A newly found toolkit referred to as DKnife has been used since 2019 to hijack site visitors on the edge-device degree and ship malware in espionage campaigns.
The framework serves as a post-compromise framework for site visitors monitoring and adversary-in-the-middle (AitM) actions. It’s designed to intercept and manipulate site visitors destined for endpoints (computer systems, cell gadgets, IoTs) on the community.
Researchers at Cisco Talos say that DKnife is an ELF framework with seven Linux-based elements designed for deep packet inspection (DPI), site visitors manipulation, credential harvesting, and malware supply.
The malware options Simplified Chinese language language artifacts in part names and code feedback, and explicitly targets Chinese language providers corresponding to electronic mail suppliers, cell apps, media domains, and WeChat customers.
Talos researchers assess with excessive confidence that the operator of DKnife is a China-nexus menace actor.
Supply: Cisco Talos
Researchers could not decide how the community gear is compromised, however discovered that DKnife delivers and interacts with the ShadowPad and DarkNimbus backdoors, each related to Chinese language menace actors.
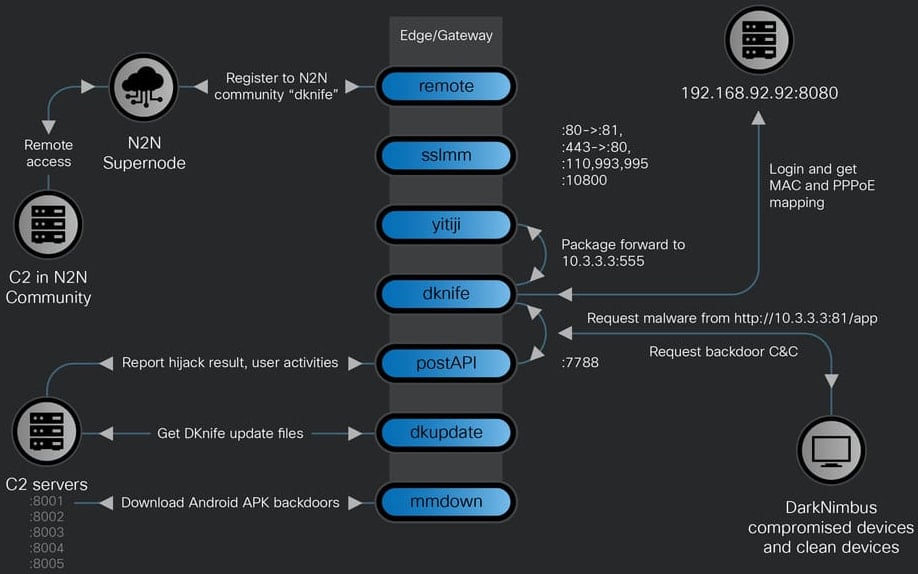
DKnife consists of seven modules, every accountable for particular actions associated to communication with the C2 servers, relaying or altering site visitors, and hiding the malicious site visitors origin:
- dknife.bin – responible for packet inspection and assault logics, it additionally stories assault standing, consumer actions, and sends collected knowledge
- postapi.bin – relay part between DKnife.bin and C2 servers
- sslmm.bin – customized reverse proxy server derived from HAProxy
- yitiji.bin – creates a digital Ethernet interface (TAP) on the router and bridges it into the LAN to route the attacker’s site visitors
- distant.bin – peer-to-peer VPN consumer utilizing the n2n VPN software program
- mmdown.bin – malware downloader and updater for Android APK information
- dkupdate.bin – DKnife obtain, deploy, and replace part
“Its [DKnife’s] key capabilities embody serving replace C2 for the backdoors, DNS hijacking, hijacking Android software updates and binary downloads, delivering ShadowPad and DarkNimbus backdoors, selectively disrupting security-product site visitors and exfiltrating consumer exercise to distant C2 servers,” the researchers stated in a report this week.
As soon as put in, DKnife makes use of its yitiji.bin part to create a bridged TAP interface (digital community system) on the router on the personal IP tackle 10.3.3.3. This permits the menace actor to intercept and rewrite community packets of their transit to the supposed host.
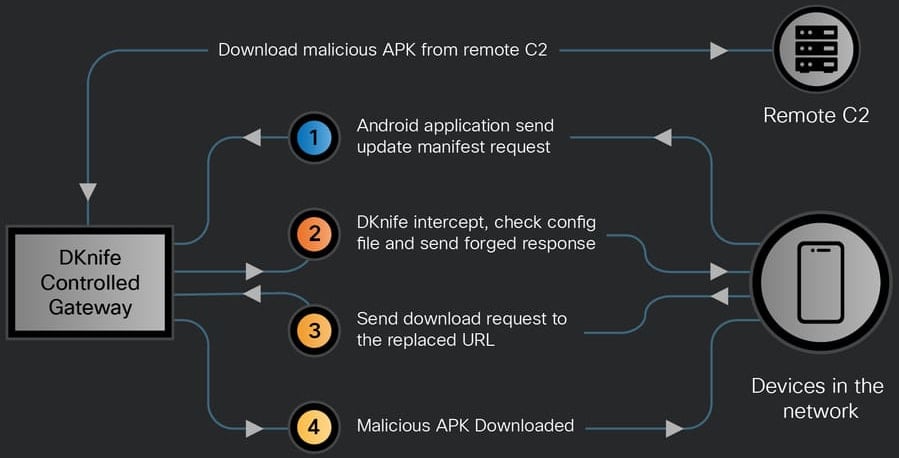
This manner, DKnife can be utilized to ship malicious APK information to cell gadgets or Home windows methods on the community.
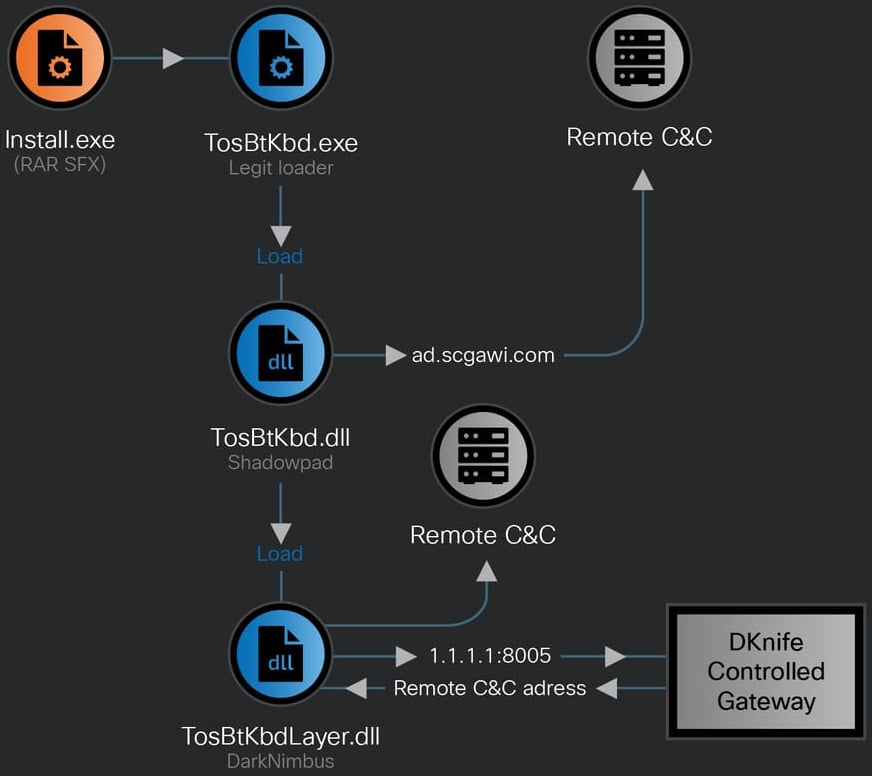
Cisco researchers noticed DKnife dropping the ShadowPad backdoor for Home windows signed with a Chinese language agency’s certificates. This motion was adopted by the deployment of the DarkNimbus backdoor. On Android gadgets, the backdoor is delivered immediately by DKnife.
Supply: Cisco Talos
On the identical infrastructure related to the DKnife framework exercise, the researchers additionally discovered that it was internet hosting the WizardNet backdoor, which ESET researchers beforehand linked to the Spellbinder AitM framework.
Other than payload supply, DKnife can be able to:
- DNS hijacking
- hijacking Android app updates
- hijacking Home windows binaries
- Credential harvesting through POP3/IMAP decryption
- Phishing web page internet hosting
- Anti-virus site visitors disruption
- monitoring consumer exercise, together with messaging app use (WeChat and Sign), maps app use, information consumption, calling exercise, ride-hailing, and procuring
WeChat actions are tracked extra analytically, Cisco Talos says, with DKnife monitoring for voice and video calls, textual content messages, photographs despatched and acquired, and articles learn on the platform.
Supply: Cisco Talos
The consumer’s exercise occasions are first routed internally between DKnife’s elements after which exfiltrated through HTTP POST requests to particular command-and-control (C2) API endpoints.
As a result of DKnife sits on gateway gadgets and stories occasions as packets go via, it permits monitoring consumer exercise and accumulating knowledge in actual time.
As of January 2026, the DKnife C2 servers are nonetheless energetic, the researchers say. Cisco Talos has printed the complete set of indicators of compromise (IoCs) related to this exercise.
Fashionable IT infrastructure strikes quicker than handbook workflows can deal with.
On this new Tines information, find out how your staff can cut back hidden handbook delays, enhance reliability via automated response, and construct and scale clever workflows on high of instruments you already use.




