
Web-exposed WS_FTP servers unpatched in opposition to a most severity vulnerability are actually focused in ransomware assaults.
As not too long ago noticed by Sophos X-Ops incident responders, risk actors self-described because the Reichsadler Cybercrime Group tried, unsuccessfully, to deploy ransomware payloads created utilizing a LockBit 3.0 builder stolen in September 2022.
“The ransomware actors did not wait lengthy to abuse the not too long ago reported vulnerability in WS_FTP Server software program,” Sophos X-Ops stated.
“Despite the fact that Progress Software program launched a repair for this vulnerability in September 2023, not the entire servers have been patched. Sophos X-Ops noticed unsuccessful makes an attempt to deploy ransomware by means of the unpatched companies.”
The attackers tried to escalate privileges utilizing the open-source GodPotato device, which permits privilege escalation to ‘NT AUTHORITYSYSTEM’ throughout Home windows shopper (Home windows 8 to Home windows 11) and server (Home windows Server 2012 to Home windows Server 2022) platforms.
Thankfully, their try to deploy the ransomware payloads on the sufferer’s techniques was thwarted, stopping the attackers from encrypting the goal’s knowledge.
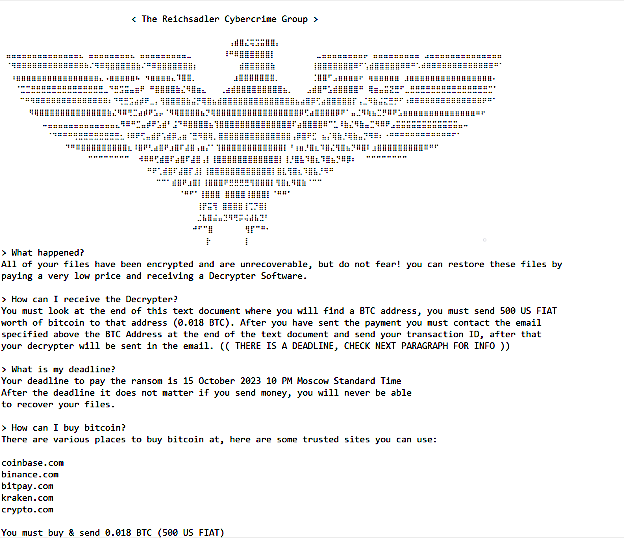
Despite the fact that they didn’t encrypt the information, the risk actors nonetheless demanded a $500 ransom, payable by October 15, Moscow Commonplace Time.
The low ransom demand hints at Web-exposed and susceptible WS_FTP servers possible being focused in mass automated assaults or by an inexperienced ransomware operation.
Tracked as CVE-2023-40044, the flaw is brought on by a .NET deserialization vulnerability within the Advert Hoc Switch Module, enabling unauthenticated attackers to execute instructions on the underlying OS by way of HTTP requests remotely.
On September 27, Progress Software program launched safety updates to deal with the important WS_FTP Server vulnerability, urging admins to improve susceptible cases.
“We do advocate upgrading to probably the most highest model which is 8.8.2. Upgrading to a patched launch, utilizing the complete installer, is the one approach to remediate this challenge,” Progress stated.
Assetnote safety researchers who found the WS_FTP bug launched proof-of-concept (PoC) exploit code simply days after it was patched.
“From our evaluation of WS_FTP, we discovered that there are about 2.9k hosts on the web which might be working WS_FTP (and now have their webserver uncovered, which is important for exploitation). Most of those on-line belongings belong to giant enterprises, governments and academic establishments,” Assetnote stated.
Cybersecurity firm Rapid7 revealed that attackers started exploiting CVE-2023-40044 on September 3, the day the PoC exploit was launched.
“The method execution chain appears the identical throughout all noticed cases, indicating attainable mass exploitation of susceptible WS_FTP servers,” Rapid7 warned.
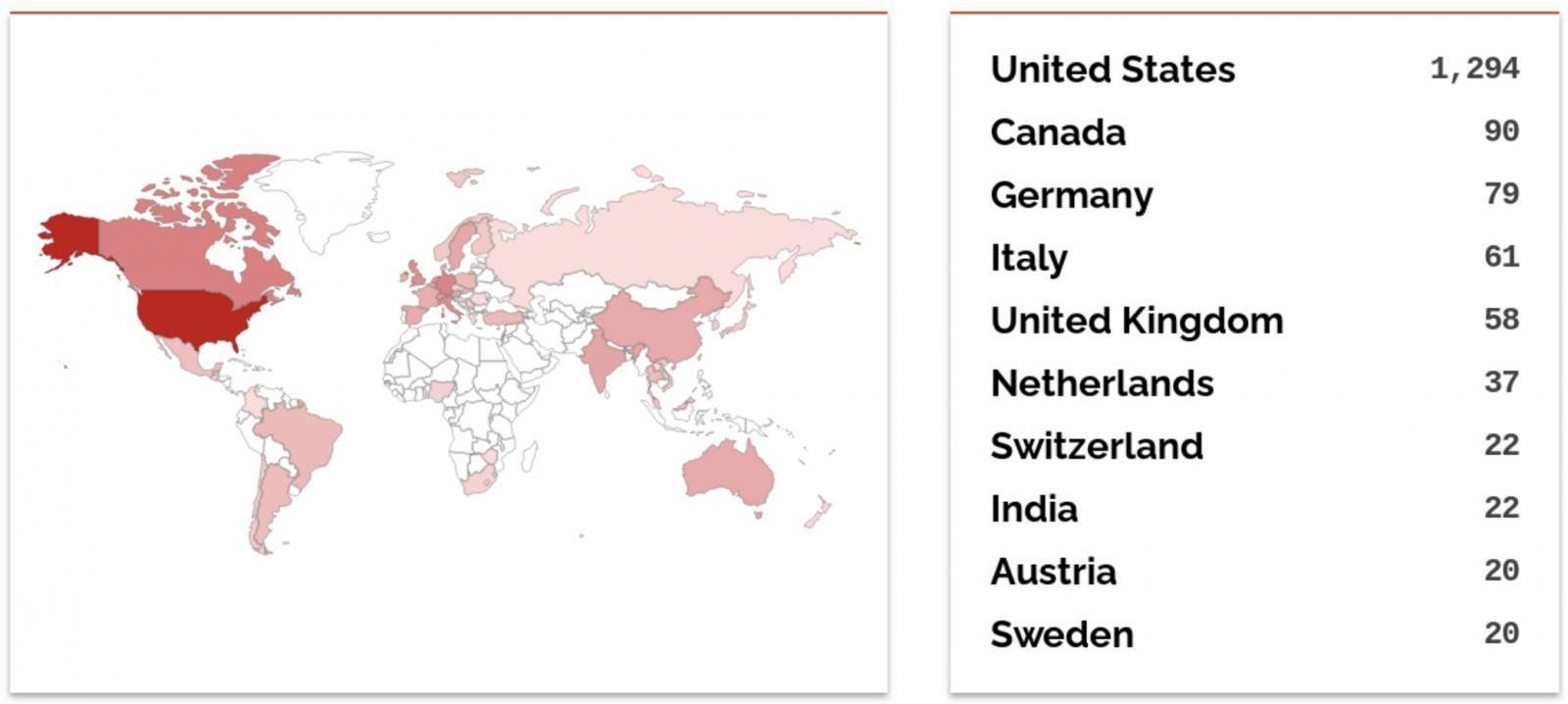
Shodan lists virtually 2,000 Web-exposed units working WS_FTP Server software program, confirming Assetnote’s preliminary estimates.
Organizations that can’t instantly patch their servers can block incoming assaults by disabling the susceptible WS_FTP Server Advert Hoc Switch Module.
The Well being Sector Cybersecurity Coordination Heart (HC3), U.S. Well being Division’s safety crew additionally warned Healthcare and Public Well being sector organizations final month to patch their servers as quickly as attainable.
Progress Software program is at present coping with the aftermath of a widespread sequence of information theft assaults that exploited a zero-day bug in its MOVEit Switch safe file switch platform earlier this 12 months.
These assaults impacted over 2,500 organizations and greater than 64 million people, as estimated by Emsisoft.

