A number of vital vulnerabilities within the in style n8n open-source workflow automation platform permit escaping the confines of the setting and taking full management of the host server.
Collectively tracked as CVE-2026-25049, the problems might be exploited by any authenticated consumer who can create or edit workflows on the platform to carry out unrestricted distant code execution on the n8n server.
Researchers at a number of cybersecurity corporations reported the issues, which stem from n8n’s sanitization mechanism and bypass the patch for CVE-2025-68613, one other vital flaw addressed on December 20.
In keeping with Pillar Safety, exploiting CVE-2026-25049 allows full compromise of the n8n occasion and might be leveraged to run arbitrary system instructions on the server, steal all saved credentials, secrets and techniques (API keys, OAuth tokens), and delicate configuration recordsdata.
By exploiting the vulnerability, the researchers have been additionally in a position to entry the filesystem and inside programs, pivot to linked cloud accounts, and hijack AI workflows (intercept prompts, modify responses, redirect site visitors).
As n8n is a multi-tenant setting, accessing inside cluster companies can probably permit pivoting to different tenants’ knowledge.
“The assault requires nothing particular. If you happen to can create a workflow, you’ll be able to personal the server,” Pillar Safety says in a report at this time.
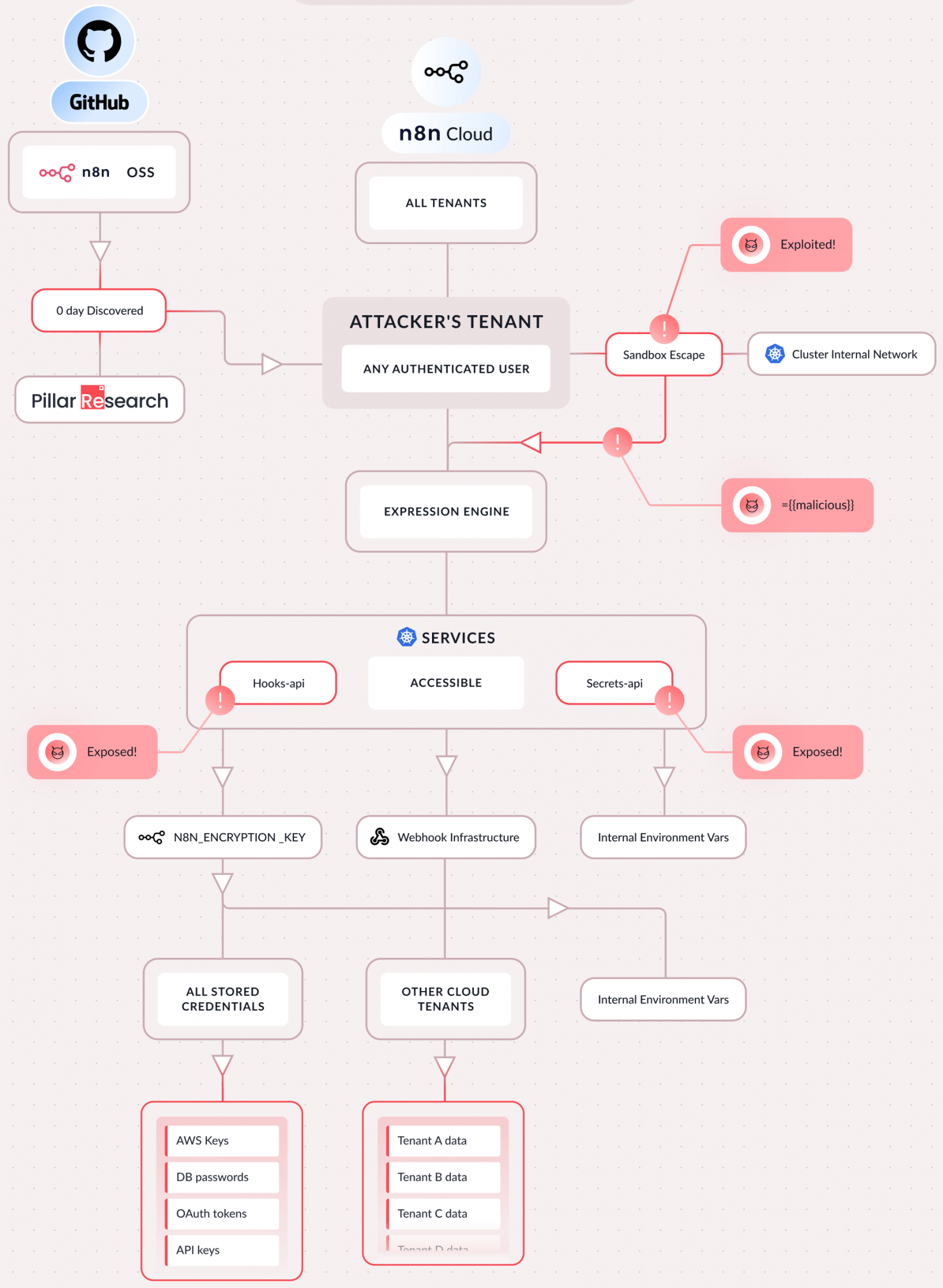
Supply: Pillar Safety
Pillar’s report describes the issue as incomplete AST-based sandboxing and explains that it arises from n8n’s weak sandboxing of user-written server-side JavaScript expressions in workflows.
On December 21, 2025, they demonstrated a chained bypass to the n8n group, permitting sandbox escape and entry to the Node.js international object, resulting in RCE.
A repair was carried out two days later, however upon additional evaluation, Pillar discovered it incomplete, and a second escape through a unique mechanism utilizing equal operations remained potential.
n8n builders confirmed the bypass on December 30, and ultimately, n8n launched model 2.4.0 on January 12, 2026, addressing the problem.
Researchers at Endor Labs additionally found sanitization bypasses and demonstrated the CVE-2026-25049 vulnerability with a easy proof-of-concept (PoC) exploit that achieves distant code execution.
“In all variations previous to 2.5.2 and 1.123.17, the sanitization operate assumes keys in property accesses are strings in attacker-controlled code,” says Cristian Staicu of Endor Labs.
Nonetheless, whereas the examine is mirrored in TypeScript typings, it isn’t enforced at runtime, introducing a type-confusion vulnerability. This results in bypassing the “sanitization controls completely, enabling arbitrary code execution assaults.”
In a report at this time, researchers at SecureLayer7 present the technical particulars that enabled them to obtain “server facet JavaScript execution utilizing the Perform constructor.”
They found CVE-2026-25049 whereas analyzing CVE-2025-68613 and n8n’s repair for it. It took greater than 150 failed makes an attempt to refine a profitable bypass.
SecureLayer7’s report additionally features a PoC exploit and detailed steps for the preliminary setup and making a malicious workflow that results in full server management.
Really useful steps
n8n customers ought to replace the platform to the newest model (presently 1.123.17 and a couple of.5.2). Pillar safety additionally recommends rotating the ‘N8N_ENCRYPTION_KEY’ and all credentials saved on the server, and reviewing workflows for suspicious expressions.
If updating just isn’t potential for the time being, the n8n group offers directors with a workaround, which acts as a short-term mitigation and doesn’t fully handle the danger:
- Restrict workflow creation and enhancing permissions to totally trusted customers solely
- Deploy n8n in a hardened setting with restricted working system privileges and community entry to scale back the impression of potential exploitation
At the moment, there haven’t been any public experiences about CVE-2026-25049 being exploited. Nonetheless, n8n’s rising recognition seems to have caught the eye of cybercriminals within the context of the Ni8mare flaw (CVE-2026-21858).
GreyNoise this week reported seeing probably malicious exercise focusing on uncovered n8n endpoints susceptible to Ni8mare, logging at the very least 33,000 requests between January 27 and February 3.
Though this probing might be because of analysis exercise, scanning for the /proc filesystem signifies curiosity in post-exploitation potential.
Fashionable IT infrastructure strikes sooner than guide workflows can deal with.
On this new Tines information, find out how your group can cut back hidden guide delays, enhance reliability by means of automated response, and construct and scale clever workflows on high of instruments you already use.




