You’ve simply downloaded a brand new cellular sport, cryptocurrency pockets, or health app, however one thing isn’t proper. Your cellphone’s display is swamped by annoying adverts, the app shouldn’t be doing what you’ll anticipate it do, and, God forbid, you discovered an unauthorized transaction in your checking account.
Chances are high good that the app you downloaded has been after your cash or delicate info. Given the wealth of knowledge we entry by way of our smartphones, it’s little marvel that cybercriminals have their sights on these gadgets, with threats looming giant particularly in third-party app shops.
In line with the ESET Risk Report T3 2022, the variety of Android threats soared by 57% in the previous couple of months of 2022, having been pushed by a whopping 163% improve in adware and progress of 83% in HiddenApps detections,
Fortunately, you may keep away from each malware and doubtlessly undesirable functions (PUAs) by being cautious and doing all of your diligence. Our ideas beneath will aid you to identify a doubtlessly dodgy app from miles away, in addition to get your cellphone again into form if you happen to downloaded such an app.
Tips on how to acknowledge a faux app
Say you’re in search of what you’ll fairly anticipate to be an app with a whole bunch of thousands and thousands of customers however solely come throughout an app that, whereas sounding like the true factor, hasn’t racked up nowhere close to as many downloads. If that’s the case, likelihood is excessive you’re coping with an imposter app.
Certainly, be cautious everytime you’re trying to obtain an app that has been the discuss of the city these days. Cybercriminals are at all times wanting to piggyback off a surge within the reputation of an app or service with the intention to push copycat apps to the market. One current instance is a slew of sketchy apps that try and journey the ChatGPT craze and that have been rolled out even earlier than the official app was launched.
A lot the identical applies to bogus updates for official and widely-used apps. One instance is the curious case of WhatsApp Pink, a faux shade theme for WhatsApp that was peddled by way of messages on the app in 2021.
If an app is rated poorly, it’s best to most likely give it a go. However, tons of glowing critiques that each one sound nearly the identical also needs to elevate eyebrows. That is particularly the case with apps that haven’t been downloaded thousands and thousands of occasions – a lot of these suggestions could be the work of pretend reviewers and even bots.
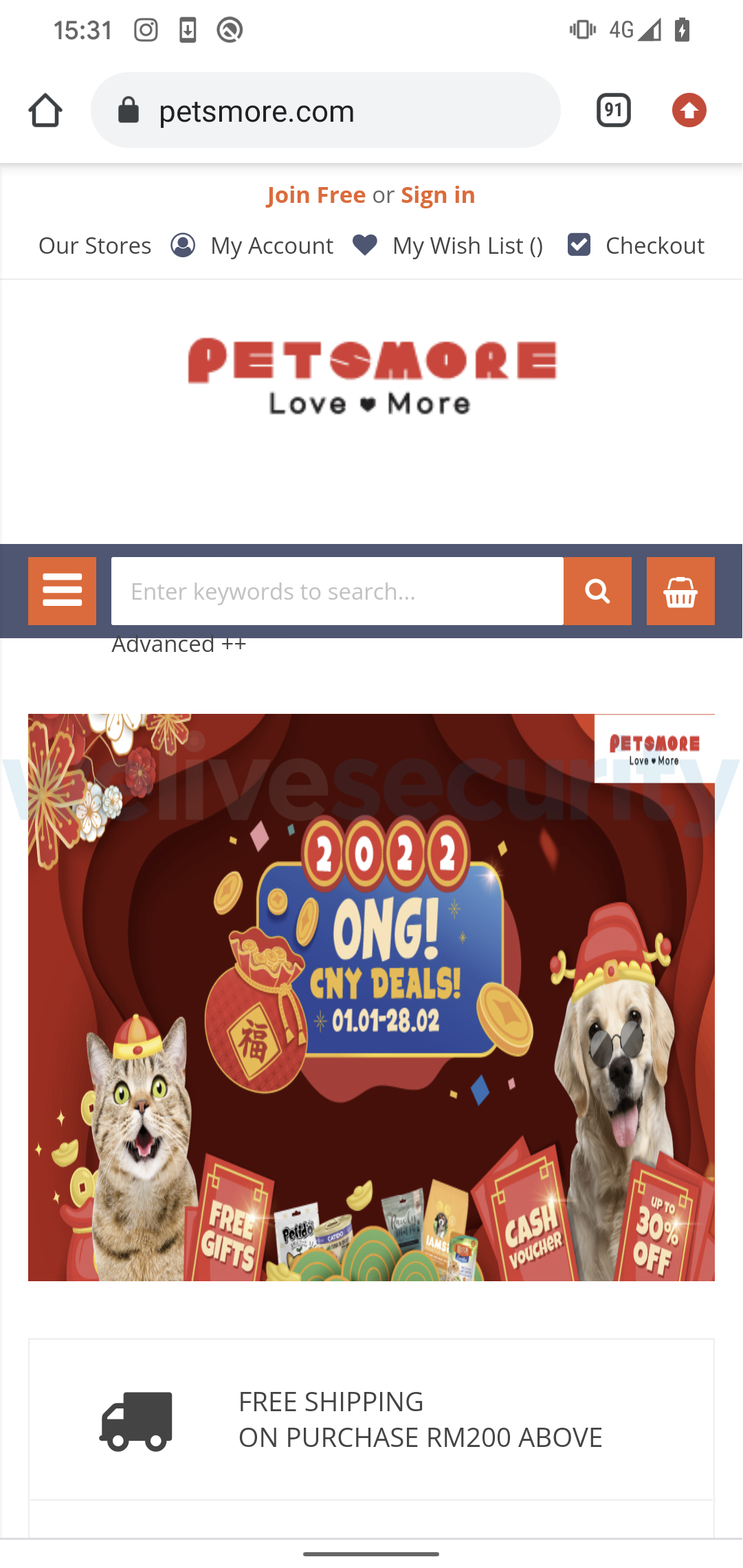
One thing in regards to the app’s shade or brand used doesn’t really feel proper … Should you’re unsure, evaluate the visuals to these on the web site of the service supplier. Malicious apps usually their mimic official counterparts and use comparable, however not essentially equivalent, logos.
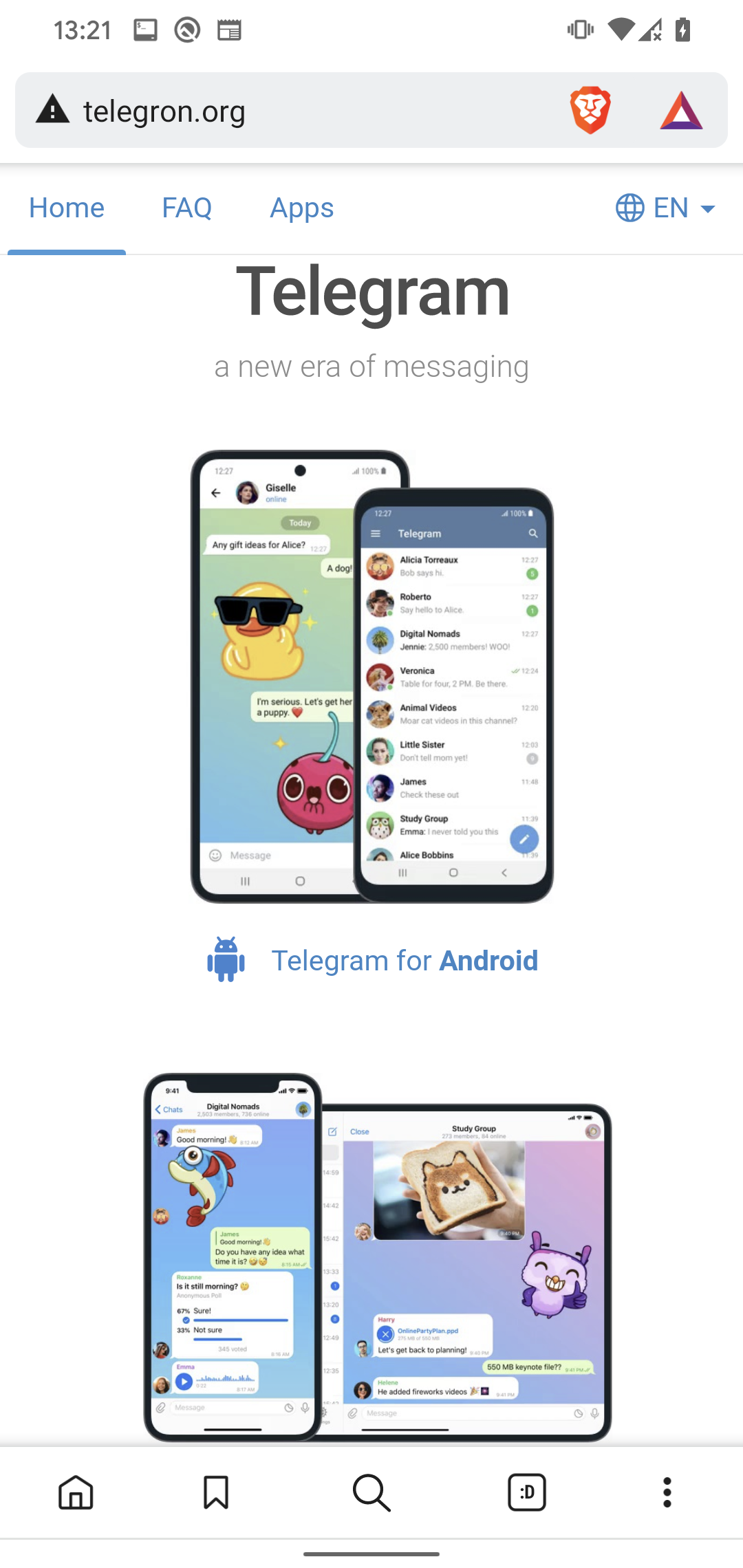
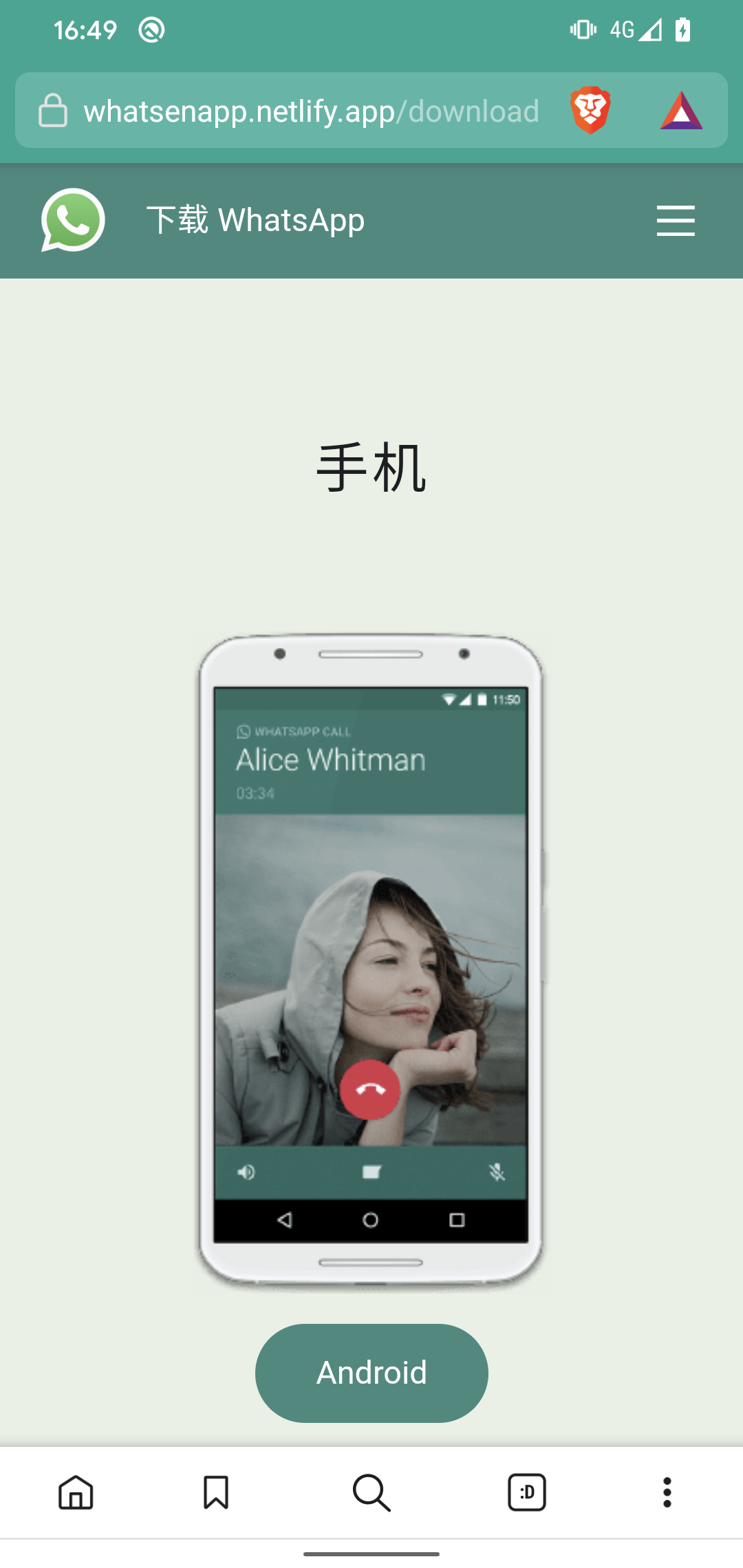
Nevertheless, don’t be lulled right into a false sense of safety simply since you acknowledged the brand of a widely known financial institution, fee processor or cryptocurrency pockets. Some apps not solely misuse the identify of a legit service, however are additionally distributed by way of web sites which are the spitting photos of the official websites. Preserve your eyes peeled for particulars – a more in-depth look, together with on the URLs, usually reveals some giveaways.
Official web site on the left, copycat on the precise (Supply: ESET Analysis)
Web sites impersonating Telegram and WhatsApp (Supply: ESET Analysis)
- Doublecheck the “official app” claims
In a single case documented by ESET analysis final 12 months, cybercriminals distributed apps for on-line shops and banks that usually didn’t even have an app accessible on Google Play.
When downloading a cellular app that needs to be related to a preferred on-line service, ensure that the service truly presents such an app. If that’s the case, its official web site will accommodates hyperlinks to the apps in Google Play Retailer and/or Apple App Retailer. The quantity and number of malicious ChatGPT-themed apps is a useful instance.
- Test the app’s identify and outline
Official app builders sometimes go to nice pains to keep away from coming throughout as unprofessional. This additionally applies to issues as mundane as app descriptions – learn by them to see if you happen to can spot poor grammar or inconsistent and incomplete particulars. These usually present a clue that an app isn’t what it’s claimed to be.
- Test the developer’s pedigree
Tread additionally fastidiously when coping with an app from an unknown app developer with no observe document in app growth. Don’t be fooled by a reputation that rings a bell, both – shady app makers could also be misusing the identify of a official and well-known entity. Doublecheck if the developer has different apps to their identify and that the apps are respected; if unsure, seek for the developer’s identify in Google.
READ ALSO: Monitoring down the developer of Android adware affecting thousands and thousands of customers
- Look out for extreme app permissions
Final however positively not least, keep away from apps that require extreme consumer permissions – that’s, the sorts of privileges that they don’t actually need to do their job. A flashlight app hardly wants admin rights and entry to core system performance.
7 methods to inform that you just downloaded a dangerous app
Listed here are a number of indicators that your newly-installed app might be sketchy:
- The app isn’t doing its job
For example, again in 2018 ESET researchers analyzed a set of apps that posed as safety options, however all they did was show undesirable adverts and provide pseudo-security. They solely mimicked primary safety features with very primitive safety checkers that relied on a number of trivial hardcoded guidelines. Consequently, they usually detected official apps as malicious and created a false sense of safety within the victims.
In case your new “sport” seems to be a playing platform, one thing isn’t proper. Test once more what it’s that you just’ve truly downloaded.
Does the app exhibit bizarre conduct, resembling beginning up, closing, or failing altogether for no obvious cause? This is likely one of the most evident indicators that you might have downloaded a dodgy app.
- You incurred sudden costs
Should you’ve noticed undesirable costs in your bank card or cellphone invoice, it might be as a result of an app you downloaded just lately.
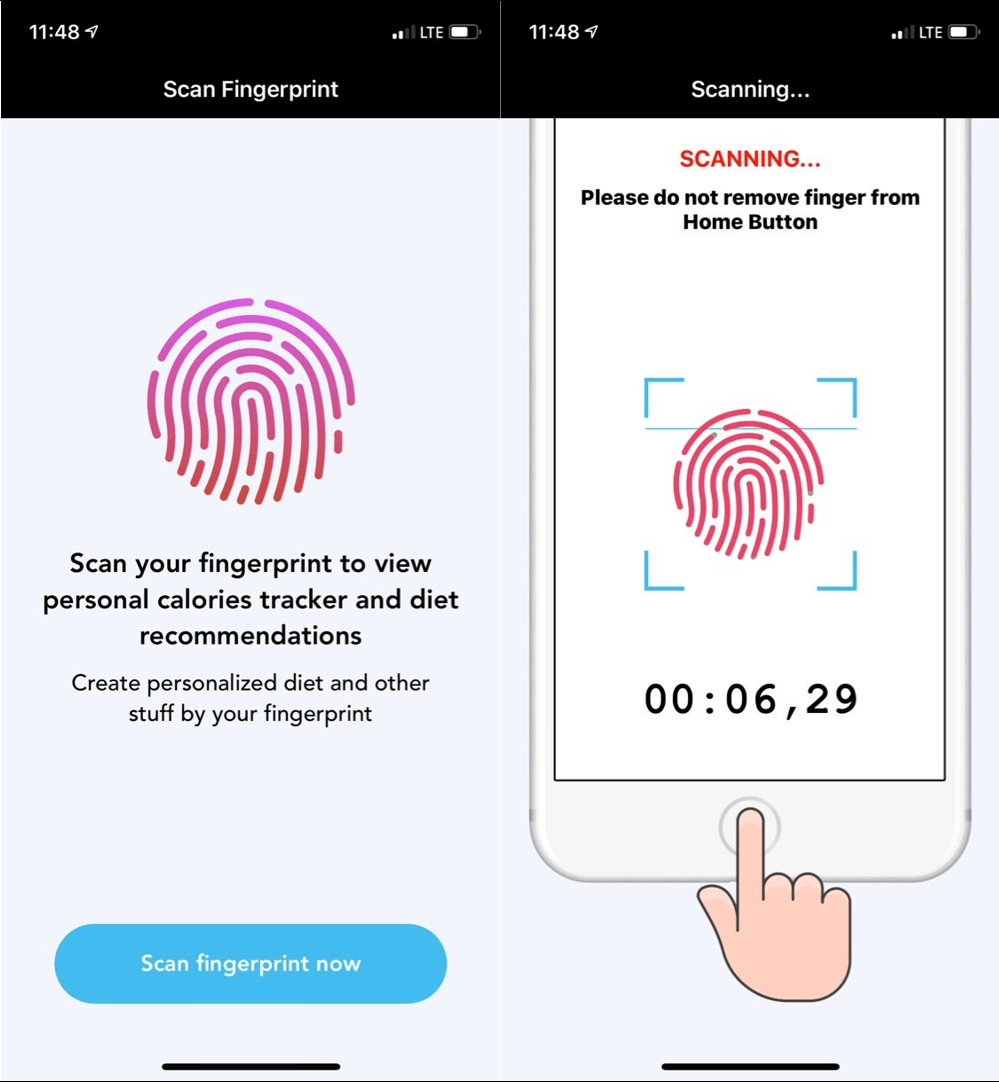
For example, ESET researchers noticed a number of apps that posed as fitness-tracking instruments and abused Apple’s Contact ID function to steal cash from iOS customers. After a consumer launched one of many apps for the primary time, it requested a fingerprint scan to “view their customized calorie tracker and food regimen suggestions”. If the consumer had a credit score or debit card immediately linked to an Apple account, the malware would go on to steal cash from the victims by way of fraudulent in-app funds.
Be careful for scams that contain downloading a peer-to-peer (P2P) fee service and provide fictitious services at hearth sale costs. As a result of funds are sometimes immediate and can’t be canceled, it’s possible you’ll lose cash by paying for one thing you’ll by no means obtain.
Determine 4. Sketchy iOS apps asking customers to scan their fingers for health monitoring earlier than exhibiting dodgy funds
- Unusual messages and calls
One other signal of bother includes malware spamming out messages out of your cellphone to your contacts (like FluBot does). In different circumstances, your name or textual content message historical past could comprise unknown entries as malware makes an attempt to make unauthorized calls or ship messages to premium-rate numbers.
Does your system battery get drained far sooner than traditional? It could be as a result of background exercise that consumes the system’s assets and will finally point out that your system has been compromised by malware.
Should you expertise a significant and sudden surge in your web knowledge utilization with none change in your searching or cellphone utilization habits, it may be due to an app’s exercise within the background.
- Random advert pop-ups and unknown apps
A malicious app could go on to put in further apps within the background and with out your authorization. The identical goes for pesky adware displaying undesirable adverts in your system. Should you spot any of this, likelihood is excessive it is advisable act quick.
What to do subsequent?
After discovering what you watched is a sketchy app, take away it or, even higher, obtain respected cellular safety software program that can scan your system and take away the app for you.
Should you go the “guide” route as a substitute, reset your cellphone to manufacturing facility settings (previous to that, be sure you have your knowledge backed up). Alternatively, it’s possible you’ll typically need to boot up your system in Protected Mode after which take away the app. The video by ESET malware researcher Lukas Stefanko exhibits you ways:
https://www.youtube.com/watch?v=dIIDh1AqUKQ
Additionally, do different potential victims a favor and report the app to the related app retailer from which you downloaded the app. You can even attempt to declare a refund.
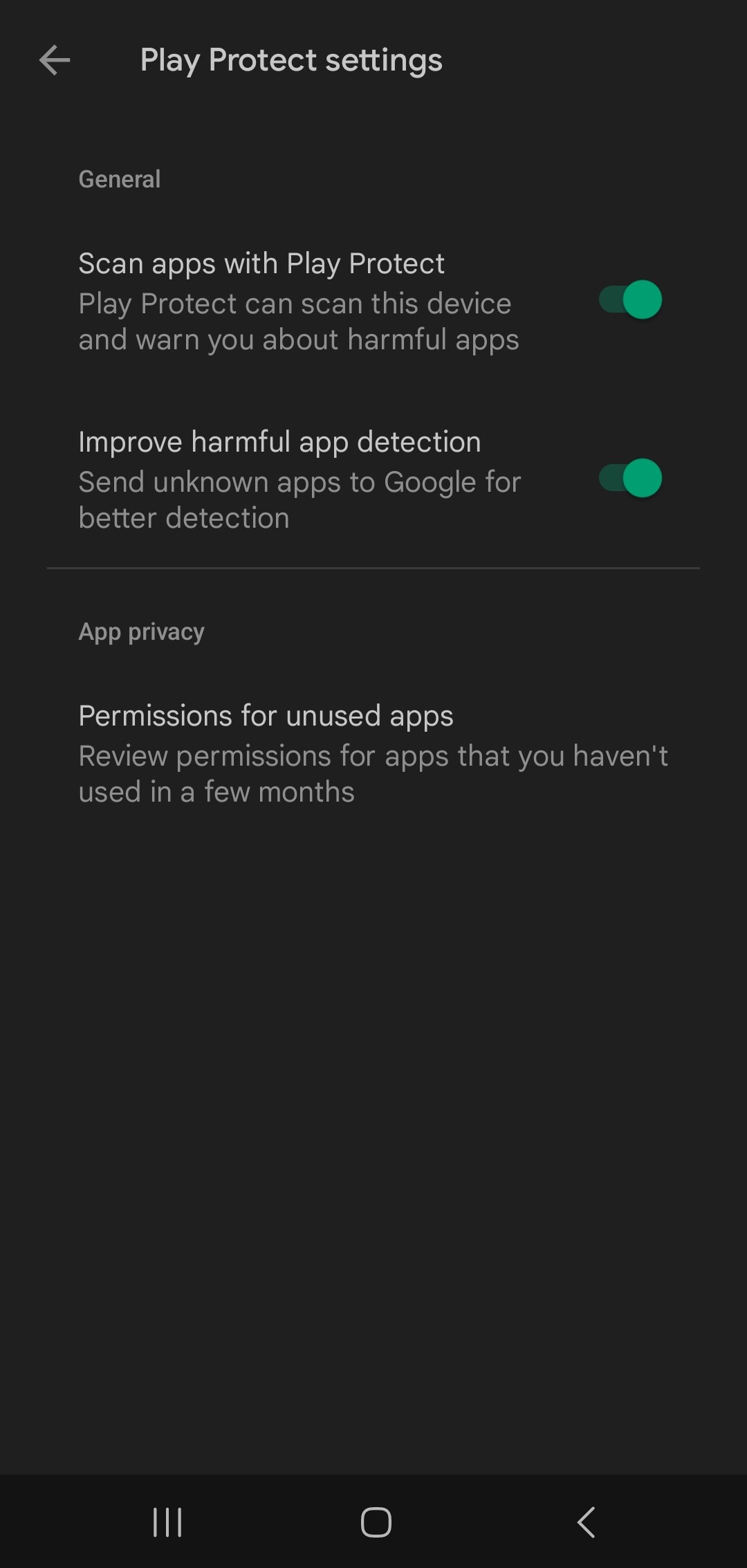
Going ahead, if you happen to use apps from the Google Play Retailer, be sure that to allow the Google Play Shield scanning in your system. You can even examine the apps you’ve downloaded from exterior of the Google Play Retailer. To take action, activate “Enhance dangerous app detection”, which can ship unknown apps to Google robotically.
What if you happen to’re an iOS consumer? Opposite to what many individuals might imagine, downloading a dodgy app on iOS, even from Apple App Retailer, isn’t remarkable. For extra on what to do if a foul app(le) slipped by the iOS security web, head over to our current deep dive into the subject:
Can your iPhone be hacked? What to learn about iOS safety
7 ideas for staying secure
Lastly, a number of fast ideas for staying secure whereas utilizing your cellular system:
- Persist with Google Play and Apple App Retailer; i.e., keep away from placing your self in danger by putting in apps from third-party shops.
- Don’t mindlessly click on on hyperlinks despatched by way of social media messages or emails.
- Use two-factor authentication (2FA) on all of your on-line accounts that provide it, particularly on people who comprise your helpful knowledge.
- Preserve your cellphone’s working system and apps up-to-date.
- Persist with apps whose builders proceed to enhance their merchandise and repair safety vulnerabilities and efficiency bugs.
- Safe your system’s display with a passcode ample size and complexity or a stable biometric function resembling a fingerprint – or, ideally, a mix of each!
- Use cellular safety software program.