
A brand new Android malware marketing campaign is utilizing the Hugging Face platform as a repository for 1000’s of variations of an APK payload that collects credentials for standard monetary and fee companies.
Hugging Face is a well-liked platform that hosts and distributes synthetic intelligence (AI), pure language processing (NLP), and machine studying (ML) fashions, datasets, and functions.
It’s thought of a trusted platform unlikely to set off safety warnings, however dangerous actors have abused it up to now to host malicious AI fashions.
The latest marketing campaign found by researchers at Romanian cybersecurity firm Bitdefender leverages the platform to distribute Android malware.
The assault begins with victims being lured to put in a dropper app referred to as TrustBastion, which makes use of scareware-style advertisements claiming that the goal’s gadget is contaminated. The malicious app is disguised as a safety instrument, claiming to detect threats equivalent to scams, fraudulent SMS messages, phishing makes an attempt, and malware.
Instantly after set up, TrustBastion reveals a compulsory replace alert with visible components that mimic Google Play.
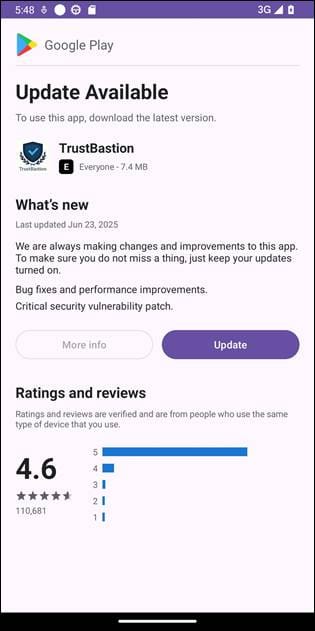
Supply: Bitdefender
As a substitute of instantly serving malware, the dropper contacts a server linked to trustbastion[.]com, which returns a redirect to a Hugging Face dataset repository internet hosting the malicious APK. The ultimate payload is downloaded from Hugging Face infrastructure and delivered by way of its content material distribution community (CDN).
To evade detection, the risk actor makes use of server-side polymorphism that generates new payload variants each quarter-hour, Bitdefender says.
“On the time of investigation, the repository was roughly 29 days previous and had gathered greater than 6,000 commits.”
Throughout evaluation, the payload-serving repository was taken down, however the operation resurfaced underneath a brand new identify, ‘Premium Membership,’ which used new icons whereas retaining the identical malicious code.
The primary payload, which lacks a reputation, is a distant entry instrument that aggressively exploits Android’s Accessibility Providers, presenting the request as essential for safety causes.
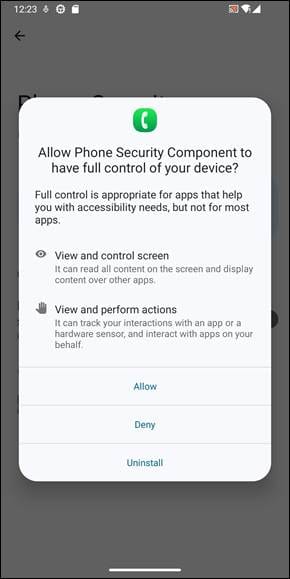
Supply: Bitdefender
This provides the malware the flexibility to serve display screen overlays, seize the person’s display screen, carry out swipes, block uninstallation makes an attempt, and extra.
On this case, Bitdefender says the malware screens person exercise and captures screenshots, exfiltrating every part to its operators. The malware additionally shows pretend login interfaces impersonating monetary companies equivalent to Alipay and WeChat to steal credentials, and likewise makes an attempt to steal the lock display screen code.
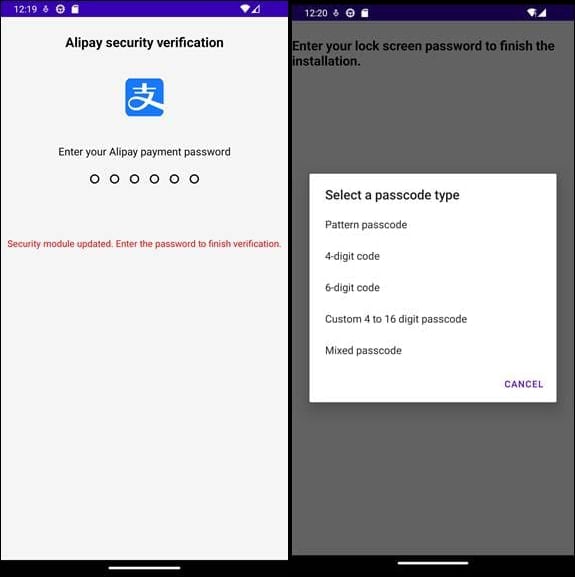
Supply: Bitdefender
The malware stays linked always to the command-and-control (C2) server, which receives the stolen knowledge, sends command execution directions, configuration updates, and likewise pushes pretend in-app content material to make TrustBastion seem reliable.
Bitdefender knowledgeable Hugging Face concerning the risk actor’s repository, and the service eliminated the datasets containing the malware. Researchers additionally printed a set of indicators of compromise for the dropper, the community, and malicious packages.
Android customers ought to keep away from downloading apps from third-party app shops or putting in them manually. They need to additionally assessment the permissions an app requests and guarantee all of them are essential for the app’s supposed performance.
It is finances season! Over 300 CISOs and safety leaders have shared how they’re planning, spending, and prioritizing for the yr forward. This report compiles their insights, permitting readers to benchmark methods, determine rising tendencies, and examine their priorities as they head into 2026.
Find out how high leaders are turning funding into measurable affect.




