
Fraudulent Excessive-Yield Funding Applications (HYIPs) are surging globally, pushing “assured” income that no reputable funding can maintain. These scams lure victims with a easy pitch: deposit cash, wait, and withdraw quick returns, typically marketed with exaggerated figures resembling “40% return in 72 hours.”
Learn the total report right here: https://www.ctm360.com/experiences/hyip-risk
However behind the polished branding and faux success tales, HYIPs usually function like basic Ponzi schemes, the place early traders obtain preliminary payouts to create the phantasm of revenue, whereas subsequent investments end in delayed or withheld withdrawals. Referrals are incentivized to maintain funds flowing.
Finally, withdrawals freeze, websites vanish, and the platform operators disappear with the remaining cash.
4,200+ Rip-off Web sites and A whole bunch of Month-to-month Incidents
In an evaluation based mostly on exercise noticed by means of its WebHunt platform, CTM360 recognized a pattern of 4,200+ web sites selling fraudulent HYIP schemes over the previous 12 months.
The corporate additionally recorded 485+ incidents in December 2025 alone, averaging 15+ detections per day, indicating sustained and scalable rip-off exercise.
Two Foremost HYIP Variants Dominating the Marketing campaign
CTM360’s findings spotlight two widespread HYIP codecs:
- Cryptocurrency trading-based HYIPs, constructed to use curiosity in digital belongings
- Foreign exchange and inventory trading-based HYIPs are designed to appear to be reputable market platforms
Each variations depend on the identical core deception: professional-looking interfaces and fabricated efficiency claims meant to extract deposits slightly than generate returns.
Conventional VPNs expose networks to safety dangers, require advanced configurations, and make compliance troublesome. TruGrid SecureRDP eliminates these challenges with a completely managed, cloud-based RDP resolution that requires no open firewall ports.
With built-in MFA, Geo-Blocking, and a Zero Belief framework, TruGrid simplifies distant entry whereas making certain enterprise-grade safety.
How HYIP Operators Unfold These Scams
CTM360 noticed that menace actors closely depend on social media distribution, utilizing:
- Paid social media advertisements (together with Meta/Fb advertisements)
- Telegram and WhatsApp
- Bogus social profiles selling “make investments/revenue/commerce” themes
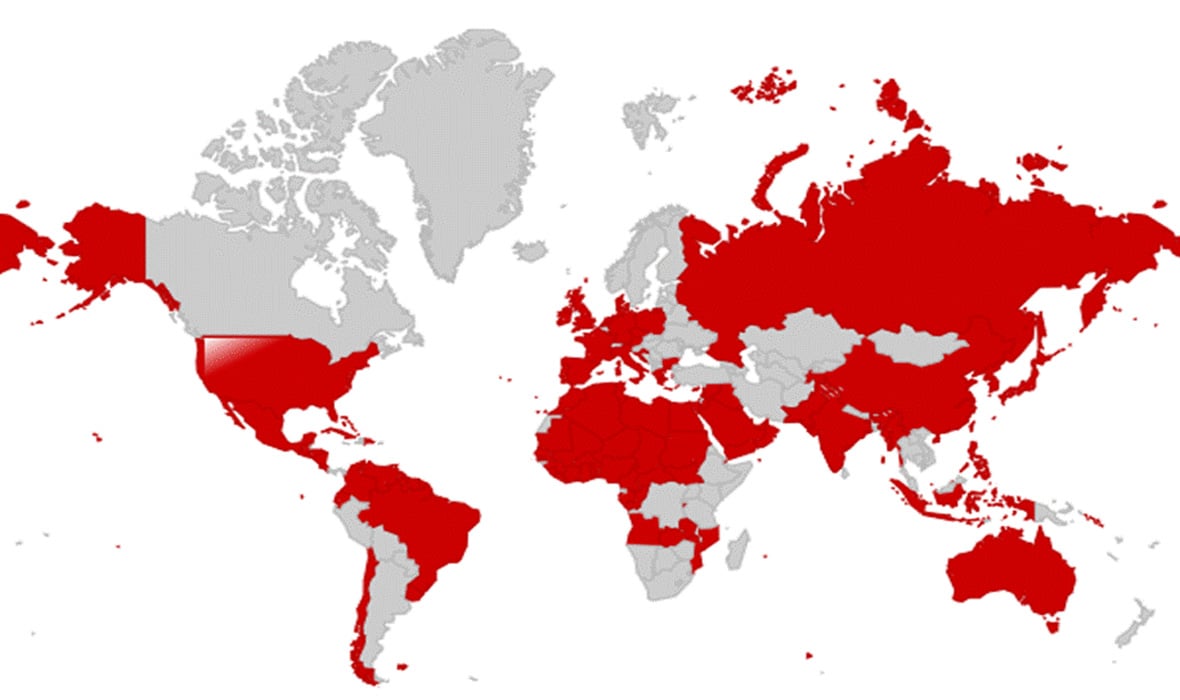
These promotions had been detected in 20+ languages, displaying extensive geographic focusing on and sufferer outreach.
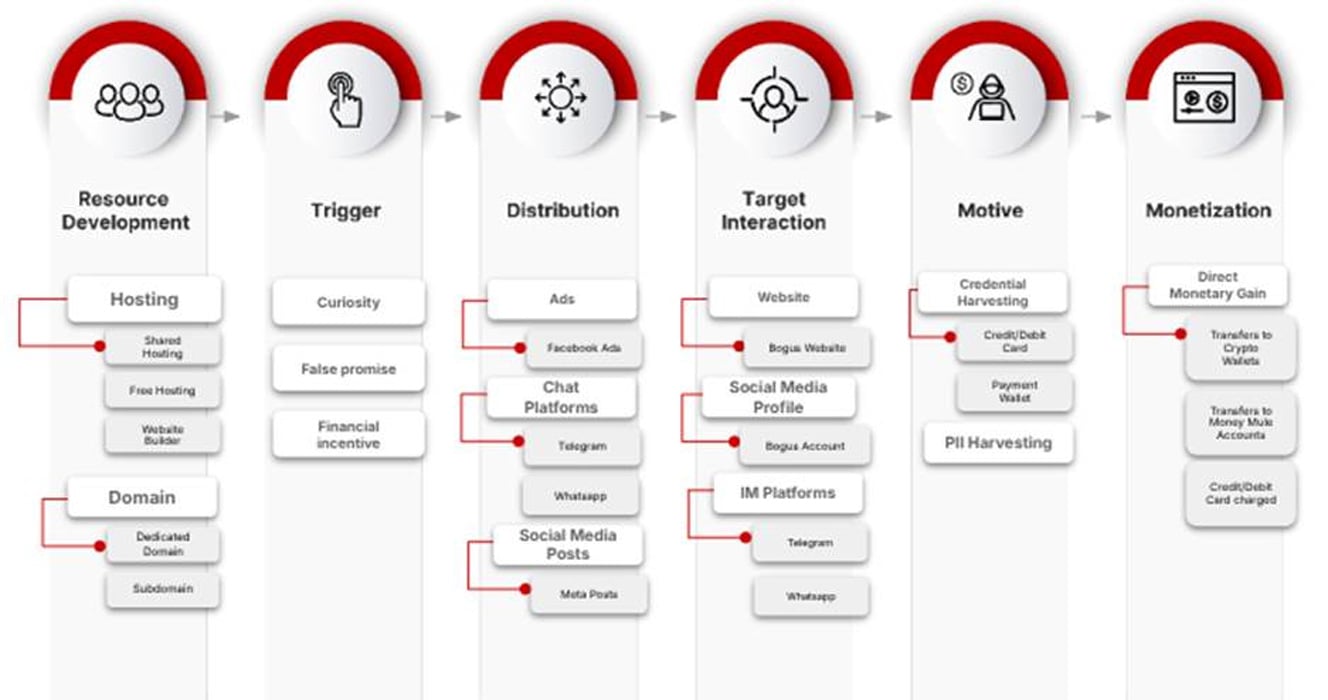
CTM360 maps this exercise utilizing its Fraud Navigator framework, impressed by MITRE, displaying a full lifecycle, from Useful resource improvement and Distribution to Motive and Monetization.
Faux “Licenses” and Recycled Templates Throughout A whole bunch of Websites
To look credible, HYIP web sites typically show:
- Cast worldwide requirements and licensing stamps
- Faux testimonials
- Fraudulent withdrawals and transaction histories
CTM360 famous that licensing particulars are steadily reused throughout a number of rip-off websites utilizing the identical templates. In a single case, the identical firm registration quantity and tackle appeared throughout 270+ websites, suggesting mass-produced rip-off infrastructure.
Referral Applications Flip Victims Into Distributors
A key progress lever in HYIPs is the referral mannequin, the place victims are pushed to ask others by means of guarantees of:
- bonus rewards
- elevated revenue charges
- referral commissions
This construction helps scams scale rapidly past paid advertisements into private networks.
Funds, KYC Delays, and the Exit Technique
Whereas cryptocurrency is usually used, CTM360 additionally noticed HYIPs accepting:
- credit score/debit playing cards
- native cost gateways
Many platforms additionally request KYC paperwork to “activate” accounts, then repeatedly declare the verification remains to be in progress to delay withdrawals and withhold funds.
The HYIP Lifecycle Ends the Similar Approach
HYIP scams comply with a predictable cycle: arrange pretend platforms, promote by means of social media, construct belief with fabricated outcomes, incentivize bigger deposits by means of referral schemes, after which collapse by blocking withdrawals and vanishing.
Learn the total report right here: https://www.ctm360.com/experiences/hyip-risk
Detect Cyber Threats 24/7 with CTM360
Monitor, analyze, and promptly mitigate dangers throughout your exterior digital panorama with the CTM360.
Be a part of our Neighborhood Version
Sponsored and written by CTM360.


