
A menace actor generally known as Zestix has been providing to promote company knowledge stolen from dozens of firms seemingly after breaching their ShareFile, Nextcloud, and OwnCloud cases.
In accordance with cybercrime intelligence firm Hudson Rock, preliminary entry could have been obtained by means of credentials collected by info-stealing malware similar to RedLine, Lumma, and Vidar deployed on worker gadgets.
The three infostealers are normally distributed by means of malvertising campaigns or ClickFix assaults. Such a malware generally targets knowledge saved by internet browsers (credentials, bank cards, private data), messaging apps, and cryptocurrency wallets.
A menace actor with legitimate credentials can achieve unauthorized entry to a service, similar to a file-sharing platforms, when multi-factor authentication (MFA) safety is lacking.
In a report at the moment, Hudson Rock notes that a number of the analyzed stolen credentials have been current in prison databases for years, indicating failure to rotate them or to invalidate energetic periods even after prolonged durations.
A number of breaches marketed
Hudson Rock says that Zestix operates as an preliminary entry dealer (IAB) on underground boards, promoting entry to high-value company cloud platforms.
The cybersecurity firm counsel that attackers breached ShareFile, Nextcloud, and ownCloud environments utilized by organizations throughout a number of sectors, together with aviation, protection, healthcare, utilities, mass transit, telecommunications, authorized, actual property, and authorities.
Supply: Hudson Rock
After parsing infostealer logs “particularly in search of company cloud URLs (ShareFile, Nextcloud),” the menace actor logs into the file-sharing providers utilizing a sound username and password the place MFA shouldn’t be energetic.
Hudson Rock says it pinpointed the seemingly breach factors by correlating infostealer knowledge from its platform with publicly obtainable photos, metadata, and open-source info.
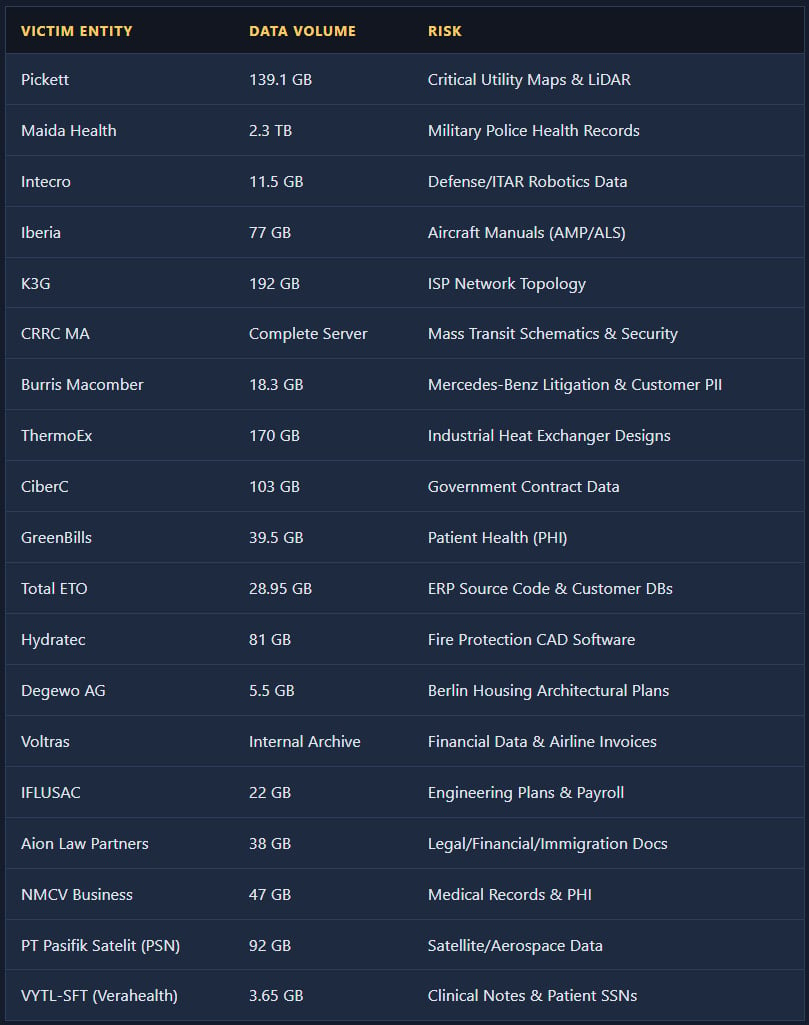
In no less than 15 of the analyzed circumstances, the cybersecurity firm discovered that worker credentials for the cloud file-sharing providers had been collected by infostealers.
You will need to word that this verification is unilateral, and there’s no public affirmation of a safety breach from the listed firms. One exception could possibly be Iberia, though its latest disclosure is not essentially linked to Hudson Rock’s findings.
Zestix supplied to promote stolen knowledge volumes that vary from tens of gigabytes to a number of terabytes, claiming to incorporate plane upkeep manuals and fleet knowledge, protection and engineering information, buyer databases, well being information, mass-transit schematics, utility LiDAR maps, ISP community configs, satellite tv for pc challenge knowledge, ERP supply code, authorities contracts, and authorized paperwork.
Most of the allegedly stolen information might expose organizations to safety, privateness, and industrial espionage dangers, whereas uncovered authorities contracts could elevate nationwide safety issues.
Supply: Hudson Rock
Hudson Rock has discovered a further set of 30 victims that Zestix sells underneath the alias “Sentap,” however the researchers didn’t validate it in the identical method.
The researchers report that, along with the listed victims, their menace intelligence knowledge signifies that cloud publicity is a broader, systemic drawback stemming from organizations’ failure to comply with good safety practices.
They report having recognized hundreds of contaminated computer systems, together with some at Deloitte, KPMG, Samsung, Honeywell, and Walmart.
Hudson Rock informed BleepingComputer that it has notified ShareFile and also will alert Nextcloud and OwnCloud concerning the verified exposures to allow them to take the suitable motion.




