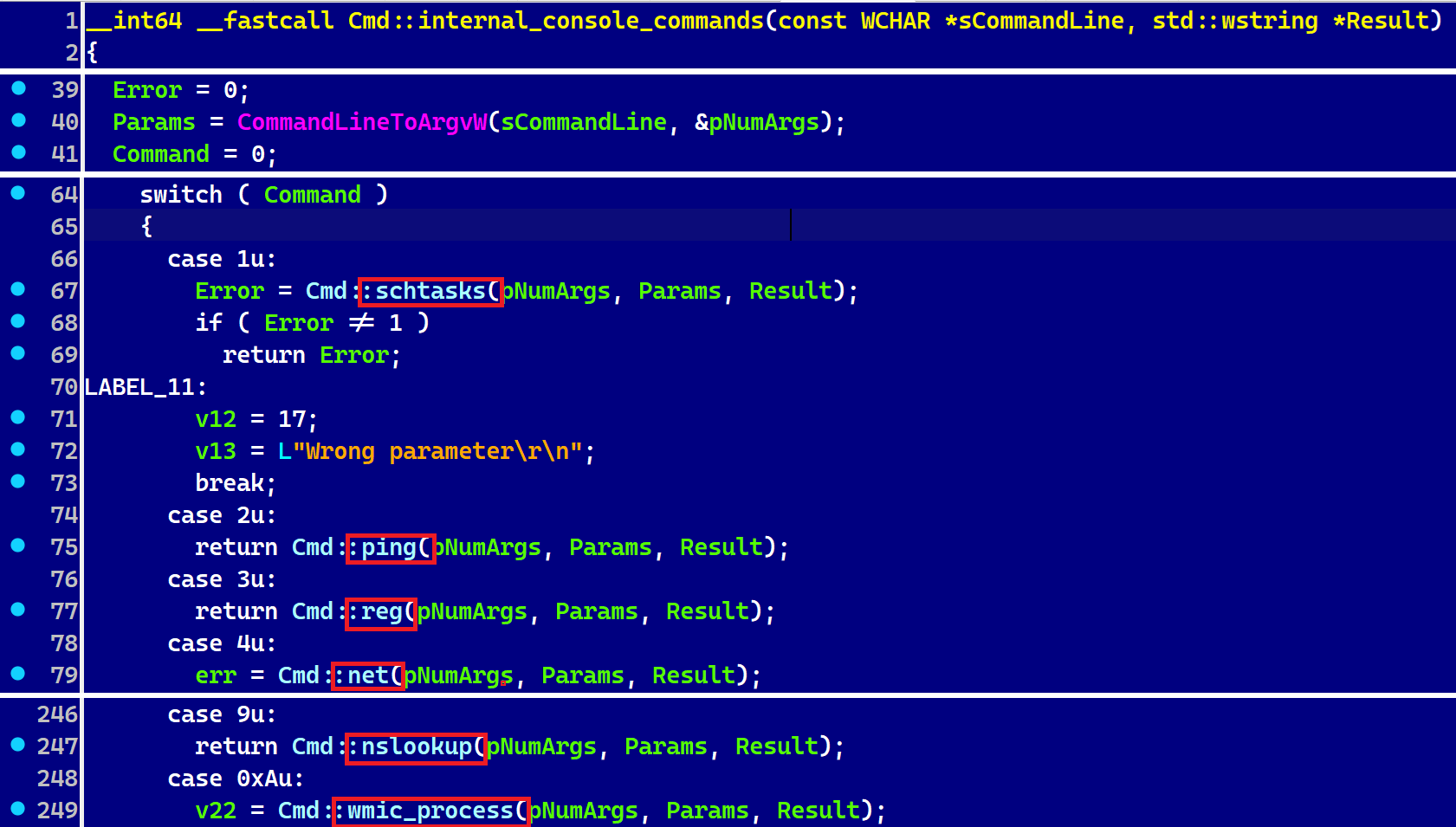
Tropidoor is probably the most subtle payload but linked to the DeceptiveDevelopment group, most likely as a result of it’s based mostly on malware developed by the extra technically superior risk actors below the Lazarus umbrella. A number of the supported instructions are proven in Determine 2.
New findings
Since our white paper’s submission, now we have uncovered new findings that additional strengthen the hyperlink between the exercise of DeceptiveDevelopment and different North Korea-aligned cyberattacks.
We found that the TsunamiKit venture dates again not less than to December 2021, when it was submitted to VirusTotal below the identify Nitro Labs.zip. One of many parts comprises the PDB path E:ProgrammingThe Tsunami ProjectMalwareC#C# Tsunami Dist Model 3.0.0CTsunamiobjReleasenetcoreapp3.1win-x64System Runtime Monitor.pdb. We conclude that TsunamiKit is probably going a modification of a darkish internet venture fairly than a brand new creation by the attackers, based mostly on TsunamiKit largely predating the approximate begin of DeceptiveDevelopment exercise in 2023, comparable TsunamiKit payloads with none indicators of BeaverTail having been noticed in ESET telemetry, and cryptocurrency mining being a core function of TsunamiKit.
AkdoorTea
In August 2025, a BAT file named ClickFix-1.bat and a ZIP archive named nvidiaRelease.zip had been uploaded to VirusTotal. The BAT file simply downloads the archive and executes run.vbs from it. The archive comprises varied reliable JAR packages for the NVIDIA CUDA Toolkit, along with the next malicious recordsdata:
- shell.bat, a trojanized installer for Node.js, which is executed afterward.
- primary.js, an obfuscated BeaverTail script, routinely loaded by Node.js.
- drvUpdate.exe, a TCP RAT, to which we assign the codename AkdoorTea, as it’s much like Akdoor reported by AlienVault in 2018 (see Desk 3). Akdoor is a detection root identify by Ahnlab and normally identifies a North Korea-aligned payload.
- run.vbs, a VBScript that executes the trojanized installer and AkdoorTea.
Desk 3. Comparability of variants of AkdoorTea and Akdoor
| AkdoorTea 2025 | Akdoor 2018 | |
| Distribution identify | drvUpdate.exe | splwow32.exe, MMDx64Fx.exe |
| Encryption | Base64 + XOR with 0x49 | Base64 + RC4 |
| Variety of supported instructions | 5 | 4 |
| C&C | 103.231.75[.]101 | 176.223.112[.]74 164.132.209[.]191 |
| Model | 01.01 | 01.01 |
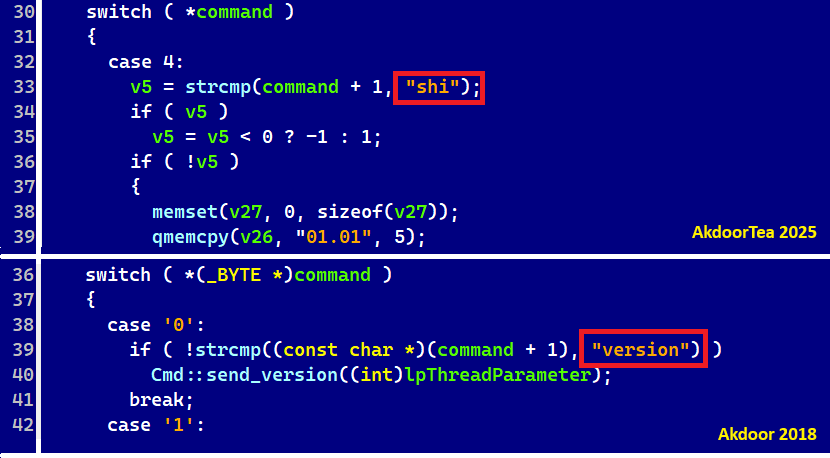
One of many variations between AkdoorTea from 2025 and Akdoor from 2018 is the numbering of instructions; see Determine 3. Additionally, the command identify “model” is named “shi” now.
North Korean IT employees (aka WageMole)
Whereas our analysis into DeceptiveDevelopment is based totally on knowledge from our telemetry and reverse-engineering the group’s toolset, it’s attention-grabbing to level out DeceptiveDevelopment’s relations to fraud operations by North Korean IT employees, overlapping with the exercise of the UNC5267 and Jasper Sleet risk teams.
IT employee campaigns have been ongoing since not less than April 2017, in keeping with an FBI wished poster, and have been more and more outstanding in recent times. A joint advisory launched in Might 2022 describes IT employee campaigns as a coordinated effort by North Korea-aligned people to achieve employment at abroad corporations, whose salaries are then used to assist fund the nation. They’ve additionally been recognized to steal inside firm knowledge and use it to extort corporations, as said in an announcement by the FBI in January 2025.
Along with utilizing AI to carry out their job duties, they rely closely on AI for manipulating photographs of their profile photos and CVs, and even carry out face swaps in real-time video interviews to seem like the persona they’re at the moment utilizing, as described in additional element in a blogpost by Unit 42 in April 2025.
A methodological perception was offered by a DTEX report in Might 2025. The IT employees reportedly function in a scattered method, with quite a few groups of employees, normally based mostly in international international locations like China, Russia, and international locations in Southeast Asia. Every workforce works in a barely completely different method, however their finish objectives and modus operandi are the identical – posing as international distant employees with faux paperwork and CVs, and in search of distant employment or freelance work to assemble funds from the salaries.
Analyzing OSINT knowledge
A number of researchers have noticed ties and situations of knowledge change between these IT employees and DeceptiveDevelopment. In August 2024, the cybersecurity researcher Heiner García printed an investigation of how each teams share e-mail accounts or are mutually adopted between the GitHub profiles of pretend recruiters and IT employees. In November 2024, Zscaler confirmed that identities stolen from compromised victims are utilized by scammers to safe distant jobs. This leads us to claim with medium confidence that though these actions are performed by two completely different teams, they’re probably linked and collaborating.
Moreover, we managed to assemble publicly obtainable knowledge detailing the interior workings of a number of the IT employee groups. We gathered this info from a number of sources (with important assist from @browsercookies on X), amongst them GitHub profiles belonging to the IT employees, containing publicly accessible inside knowledge and content material shared publicly by researchers. These embrace particulars of their work assignments, schedules, communication with shoppers and one another, emails, varied photos used for on-line profiles (each actual and faux), faux CVs, and textual content templates used when job searching; resulting from info sharing agreements, we’re not disclosing the precise sources of the info utilized in our evaluation. We dive into these particulars in our white paper, and supply a compact abstract beneath.
Evaluation of pretend CVs and inside supplies reveals that IT employees initially focused jobs within the US, however have just lately shifted focus to Europe, together with France, Poland, Ukraine, and Albania.
Every workforce is led by a “boss” who units quotas and coordinates work. Members spend 10–16 hours each day buying jobs, finishing duties, and self-educating – primarily in internet programming, blockchain, English, and AI integration.
They meticulously monitor their work and use faux identities, CVs, and portfolios to use for jobs. Communication with employers follows scripted responses to look certified.
Moreover, they use premade scripts to recruit actual folks as proxies, providing them a share of the wage to attend interviews or host work gadgets in much less suspicious international locations. In a single case, Ukrainian builders had been focused resulting from perceived hiring benefits.
Conclusion
DeceptiveDevelopment’s TTPs illustrate a extra distributed, volume-driven mannequin of its operations. Regardless of typically missing technical sophistication, the group compensates by way of scale and inventive social engineering. Its campaigns exhibit a realistic strategy, exploiting open-source tooling, reusing obtainable darkish internet tasks, adapting malware most likely rented from different North Korea-aligned teams, and leveraging human vulnerabilities by way of faux job affords and interview platforms.
The actions of North Korean IT employees represent a hybrid risk. This fraud-for-hire scheme combines classical felony operations, resembling identification theft and artificial identification fraud, with digital instruments, which classify it as each a standard crime and a cybercrime (or eCrime). Proxy interviewing poses a extreme threat to employers, since an illegitimate worker employed from a sanctioned nation might not solely be irresponsible or underperforming, however may additionally evolve right into a harmful insider risk.
Our findings additionally spotlight the blurred traces between focused APT exercise and cybercrime, notably within the overlap between malware campaigns by DeceptiveDevelopment and the operations of North Korean IT employees. These dual-use techniques – combining cybertheft and cyberespionage with non-cyberspace employment-fraud schemes – underscore the necessity for defenders to contemplate broader risk ecosystems fairly than remoted campaigns..
For any inquiries about our analysis printed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis affords personal APT intelligence studies and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
Recordsdata
A complete listing of indicators of compromise (IoCs) and samples will be present in our GitHub repository.
| SHA-1 | Filename | Detection | Description |
| E34A43ACEF5AF1E5197D | nvidiadrivers | WinGo/DeceptiveDeve | A trojanized venture containing WeaselStore. |
| 3405469811BAE511E62C | VCam1.replace | WinGo/DeceptiveDeve | A trojanized venture containing WeaselStore. |
| C0BAA450C5F3B6AACDE2 | VCam2.replace | WinGo/DeceptiveDeve | A trojanized venture containing WeaselStore. |
| DAFB44DA364926BDAFC7 | nvidia.js | JS/Spy.DeceptiveDeve | WeaselStore downloader for Home windows. |
| 015583535D2C8AB710D1 | ffmpeg.sh | OSX/DeceptiveDeve | WeaselStore downloader for OSX/Linux. |
| CDA0F15C9430B6E0FF1A | DriverMinUpdate | OSX/DeceptiveDeve | Pretend immediate requesting consumer’s login on macOS. |
| 214F0B10E9474F0F5D32 | nvidiaupdate | WinGo/DeceptiveDeve | Compiled WeaselStore binary for Home windows. |
| 4499C80DDA6DBB492F86 | bow | Python/DeceptiveDeve | InvisibleFerret. |
| B20BFBAB8BA732D428AF | N/A | Python/DeceptiveDeve | Browser-data stealer module of InvisibleFerret. |
| C6888FB1DE8423D9AEF9 | Home windows Replace | Python/TsunamiKit.A | TsunamiInjector. |
| 4AAF0473599D7E3A5038 | Runtime Dealer | MSIL/DeceptiveDeve | TsunamiInstaller. |
| 251CF5F4A8E73F8C5F91 | Tsunami Payload | MSIL/DeceptiveDeve | TsunamiClientInstaller. |
| D469D1BAA3417080DED7 | Tsunami Payload | MSIL/DeceptiveDeve | TsunamiClient. |
| 0C0F8152F3462B662318 | Runtime Dealer | Win64/Riskware.Tor.A | Tor Proxy. |
| F42CC34C1CFAA826B962 | autopart.zip | Win64/DeceptiveDeve JS/Spy.DeceptiveDeve | A trojanized venture containing BeaverTail and a downloader of Tropidoor. |
| 02A2CD54948BC0E2F696 | hoodygang.zip | Win64/DDeceptiveDeve JS/Spy.DeceptiveDeve | A trojanized venture containing BeaverTail and a downloader of Tropidoor. |
| 6E787E129215AC153F3A | tailwind.con | JS/Spy.DeceptiveDeve | A trojanized JavaScript containing BeaverTail. |
| FE786EAC26B61743560A | tailwind.con | JS/Spy.DeceptiveDeve | A trojanized JavaScript containing BeaverTail. |
| 86784A31A2709932FF10 | img_layer_gen | Win64/DeceptiveDeve | A downloader of the Tropidoor RAT. |
| 90378EBD8DB757100A83 | N/A | Win64/DeceptiveDeve | Tropidoor RAT. |
| C86EEDF02B73ADCE0816 | drivfixer.sh | OSX/DeceptiveDeve | A trojanized macOS installer and launcher of Node.js. |
| 4E4D31C559CA16F8B7D4 | ClickFix-1 | PowerShell/Decepti | An preliminary stage on Home windows: BAT downloading a malicious nvidiaRelease.zip archive. |
| A9C94486161C07AE6935 | driv.zip | JS/Spy.DeceptiveDeve OSX/DeceptiveDeve | A ZIP archive containing BeaverTail. |
| F01932343D7F13FF1094 | nvidiaRelease | JS/Spy.DeceptiveDeve Win32/DeceptiveDeve VBS/DeceptiveDeve BAT/DeceptiveDeve | A ZIP archive containing BeaverTail and AkdoorTea. |
| BD63D5B0E4F2C72CCFBF | mac-v-j1722 | OSX/DeceptiveDeve | An preliminary stage on macOS: a bash script that downloads a malicious driv.zip archive. |
| 10C967386460027E7492 | primary.js | JS/Spy.DeceptiveDeve | An obfuscated BeaverTail script, routinely loaded by Node.js. |
| 59BA52C644370B4D627F | run.vbs | VBS/DeceptiveDeve | A VBScript that executes AkdoorTea and shell.bat. |
| 792AFE735D6D356FD30D | drvUpdate.exe | Win32/DeceptiveDeve | AkdoorTea, a TCP RAT. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 199.188.200[.]147 | driverservice | Namecheap, Inc. | 2025‑08‑08 | Distant storage for DeceptiveDevelopment. |
| 116.125.126[.]38 | www.royalsevr | SK Broadband Co Ltd | 2024‑06‑25 | Distant storage for DeceptiveDevelopment. |
| N/A | n34kr3z26f3jz | N/A | 2023‑10‑06 | TsunamiClient C&C server. |
| 103.231.75[.]101 | N/A | THE-HOSTING-MNT | 2025‑08‑10 | AkdoorTea C&C server. |
| 45.159.248[.]110 | N/A | THE-HOSTING-MNT | 2025‑06‑29 | BeaverTail C&C server. |
| 45.8.146[.]93 | N/A | STARK INDUSTRIES SOLUTIONS LTD | 2024‑10‑26 | Tropidoor C&C server. |
| 86.104.72[.]247 | N/A | STARK INDUSTRIES SOLUTIONS LTD | 2024‑10‑31 | Tropidoor C&C server. |
| 103.35.190[.]170 | N/A | STARK INDUSTRIES SOLUTIONS LTD | 2024‑06‑24 | Tropidoor C&C server. |
MITRE ATT&CK methods
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Identify | Description |
| Reconnaissance | T1589 | Collect Sufferer Identification Data | DeceptiveDevelopment steals victims’ credentials for use by WageMole in consequent social engineering. |
| Useful resource Improvement | T1585.001 | Set up Accounts: Social Media Accounts | Pretend recruiter accounts created on LinkedIn, Upwork, Freelancer.com, and so forth. |
| T1586 | Compromise Accounts | Hijacked GitHub and social media accounts used to distribute malware. | |
| Preliminary Entry | T1566.001 | Phishing: Spearphishing Attachment | Pretend job affords embrace attachments or hyperlinks to malicious tasks. |
| T1566.002 | Phishing: Spearphishing Hyperlink | ClickFix approach makes use of misleading hyperlinks to faux troubleshooting guides. | |
| Execution | T1204.001 | Consumer Execution: Malicious Hyperlink | Victims are lured to faux job interview websites (e.g., ClickFix) that provoke malware obtain. |
| T1204.002 | Consumer Execution: Malicious File | Trojanized coding challenges comprise variants of BeaverTail. | |
| T1059 | Command and Scripting Interpreter | DeceptiveDevelopment makes use of VBS, Python, JavaScript, and shell instructions for execution. | |
| Protection Evasion | T1078 | Legitimate Accounts | WageMole reuses stolen identities and credentials, particularly for faux recruiter and GitHub accounts. |
| T1027 | Obfuscated Recordsdata or Data | Obfuscated malicious scripts are hidden in lengthy feedback or outdoors IDE view. | |
| T1055 | Course of Injection | TsunamiKit makes use of injection methods in its execution chain. | |
| T1036 | Masquerading | Malware disguised as reliable software program (e.g., conferencing instruments, NVIDIA installers). | |
| T1497 | Virtualization/Sandbox Evasion | TsunamiKit contains atmosphere checks and obfuscation to evade evaluation. | |
| Assortment | T1056.001 | Enter Seize: Keylogging | InvisibleFerret contains clipboard and keylogging modules. |
| Command and Management | T1071.001 | Software Layer Protocol: Net Protocols | AkdoorTea, BeaverTail, and Tropidoor talk with C&C servers over HTTP/S. |
| T1105 | Ingress Device Switch | BeaverTail downloads second-stage payloads like InvisibleFerret, TsunamiKit, or Tropidoor. |



