
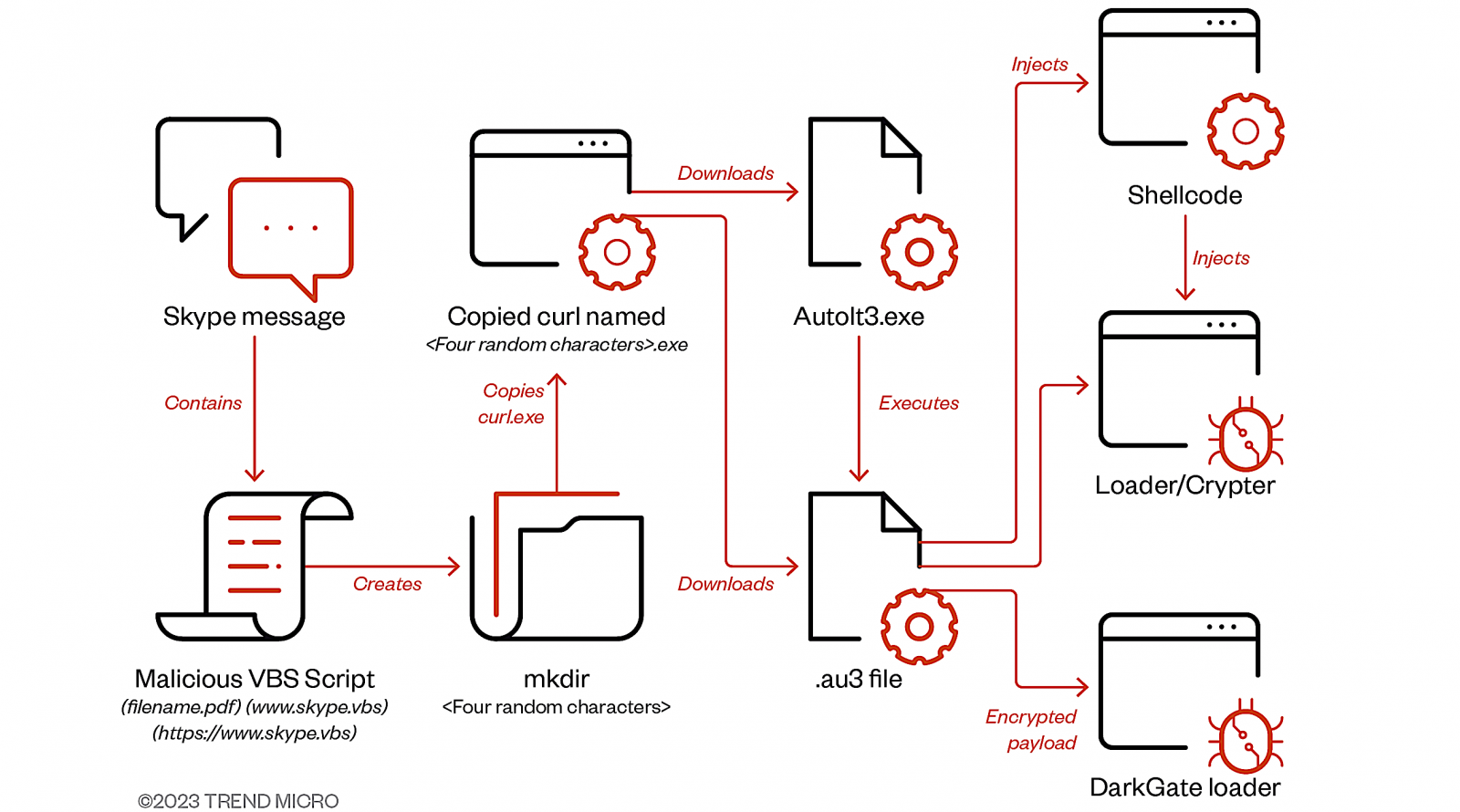
Between July and September, DarkGate malware assaults have used compromised Skype accounts to contaminate targets by way of messages containing VBA loader script attachments.
In keeping with Development Micro safety researchers who noticed the assaults, this script downloads a second-stage AutoIT script designed to drop and execute the ultimate DarkGate malware payload.
“Entry to the sufferer’s Skype account allowed the actor to hijack an current messaging thread and craft the naming conference of the information to narrate to the context of the chat historical past,” Development Micro mentioned.
“It is unclear how the originating accounts of the moment messaging purposes had been compromised, nonetheless is hypothesized to be both by way of leaked credentials obtainable by way of underground boards or the earlier compromise of the father or mother group,”
Development Micro additionally noticed the DarkGate operators attempting to push their malware payload by way of Microsoft Groups in organizations the place the service was configured to simply accept messages from exterior customers.
Groups phishing campaigns utilizing malicious VBScript to deploy DarkGate malware had been beforehand noticed by Truesec and MalwareBytes.
As they defined, malicious actors focused Microsoft Groups customers through compromised Workplace 365 accounts exterior their organizations and a publicly obtainable software named TeamsPhisher. This software allows attackers to bypass restrictions for incoming information from exterior tenants and ship phishing attachments to Groups customers.
“The objective remains to be to penetrate the entire surroundings, and relying on the menace group that purchased or leased the DarkGate variant used, the threats can fluctuate from ransomware to cryptomining,” Development Micro mentioned.
“From our telemetry, we’ve seen DarkGate resulting in tooling being detected generally related to the Black Basta ransomware group.”
DarkGate malware surge
Cybercriminals have more and more adopted the DarkGate malware loader for preliminary entry into company networks, a development noticed because the disruption of the Qakbot botnet in August on account of worldwide collaborative efforts.
Earlier than Qakbot’s dismantling, a person purporting to be DarkGate’s developer tried to promote subscriptions on a hacking discussion board, quoting an annual charge of as much as $100,000.
The malware was touted to supply a big selection of options, together with a hid VNC, capabilities to bypass Home windows Defender, a browser historical past theft software, an built-in reverse proxy, a file supervisor, and a Discord token stealer.
Following this announcement, there’s been a noticeable uptick in stories documenting DarkGate infections through varied supply strategies, similar to phishing and malvertising.
This latest surge in DarkGate exercise underscores the rising affect of this malware-as-a-service (MaaS) operation inside the cybercriminal sphere.
It additionally emphasizes the menace actors’ dedication to proceed their assaults, adapting their ways and strategies regardless of disruptions and challenges.


