
A beforehand undocumented spyware and adware referred to as ‘Batavia’ has been focusing on massive industrial enterprises in Russia in a phishing e-mail marketing campaign that makes use of contract-related lures.
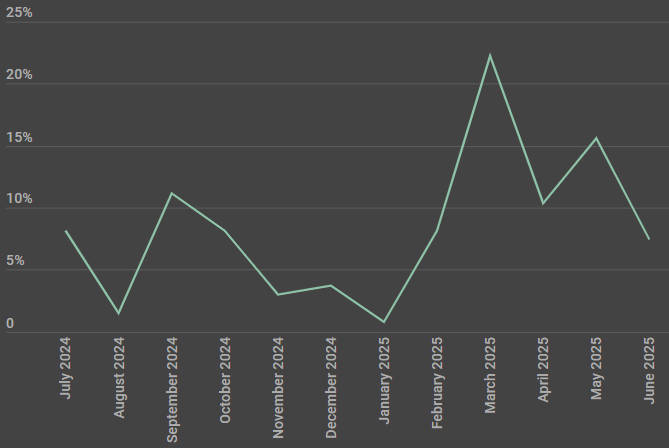
The researchers imagine the operation has been lively since at the very least final 12 months in July and is ongoing. Based mostly on telemetry knowledge, the phishing emails delivering Batavia have reached staff at a number of dozen Russian organizations have been focused.
Since January 2025, the marketing campaign has elevated in depth and peaked in direction of the top of February.
Supply: Kaspersky
Batavia assault chain
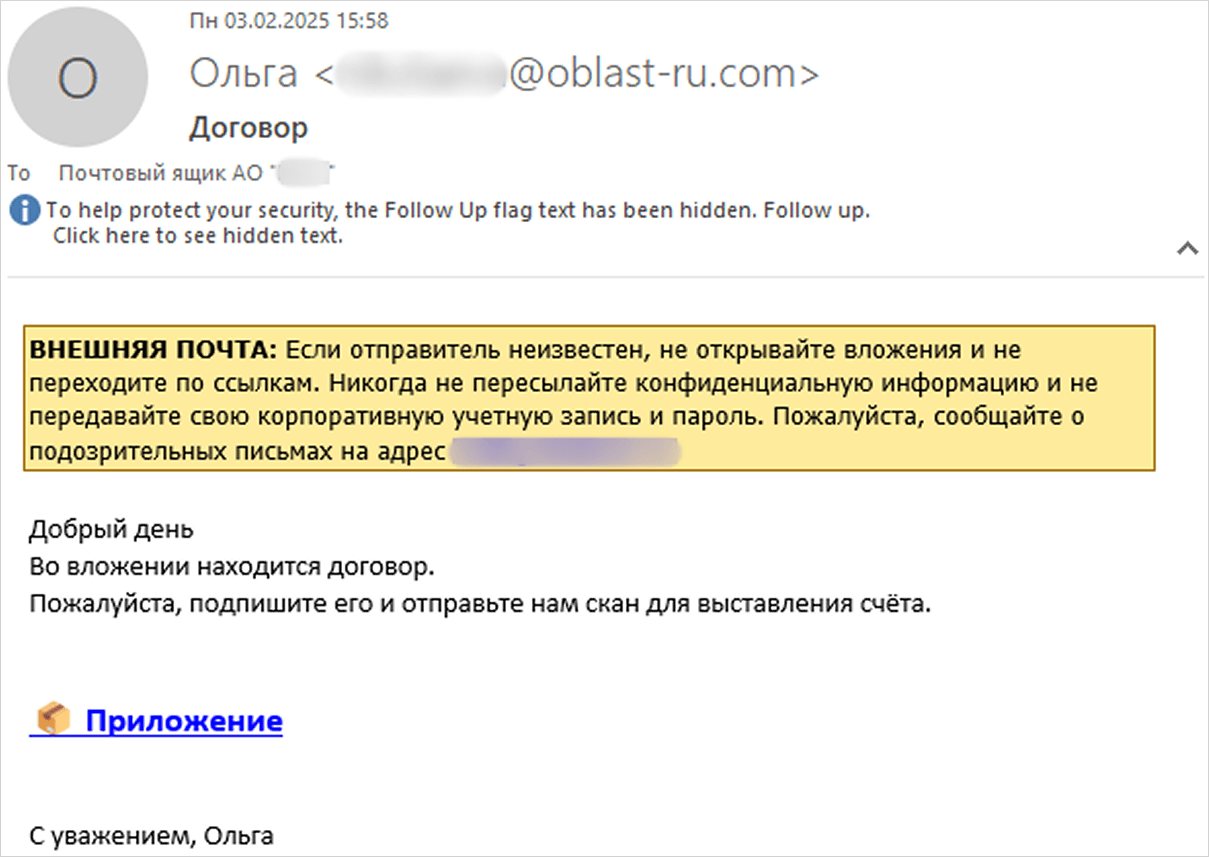
Researchers at Kaspersky say that the assaults start with an e-mail embedding a hyperlink disguised as a contract attachment. Clicking it downloads an archive that with a malicious Visible Primary Encoded script (.VBE) file.
When executed, the script profiles the host system and sends the main points to the attacker’s command and management server (C2). Then it downloads the following stage payload, WebView.exe, from oblast-ru[.]com.
Supply: Kaspersky
The second stage is a Delphi-based malware that shows a pretend contract to the sufferer for diversion whereas accumulating system logs, paperwork, and capturing screenshots within the background.
The collected knowledge is then exfiltrated to ru-exchange[.]com, whereas the malware makes use of a hash of the primary 40,000 bytes of every file to keep away from redundant uploads.
Lastly, it fetches the third-stage payload, ‘javav.exe,’ a C++ knowledge stealer, and provides a startup shortcut to execute it on OS boot.
The ultimate payload expands the info assortment much more, focusing on extra file sorts (photos, shows, emails, archives, spreadsheets, TXTs, and RTFs).
Kaspersky notes within the report that there’s probably a fourth payload, named ‘windowsmsg.exe’ – probably used for the following stage of the assault, however the researchers could not retrieve it.
The researchers haven’t speculated concerning the objective of the marketing campaign however the targets mixed with Batavia’s capabilities may point out an espionage operation on Russia’s industrial exercise.


