
Hackers over the previous six months have relied more and more extra on the browser-in-the-browser (BitB) technique to trick customers into offering Fb account credentials.
The BitB phishing approach was developed by safety researcher mr.d0x in 2022. Cybercriminals later adopted it in assaults focusing on numerous on-line providers, together with Fb and Steam.
Trellix researchers monitoring malicious exercise say that risk actors steal Fb accounts to unfold scams, harvest private knowledge, or commit id fraud. With greater than three billion energetic customers, the social community continues to be a main goal for fraudsters.
In a BitB assault, customers who go to attacker-controlled webpages are introduced with a faux browser pop-up containing a login type.
The pop-up is applied utilizing an iframe that imitates the authentication interface of authentic platforms and may be custom-made with a window title and URL that make the deception harder to detect.
In accordance with Trellix, current phishing campaigns focusing on Fb customers impersonate regulation companies claiming copyright infringement, threatening imminent account suspension, or Meta safety notifications about unauthorized logins.
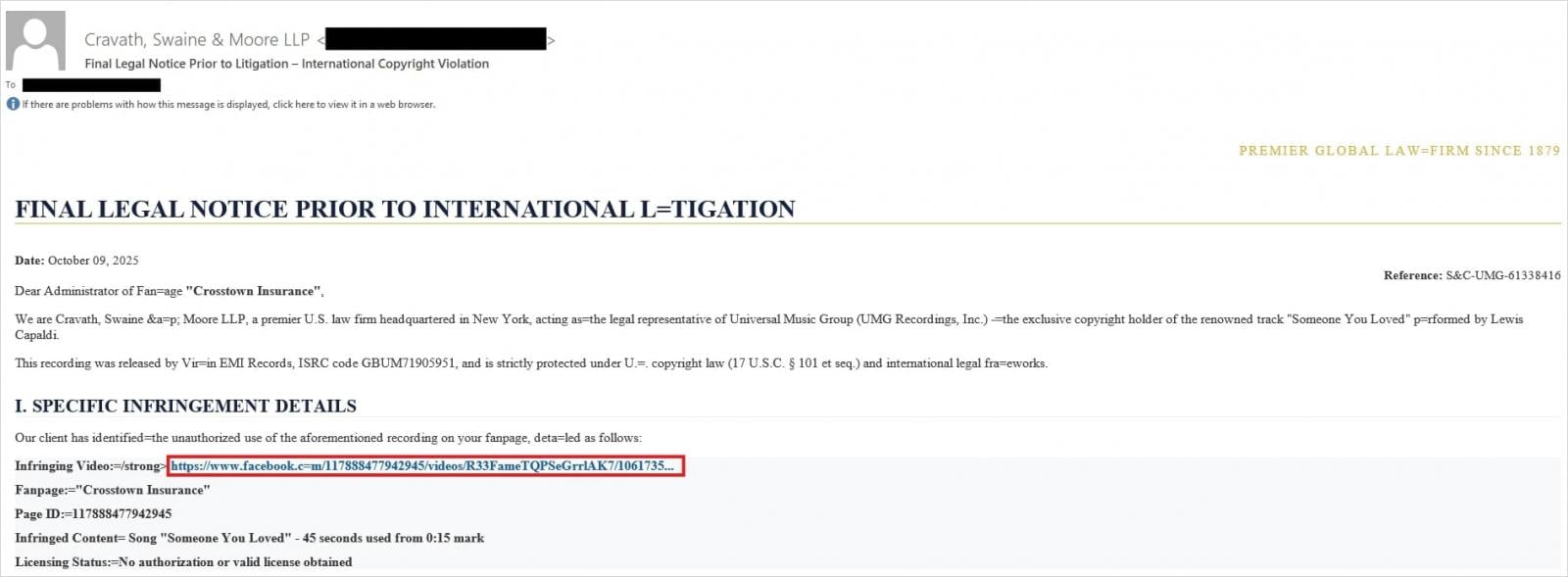
Supply: Trellix
To keep away from detection and to extend the sense of legitimacy, cybercriminals added shortened URLs and faux Meta CAPTCHA pages.
Within the last stage of the assault, victims are prompted to log in by coming into their Fb credentials in a faux pop-up window.
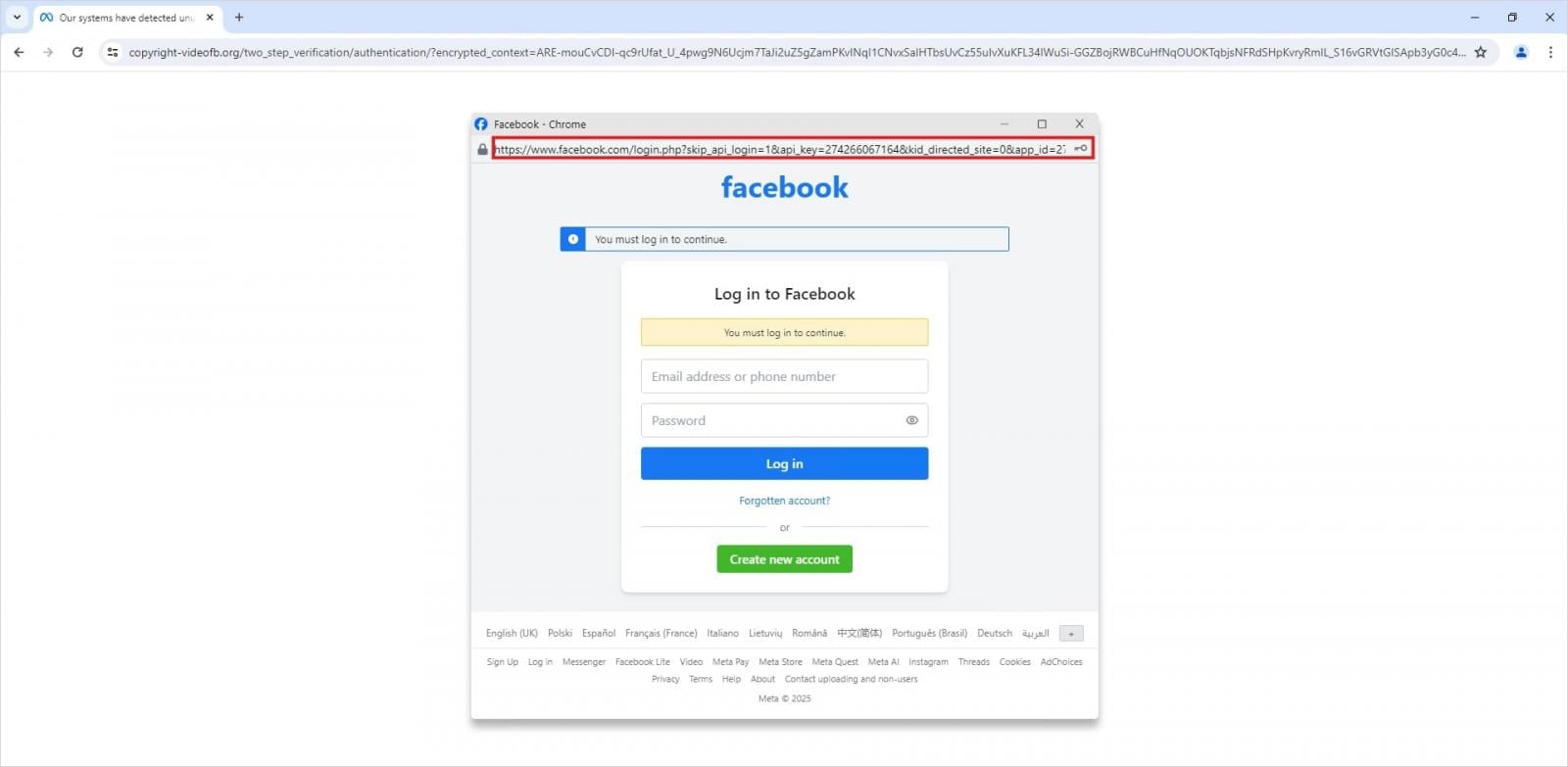
Supply: Trellix
In parallel, Trellix found a excessive variety of phishing pages hosted on authentic cloud platforms like Netlify and Vercel, which mimic Meta’s Privateness Middle portal, redirecting customers to pages disguised as enchantment types that collected private info.
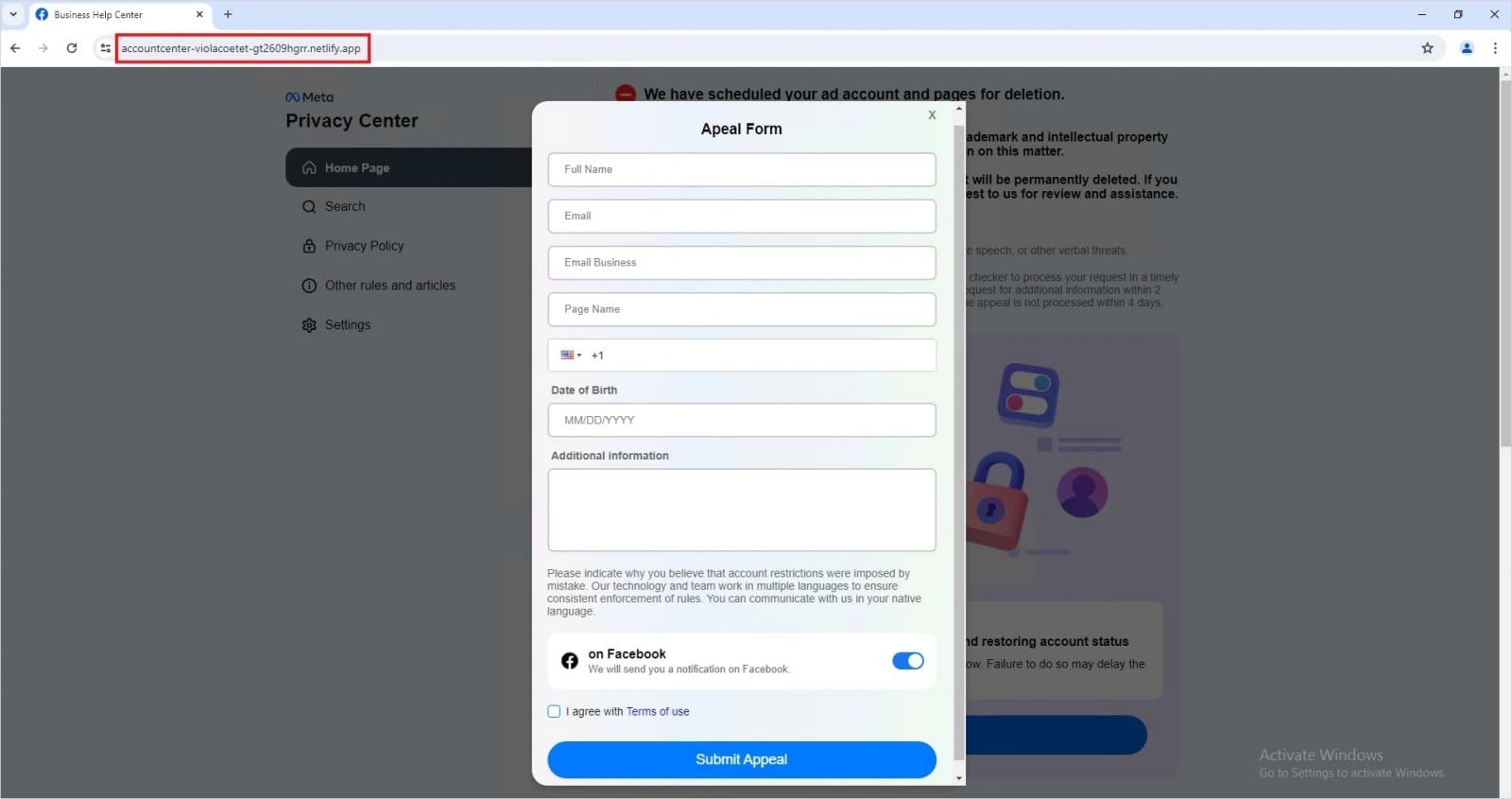
Supply: Trellix
These campaigns represent a big evolution in comparison with commonplace Fb phishing campaigns that safety researchers sometimes observe.
“The important thing shift lies within the abuse of trusted infrastructure, using authentic cloud internet hosting providers like Netlify and Vercel, and URL shorteners to bypass conventional safety filters and lend a false sense of safety to phishing pages,” reads the Trellix report.
“Most critically, the emergence of the Browser-in-the-Browser (BitB) approach represents a significant escalation. By making a custom-built, faux login pop-up window inside the sufferer’s browser, this technique capitalizes on person familiarity with authentication flows, making credential theft practically inconceivable to detect visually.”
Easy methods to shield towards BitM
When customers obtain account-related safety alerts or infringement notifications, they need to all the time navigate to the official URL in a separate tab as an alternative of following embedded hyperlinks or buttons on the e-mail itself.
When prompted to enter credentials in login pop-ups, test if the window can transfer outdoors the browser window. iframes, that are important for the BitB trick, are related to the underlying window and can’t be pulled outdoors it.
The overall suggestion for safeguarding entry to your on-line accounts is to activate the two-factor authentication safety characteristic. Though not infallible, this provides an additional layer of safety towards account takeover makes an attempt even when credentials have been compromised.




