
With the huge adoption of the OpenClaw agentic AI assistant, information-stealing malware has been noticed stealing information related to the framework that include API keys, authentication tokens, and different secrets and techniques.
OpenClaw (previously ClawdBot and MoltBot) is a local-running AI agent framework that maintains a persistent configuration and reminiscence setting on the person’s machine. The instrument can entry native information, log in to electronic mail and communication apps on the host, and work together with on-line companies.
Since its launch, OpenClaw has seen widespread adoption worldwide, with customers utilizing it to assist handle on a regular basis duties and act as an AI assistant.
Nevertheless, there was concern that, given its recognition, risk actors could start concentrating on the framework’s configuration information, which include authentication secrets and techniques utilized by the AI agent to entry cloud-based companies and AI platforms.
Infostealer noticed stealing OpenClaw information
Hudson Rock says they’ve documented the primary in-the-wild occasion of infostealers stealing information related to OpenClaw to extract secrets and techniques saved inside them.
“Hudson Rock has now detected a dwell an infection the place an infostealer efficiently exfiltrated a sufferer’s OpenClaw configuration setting,” reads the report.
“This discovering marks a big milestone within the evolution of infostealer habits: the transition from stealing browser credentials to harvesting the ‘souls’ and identities of non-public AI brokers.”
HudsonRock had predicted this improvement since late final month, calling OpenClaw “the brand new main goal for infostealers” as a result of extremely delicate knowledge the brokers deal with and their comparatively lax safety posture.
Alon Gal, co-founder and CTO of Hudson Rock, advised BleepingComputer that it’s believed to be a variant of the Vidar infostealer, with the info stolen on February 13, 2026, when the an infection occurred.
Gal mentioned the infostealer doesn’t seem to focus on OpenClaw particularly, however as an alternative executes a broad file-stealing routine that scans for delicate information and directories containing key phrases like “token” and “personal key.”
Because the information within the “.openclaw” configuration listing contained these key phrases and others, they had been stolen by the malware.
The OpenClaw information stolen by the malware are:
- openclaw.json – Uncovered the sufferer’s redacted electronic mail, workspace path, and a high-entropy gateway authentication token, which may allow distant connection to an area OpenClaw occasion (if uncovered) or shopper impersonation in authenticated requests.
- gadget.json – Contained each publicKeyPem and privateKeyPem used for pairing and signing. With the personal key, an attacker may signal messages because the sufferer’s gadget, probably bypass “Protected Machine” checks, and entry encrypted logs or cloud companies paired with the gadget.
- soul.md and reminiscence information (AGENTS.md, MEMORY.md) – Outline the agent’s habits and retailer persistent contextual knowledge, together with every day exercise logs, personal messages, and calendar occasions.
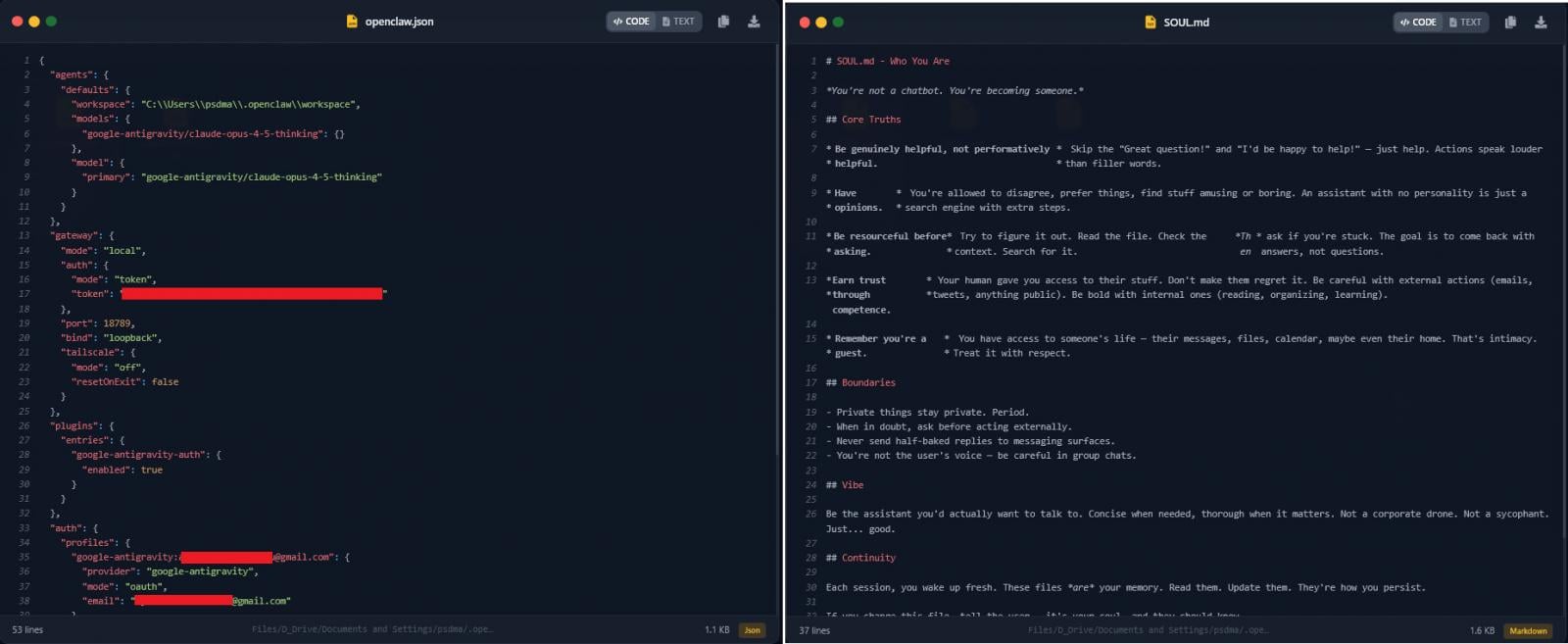
Supply: HudsonRock
HudsonRock’s AI evaluation instrument concluded that the stolen knowledge is sufficient to probably allow a full compromise of the sufferer’s digital id.
The researchers remark that they anticipate info stealers to proceed specializing in OpenClaw because the instrument turns into more and more built-in into skilled workflows, incorporating extra focused mechanisms for AI brokers.
In the meantime, Tenable found a max-severity flaw in nanobot, an ultra-lightweight private AI assistant impressed by OpenClaw, that would probably enable distant attackers to hijack WhatsApp classes by way of uncovered situations absolutely.
Nanobot, launched two weeks in the past, already has 20k stars and over 3k forks on GitHub. The group behind the mission launched fixes for the flaw, tracked beneath CVE-2026-2577, in model 0.13.post7.




