
Microsoft introduced that it’s going to disable the 30-year-old NTLM authentication protocol by default in upcoming Home windows releases on account of safety vulnerabilities that expose organizations to cyberattacks.
NTLM (brief for New Expertise LAN Supervisor) is a challenge-response authentication protocol launched in 1993 with Home windows NT 3.1 and is the successor to the LAN Supervisor (LM) protocol.
Kerberos has outmoded NTLM and is now the present default protocol for domain-connected units operating Home windows 2000 or later. Whereas it was the default protocol in older Home windows variations, NTLM continues to be used as we speak as a fallback authentication technique when Kerberos is unavailable, regardless that it makes use of weak cryptography and is susceptible to assaults.
Since its launch, NTLM has been broadly exploited in NTLM relay assaults (the place menace actors power compromised community units to authenticate in opposition to attacker-controlled servers) to escalate privileges and take full management over the Home windows area. Regardless of this, NTLM continues to be used on Home windows servers, permitting attackers to use vulnerabilities resembling PetitPotam, ShadowCoerce, DFSCoerce, and RemotePotato0 to bypass NTLM relay assault mitigations.
NTLM has additionally been focused by pass-the-hash assaults, through which cybercriminals exploit system vulnerabilities or deploy malicious software program to steal NTLM hashes (hashed passwords) from focused programs. These hashed passwords are used to authenticate because the compromised person, permitting the attackers to steal delicate knowledge and unfold laterally throughout the community.
“Blocked and not used routinely”
On Thursday, as a part of a broader push towards passwordless, phishing-resistant authentication strategies, Microsoft introduced that NTLM will lastly be disabled by default within the subsequent main Home windows Server launch and related Home windows shopper variations, marking a big shift away from the legacy protocol to safer Kerberos-based authentication.
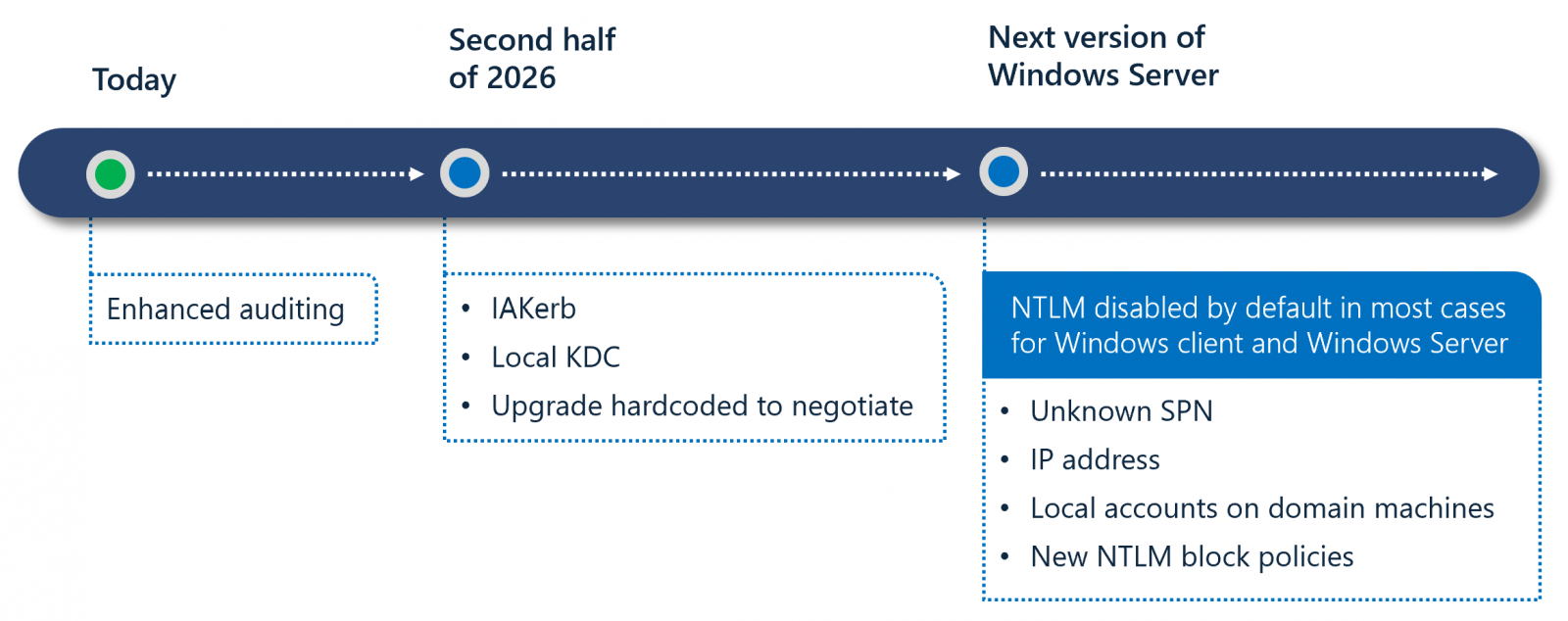
Microsoft additionally outlined a three-phase transition plan designed to mitigate NTLM-related dangers whereas minimizing disruption. In part one, admins will be capable to use enhanced auditing instruments obtainable in Home windows 11 24H2 and Home windows Server 2025 to establish the place NTLM continues to be in use.
Part two, scheduled for the second half of 2026, will introduce new options, resembling IAKerb and a Native Key Distribution Middle, to deal with widespread situations that set off NTLM fallback.
Part three will disable community NTLM by default in future releases, regardless that the protocol will stay current within the working system and may be explicitly re-enabled by way of coverage controls if wanted.
”Disabling NTLM by default doesn’t imply fully eradicating NTLM from Home windows but. As an alternative, it implies that Home windows will likely be delivered in a secure-by-default state the place community NTLM authentication is blocked and not used routinely,” Microsoft mentioned.
“The OS will choose fashionable, safer Kerberos-based options. On the identical time, widespread legacy situations will likely be addressed by way of new upcoming capabilities resembling Native KDC and IAKerb (pre-release).”
Microsoft first introduced plans to retire the NTLM authentication protocol in October 2023, noting that it additionally needed to broaden administration controls to provide directors better flexibility in monitoring and proscribing NTLM utilization inside their environments.
It additionally formally deprecated NTLM authentication on Home windows and Home windows servers in July 2024, advising builders to transition to Kerberos or Negotiation authentication to forestall future points.
Microsoft has been warning builders to cease utilizing NTLM of their apps since 2010 and advising Home windows admins to both disable NTLM or configure their servers to dam NTLM relay assaults utilizing Lively Listing Certificates Providers (AD CS).




