
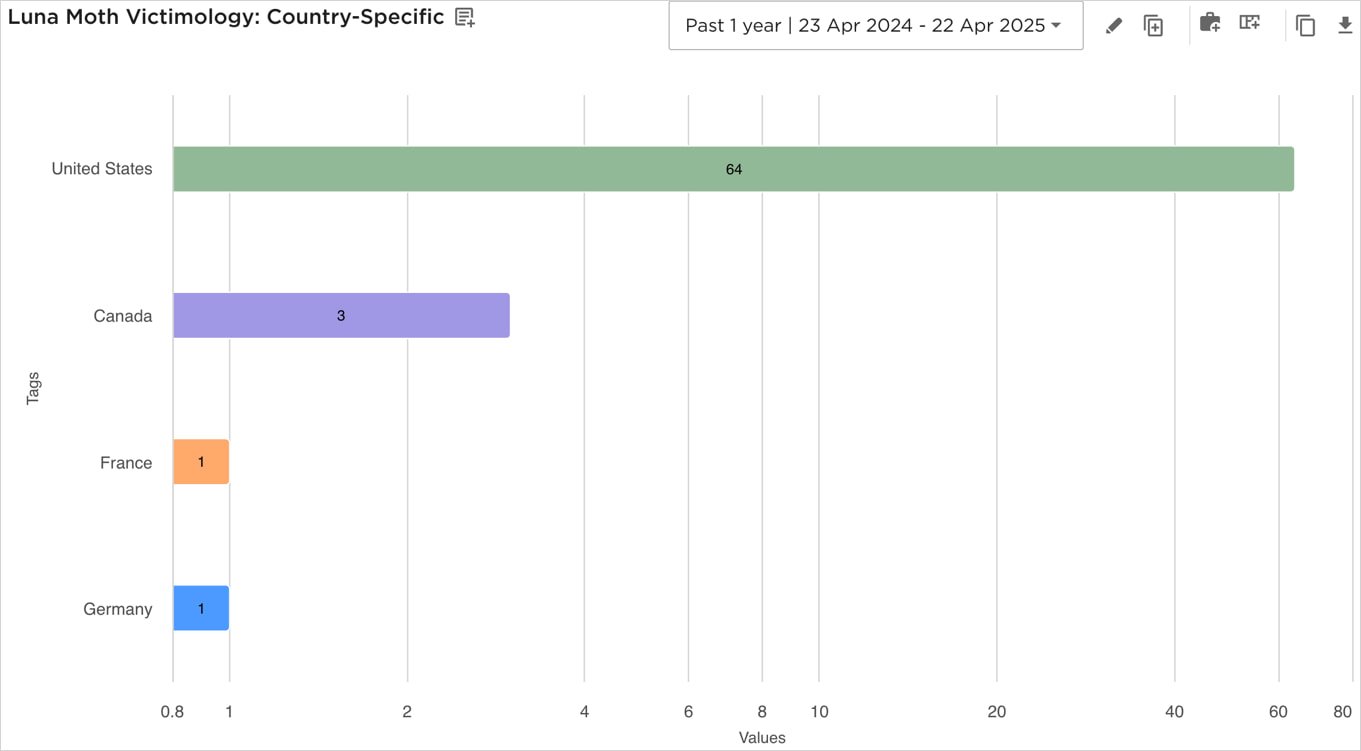
The FBI warned that an extortion gang generally known as the Silent Ransom Group has been concentrating on U.S. legislation companies during the last two years in callback phishing and social engineering assaults.
Also referred to as Luna Moth, Chatty Spider, and UNC3753, this risk group has been lively since 2022 and was additionally behind BazarCall campaigns that supplied preliminary entry to company networks for Ryuk and Conti ransomware assaults.
In March 2022, following Conti’s shutdown, the risk actors separated from the cybercrime syndicate and shaped their very own operation known as Silent Ransom Group (SRG).
In latest assaults, SRG impersonates the targets’ IT assist in e mail, pretend websites, and telephone calls utilizing social engineering ways to realize entry to the targets’ networks.
This extortion group does not encrypt the victims’ methods and is thought for demanding ransoms to not leak delicate data stolen from compromised gadgets on-line.
“SRG will then direct the worker to hitch a distant entry session, both by an e mail despatched to them, or navigating to an online web page. As soon as the worker grants entry to their machine, they’re instructed that work must be achieved in a single day,” the FBI mentioned in a personal business notification on Friday.
“As soon as within the sufferer’s machine, a typical SRG assault entails minimal privilege escalation and shortly pivots to information exfiltration performed by ‘WinSCP’ (Home windows Safe Copy) or a hidden or renamed model of ‘Rclone.'”
After stealing the victims’ information, they extort them by way of ransom emails, threatening to promote or publish the knowledge, and so they’ll additionally name staff of breached organizations to strain them into ransom negotiations. Whereas they’ve a devoted web site the place they’re leaking their victims’ information, the FBI says the extortion gang does not all the time observe up on their information leak threats.
To defend towards their assaults, the FBI advises utilizing strong passwords, enabling two-factor authentication for all staff, making common information backups, and conducting employees coaching on detecting phishing makes an attempt.
FBI’s warning follows a latest EclecticIQ report detailing SRG assaults concentrating on authorized and monetary establishments in the USA, with the attackers being noticed registering domains to “impersonate IT helpdesk or assist portals for main U.S. legislation companies and monetary companies companies, utilizing typosquatted patterns.”
Victims are being despatched malicious emails with pretend helpdesk numbers, urging them to name to resolve numerous non-existent issues. Nevertheless, Luna Moth operators impersonating IT employees on the opposite finish will try to trick focused corporations’ staff into putting in distant monitoring & administration (RMM) software program from pretend IT assist desk websites.
As soon as the RMM software is put in and launched, the risk actors achieve hands-on keyboard entry, which permits them to search for invaluable paperwork on compromised gadgets and shared drivers that will probably be later exfiltrated utilizing Rclone (cloud syncing) or WinSCP (by way of SFTP).
In keeping with EclecticIQ, ransom calls for despatched by the Silent Ransom Group vary between one and eight million USD, relying on the breached firm’s measurement.



