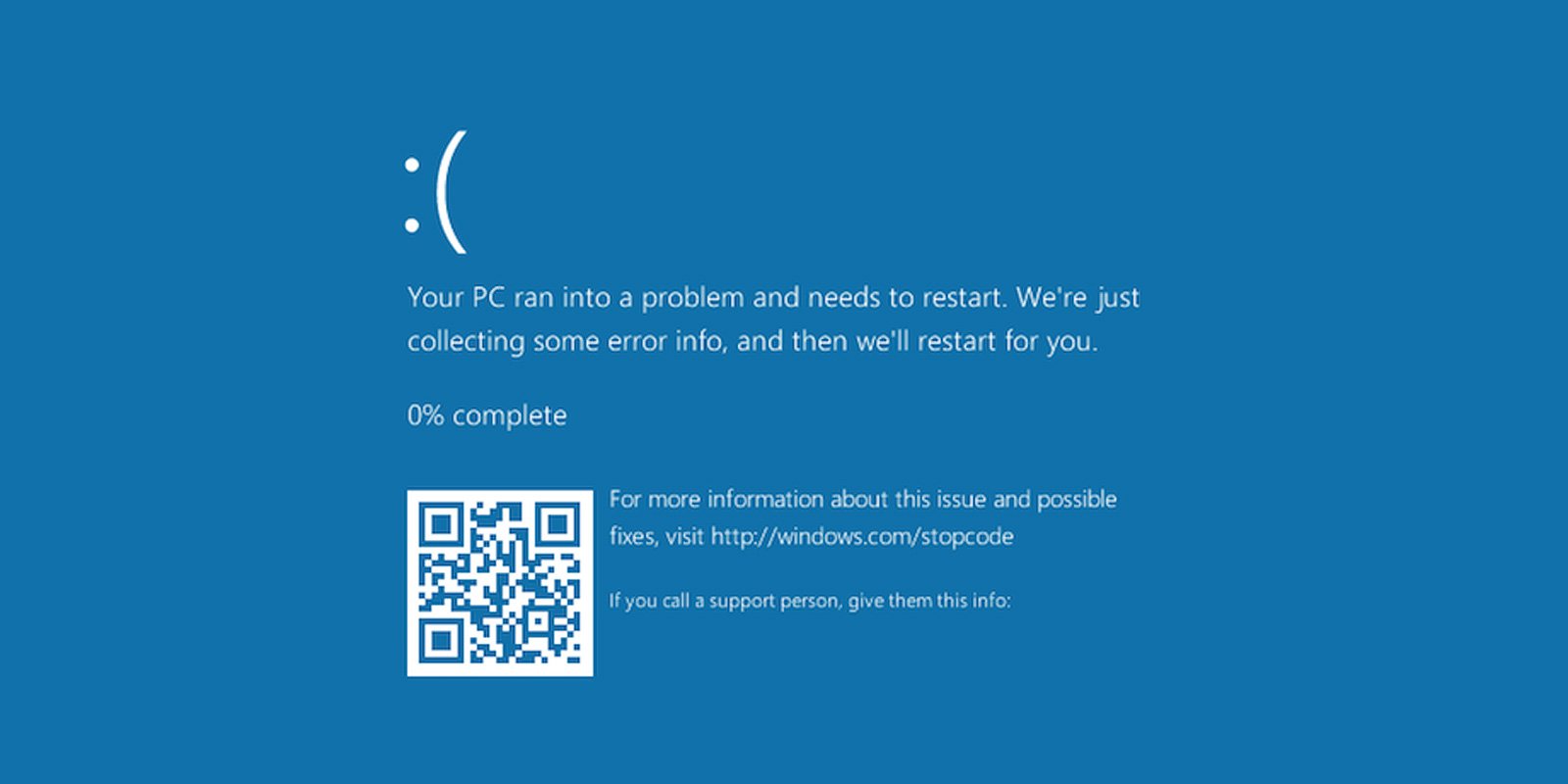
A brand new ClickFix social engineering marketing campaign is concentrating on the hospitality sector in Europe, utilizing pretend Home windows Blue Display screen of Dying (BSOD) screens to trick customers into manually compiling and executing malware on their programs.
A BSOD is a Home windows crash display screen displayed when the working system encounters a deadly, unrecoverable error that causes it to halt.
In a brand new marketing campaign first noticed in December and tracked by researchers at Securonix as “PHALT#BLYX,” phishing emails impersonating Reserving.com led to a ClickFix social engineering assault that deployed malware.
ClickFix assault impersonated BSOD crashes
ClickFix social engineering assaults are webpages designed to show an error or subject after which supply “fixes” to resolve it. These errors might be pretend error messages, safety warnings, CAPTCHA challenges, or replace notices that instruct guests to run a command on their laptop to repair the problem.
Victims find yourself infecting their very own machines by operating malicious PowerShell or shell instructions supplied within the attacker’s directions.
On this new ClickFix marketing campaign, attackers ship phishing emails that impersonate a resort visitor cancelling their Reserving.com reservation, usually despatched to a hospitality agency. The claimed refund quantity is important sufficient to create a way of urgency for the recipient of the e-mail.
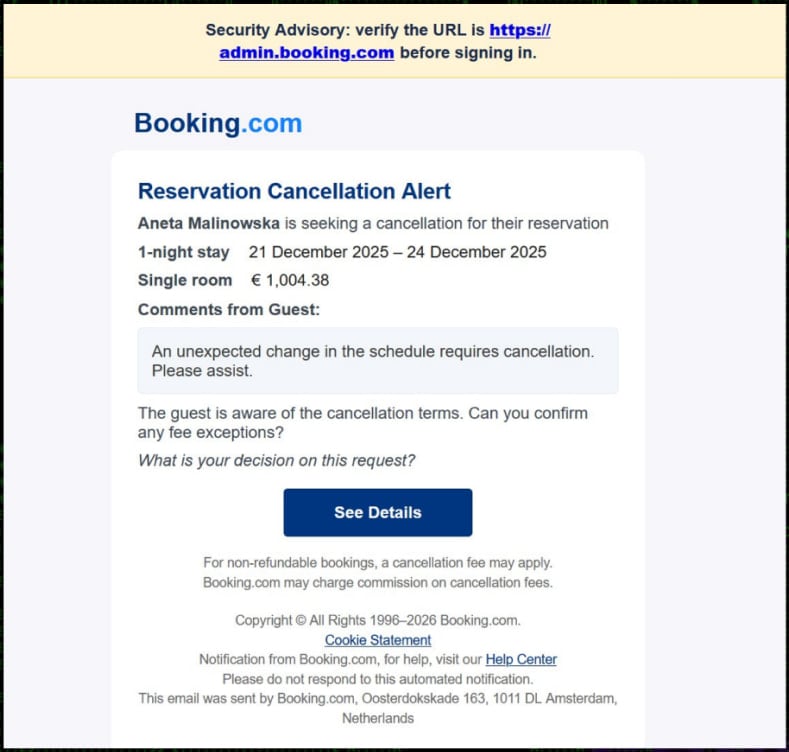
Supply: Securonix
Clicking the hyperlink within the e mail takes the sufferer to a pretend Reserving.com web site hosted on ‘low-house[.]com,’ which Securonix characterizes as a “high-fidelity clone” of the true Reserving.com web site.
“The web page makes use of official Reserving.com branding, together with the proper shade palette, logos, and font kinds. To the untrained eye, it’s indistinguishable from the legit web site,” experiences Securonix.
The positioning hosts malicious JavaScript that shows a pretend “Loading is taking too lengthy” error to the goal, prompting them to click on a button to refresh the web page.
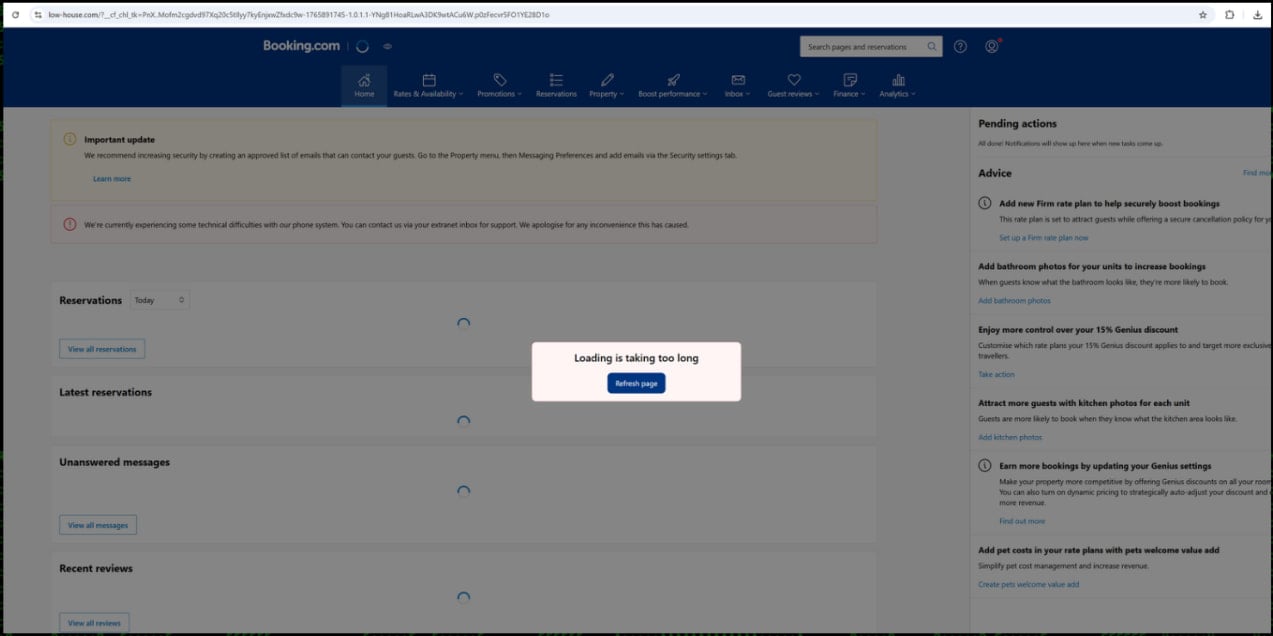
Supply: Securonix
Nonetheless, when the goal clicks the button, the browser as a substitute enters full-screen mode and shows a pretend Home windows BSOD crash display screen that initiates the ClickFix social engineering assault.
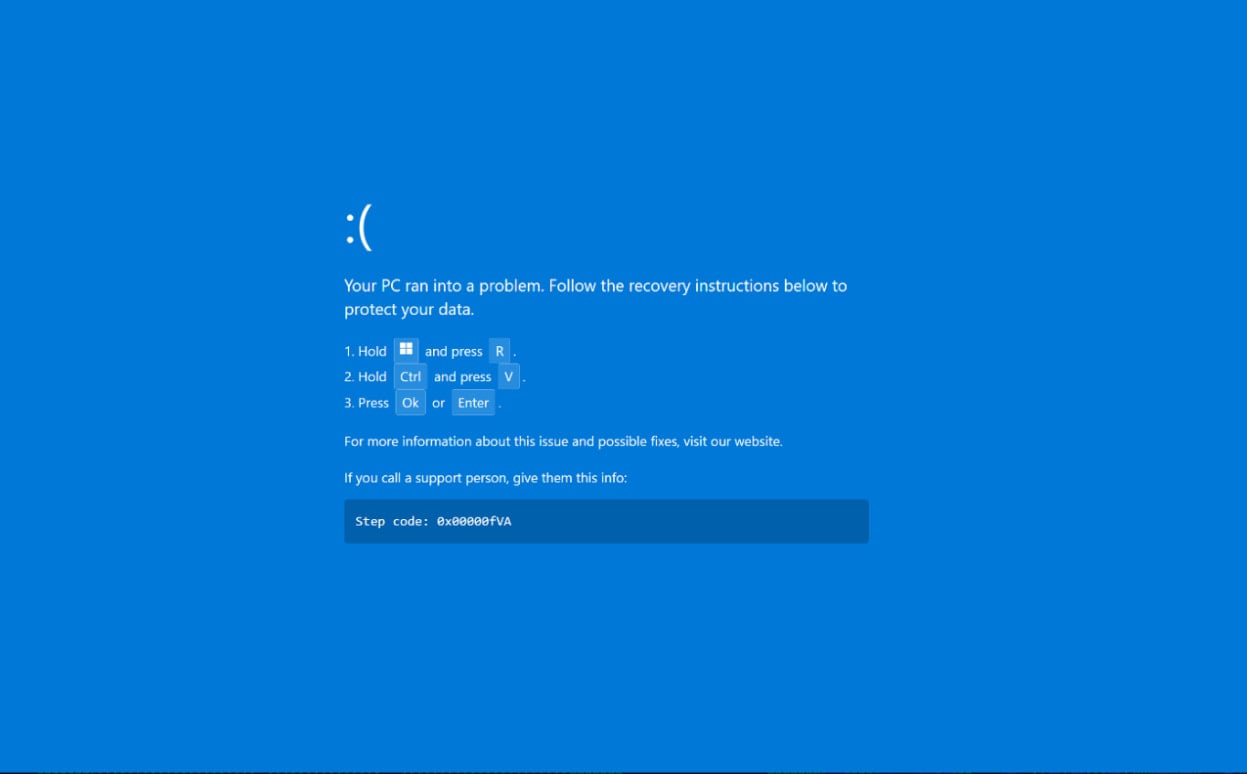
Supply: Securonix
The display screen prompts the particular person to open the Home windows Run dialog field after which press CTRL+V, which pastes a malicious command copied to the Home windows clipboard.
The person is then prompted to press the OK button or Enter on their keyboard to execute the command.
Actual BSOD messages don’t supply restoration directions and solely show an error code and a reboot discover, however inexperienced customers or hospitality employees beneath stress to resolve a dispute might overlook these indicators of trickery.
Pasting the supplied command runs a PowerShell command that opens a decoy Reserving.com admin web page. On the similar time, within the background, it downloads a malicious .NET mission (v.proj) and compiles it with the legit Home windows MSBuild.exe compiler.
When executed, the payload provides Home windows Defender exclusions and triggers UAC prompts to achieve admin rights, earlier than it downloads the first loader utilizing the Background Clever Switch Service (BITS) and establishes persistence by dropping a .url file within the Startup folder.
The malware (staxs.exe) is DCRAT, a distant entry Trojan generally utilized by risk actors for distant entry to contaminated gadgets.
The malware is injected into the legit ‘aspnet_compiler.exe’ course of utilizing course of hollowing and executed immediately in reminiscence.
Upon first contact with the command-and-control (C2) server, the malware sends its full system fingerprint after which waits for instructions to execute.
It helps distant desktop performance, keylogging, reverse shell, and in-memory execution of further payloads. Within the case noticed by Securonix, the attackers dropped a cryptocurrency miner.
With distant entry established, the risk actors now have a foothold on the goal’s community, permitting them to unfold to different gadgets, steal information, and doubtlessly compromise different programs.




