Hackers partaking in cyber espionage have focused Chinese language-speaking semiconductor corporations with TSMC-themed lures that infect them with Cobalt Strike beacons.
Taiwan Semiconductor Manufacturing Firm (TSMC) is the world’s largest semiconductor contract manufacturing and design agency, with an annual income of $73.5 billion and over 73,000 staff worldwide.
The marketing campaign noticed by EclecticIQ focuses on companies based mostly in Taiwan, Hong Kong, and Singapore, with the noticed TTPs (ways, strategies, and procedures) bearing similarities to earlier actions linked to Chinese language state-backed risk teams.
Deploying Cobalt Strike
Eclectic’s report doesn’t specify the preliminary compromise channel, however it’s presumed to be spear-phishing emails, a typical method utilized in cyber espionage operations.
On this marketing campaign, the risk actors distribute the HyperBro loader to put in a Cobalt Strike beacon on the compromised system, offering distant entry to the risk actors.
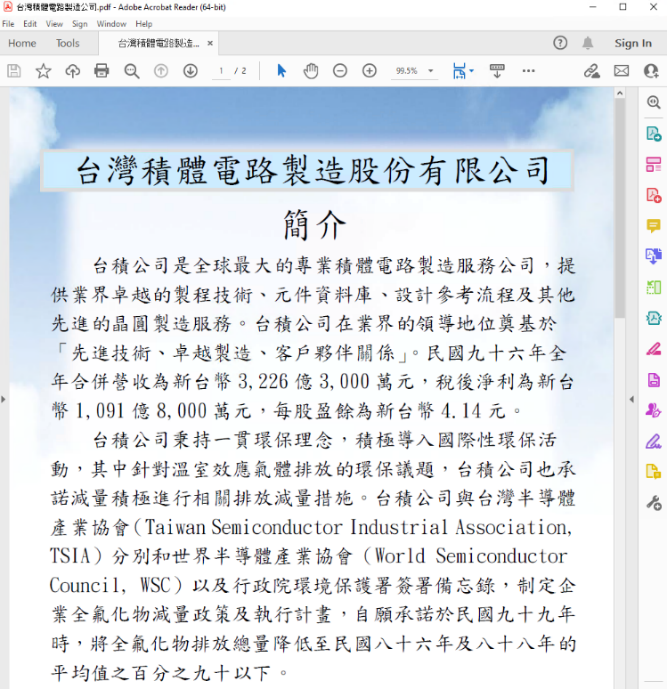
When HyperBro is launched, it would additionally show a PDF pretending to be from TSMC to divert consideration, obtain a stealthier compromise, and keep away from elevating suspicions.
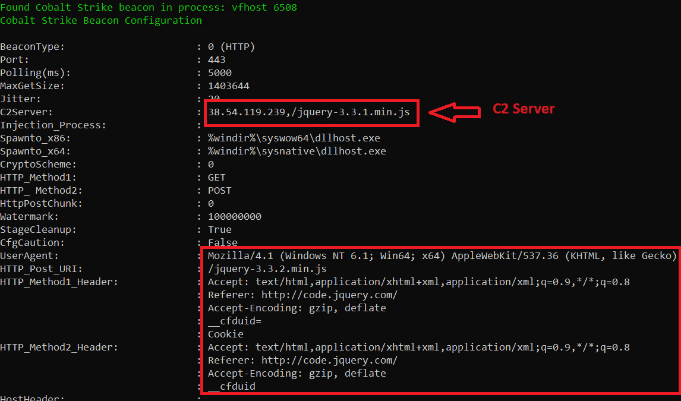
The loader makes use of DLL side-loading to launch a Cobalt Strike beacon in reminiscence, leveraging a digitally signed binary from CyberArk’s vfhost.exe.
A file named ‘bin.config’ that incorporates XOR encrypted Cobalt Strike shellcode is decrypted and loaded into the reliable ‘vfhost.exe’ course of, evading AV detection.
The command and management (C2) server handle hardcoded into the Cobalt Strike implant used on this assault is disguised as a reliable jQuery CDN, permitting it to bypass firewall defenses.
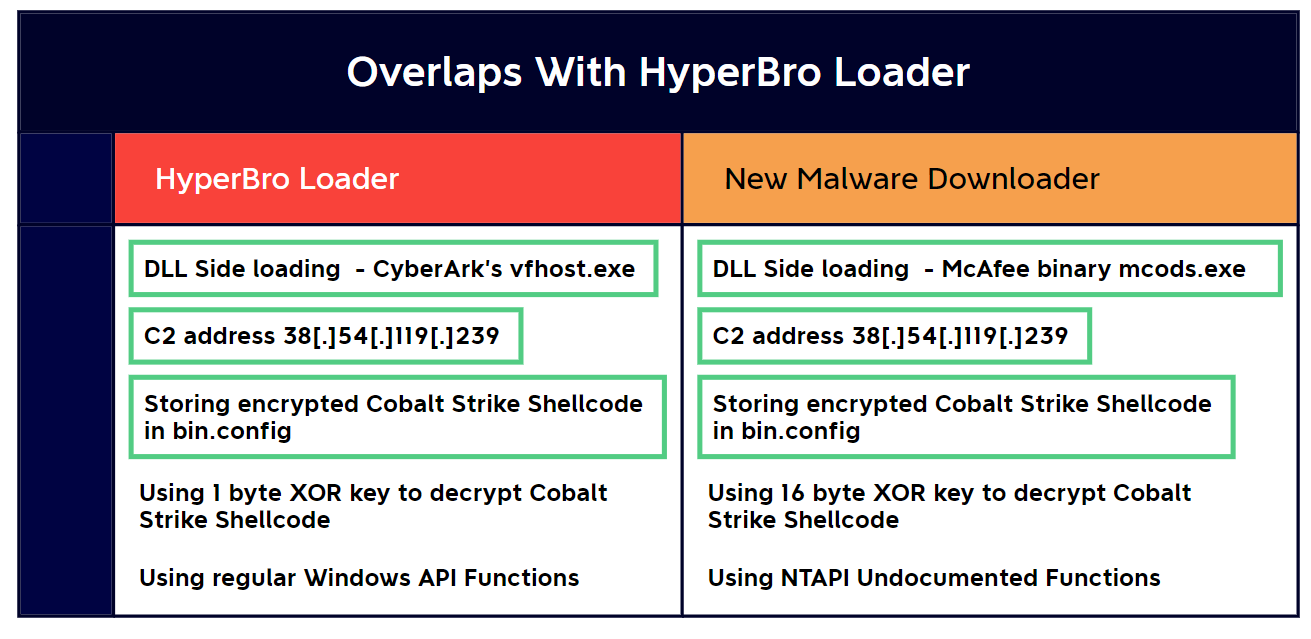
On a second variant of the assault, the hackers use a compromised Cobra DocGuard internet server to drop a further McAfee binary (‘mcods.exe’) and cargo extra Cobalt Strike shellcode utilizing DLL side-loading once more by way of ‘mcvsocfg.dll.’
On this case, the hackers deployed a beforehand undocumented Go-based backdoor named ‘ChargeWeapon,’ designed to collect and transmit host information to the C2 in base64-encoded kind.
ChargeWeapon employs easy malware evasion strategies offered by the “garble” open-source software, whereas its capabilities embody the next:
- Talk with a distant system utilizing the default Home windows command line interface
- Execute instructions by Home windows Administration Instrumentation (WMI)
- Make the most of TCP over HTTP for its C2 communications
- Use base64 encoding to obfuscate information throughout C2 connection
- Reads and writes information on the contaminated host
Attributed to China
Eclectic says the noticed TTPs present intensive similarities with Chinese language risk group’s operations, like RedHotel and APT27 (aka Budworm, LuckyMouse).
“EclecticIQ analysts assess with excessive confidence that the analyzed Hyperbro Loader, the malware downloader and the GO backdoor are very doubtless operated and developed by a PRC backed nation-state risk actor, resulting from victimology, infrastructure noticed, malware code and resemblance with beforehand reported exercise clusters,” explains EclecticIQ.
Symantec and ESET have each beforehand reported about China-sponsored APTs leveraging Cobra DocGuard servers for malware supply, additional strengthening the attribution speculation to Chinese language hackers.


