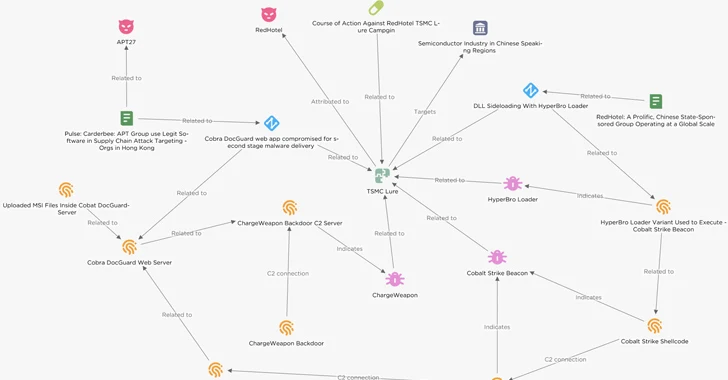
Menace actors have been noticed concentrating on semiconductor firms in East Asia with lures masquerading as Taiwan Semiconductor Manufacturing Firm (TSMC) which can be designed to ship Cobalt Strike beacons.
The intrusion set, per EclecticIQ, leverages a backdoor known as HyperBro, which is then used as a conduit to deploy the industrial assault simulation software program and post-exploitation toolkit.
An alternate assault sequence is alleged to have utilized a beforehand undocumented malware downloader to deploy Cobalt Strike, indicating that the risk actors devised a number of approaches to infiltrate targets of curiosity.
The Dutch cybersecurity agency attributed the marketing campaign to a China-linked risk actor owing to the usage of HyperBro, which has been nearly solely put to make use of by a risk actor often known as Fortunate Mouse (aka APT27, Budworm, and Emissary Panda).
Tactical overlaps have additionally been unearthed between the adversary behind the assaults and one other cluster tracked by RecordedFuture underneath the identify RedHotel, which additionally overlaps with a hacking crew known as Earth Lusca.
One other Chinese language connection comes from the usage of a possible compromised Cobra DocGuard internet server to host second-stage binaries, together with a Go-based implant dubbed ChargeWeapon, for distribution through the downloader.
“ChargeWeapon is designed to get distant entry and ship gadget and community info from an contaminated host to an attacker managed [command-and-control] server,” EclecticIQ researcher Arda Büyükkaya stated in a Thursday evaluation.
It is value noting {that a} trojanized model of EsafeNet’s Cobra DocGuard encryption software program has additionally been linked to the deployment of PlugX, with Symantec linking it to a suspected China-nexus actor codenamed Carderbee.
Within the assault chain documented by EclecticIQ, a TSMC-themed PDF doc is displayed as a decoy following the execution of HyperBro, indicating the usage of social engineering strategies to activate the an infection.
“By presenting a traditional trying PDF whereas covertly operating malware within the background, the probabilities of the sufferer rising suspicious are minimized,” Büyükkaya defined.
A notable side of the assault is that the C2 server tackle hard-coded into the Cobalt Strike beacon is disguised as a legit jQuery CDN in an effort to bypass firewall defenses.
The disclosure comes because the Monetary Instances reported that Belgium’s intelligence and safety company, the State Safety Service (VSSE), is working to “detect and struggle towards attainable spying and/or interference actions carried out by Chinese language entities together with Alibaba” on the nation’s Liège cargo airport.
Alibaba has denied any wrongdoing.
“China’s actions in Belgium will not be restricted to the basic spy stealing state secrets and techniques or the hacker paralyzing a vital business or authorities division from behind his PC,” the company famous in an intelligence report. “In an try to affect decision-making processes, China makes use of a variety of state and non-state sources.”
A report launched by the U.S. Division of Protection (DoD) final month described China as posing a “broad and pervasive cyber espionage risk,” and that it steals expertise secrets and techniques and undertakes surveillance efforts to realize a strategic benefit.
“Utilizing cyber means, the PRC has engaged in extended campaigns of espionage, theft, and compromise towards key protection networks and broader U.S. crucial infrastructure, particularly the Protection Industrial Base (DIB),” DoD stated.