
Vulnerabilities affecting a Bluetooth chipset current in additional than two dozen audio gadgets from ten distributors will be exploited for eavesdropping or stealing delicate info.
Researchers confirmed that 29 gadgets from Beyerdynamic, Bose, Sony, Marshall, Jabra, JBL, Jlab, EarisMax, MoerLabs, and Teufel are affected.
The listing of impacted merchandise contains audio system, earbuds, headphones, and wi-fi microphones.
The safety issues might be leveraged to take over a weak product and on some telephones, an attacker inside connection vary might be able to extract name historical past and contacts.
Snooping over a Bluetooth connection
On the TROOPERS safety convention in Germany, researchers at cybersecurity firm ERNW disclosed three vulnerabilities within the Airoha techniques on a chip (SoCs), that are broadly utilized in True Wi-fi Stereo (TWS) earbuds.
The problems aren’t crucial and moreover shut bodily proximity (Bluetooth vary), their exploitation additionally requires “a excessive technical ability set.” They acquired the next identifiers:
- CVE-2025-20700 (6.7, medium severity rating) – lacking authentication for GATT providers
- CVE-2025-20701 (6.7, medium severity rating) – lacking authentication for Bluetooth BR/EDR
- CVE-2025-20702 (7.5, excessive severity rating) – crucial capabilities of a customized protocol
ERNW researchers say they created a proof-of-concept exploit code that allowed them to learn the at present enjoying media from the focused headphones.
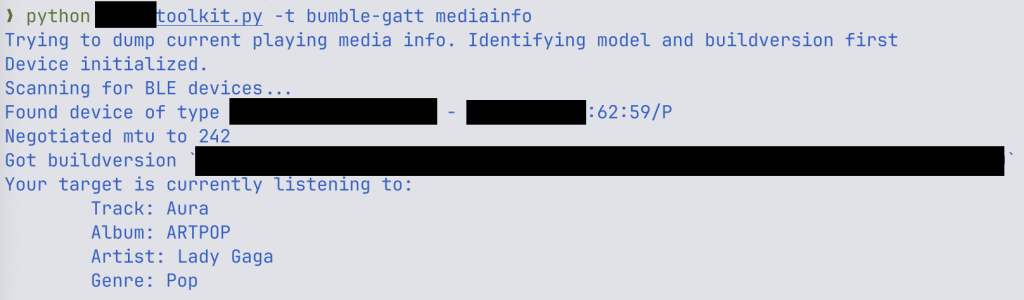
supply: ERWN
Whereas such an assault might not current a fantastic danger, different eventualities leveraging the three bugs may let a risk actor hijack the connection between the cell phone and an audio Bluetooth system and use the Bluetooth Fingers-Free Profile (HFP) to situation instructions to the cellphone.
“The vary of accessible instructions relies on the cell working system, however all main platforms help at the very least initiating and receiving calls” – ERNW
The researchers had been capable of set off a name to an arbitrary quantity by extracting the Bluetooth hyperlink keys from a weak system’s reminiscence.
They are saying that relying on the cellphone’s configuration, an attacker may additionally retrieve the decision historical past and contacts.
They had been additionally capable of provoke a name and “efficiently snoop on conversations or sounds inside earshot of the cellphone.”
Moreover, the weak system’s firmware may doubtlessly be rewritten to allow distant code execution, thereby facilitating the deployment of a wormable exploit able to propagating throughout a number of gadgets.
Assault restrictions apply
Though the ERNW researchers current critical assault eventualities, sensible implementation at scale is constrained by sure limitations.
“Sure — the concept that somebody may hijack your headphones, impersonate them in the direction of your cellphone, and doubtlessly make calls or spy on you, sounds fairly alarming.”
“Sure — technically, it’s critical,” the researchers say, including that “actual assaults are advanced to carry out.”
The need of each technical sophistication and bodily proximity confines these assaults to high-value targets, akin to these in diplomacy, journalism, activism, or delicate industries.
Airoha has launched an up to date SDK incorporating crucial mitigations, and system producers have began patch growth and distribution.
Nonetheless, German publication Heise says that the newest firmware updates for greater than half of the affected gadgets are from Could 27 or earlier, which is earlier than Airoha delivered the up to date SDK to its prospects.



