
Okta is warning about customized phishing kits constructed particularly for voice-based social engineering (vishing) assaults. BleepingComputer has discovered that these kits are being utilized in lively assaults to steal Okta SSO credentials for knowledge theft.
In a brand new report launched as we speak by Okta, researchers clarify that the phishing kits are bought as a part of an “as a service” mannequin and are actively being utilized by a number of hacking teams to focus on id suppliers, together with Google, Microsoft, and Okta, and cryptocurrency platforms.
In contrast to typical static phishing pages, these adversary-in-the-middle platforms are designed for reside interplay through voice calls, permitting attackers to alter content material and show dialogs in actual time as a name progresses.
The core options of those phishing kits are real-time manipulation of targets by scripts that give the caller direct management over the sufferer’s authentication course of.
Because the sufferer enters credentials into the phishing web page, these credentials are forwarded to the attacker, who then makes an attempt to log in to the service whereas nonetheless on the decision.
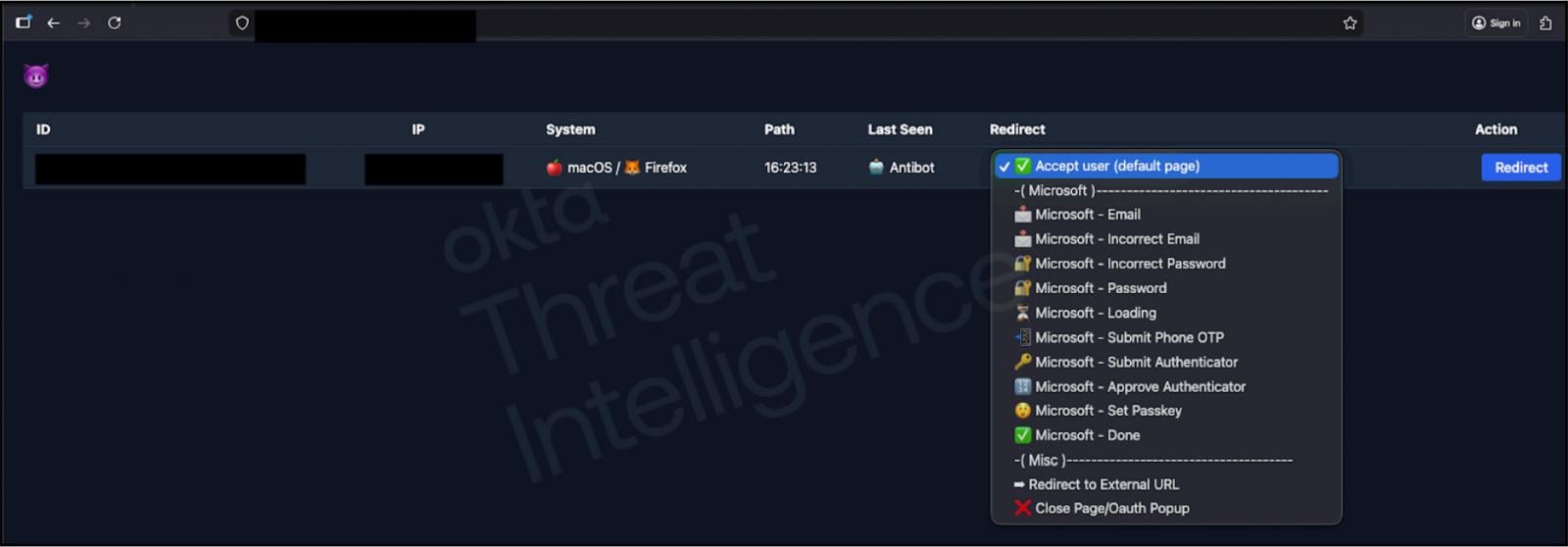
Supply: Okta
When the service responds with an MFA problem, akin to a push notification or OTP, the attacker can choose a brand new dialog that immediately updates the phishing web page to match what the sufferer sees when trying to log in. This synchronization makes fraudulent MFA requests seem official.
Okta says these assaults are extremely deliberate, with menace actors performing reconnaissance on a focused worker, together with which purposes they use and the telephone numbers related to their firm’s IT assist.
They then create custom-made phishing pages and name the sufferer utilizing spoofed company or helpdesk numbers. When the sufferer enters their username and password on the phishing web site, these credentials are relayed to the attacker’s backend, generally to Telegram channels operated by the menace actors.
This permits the attackers to right away set off actual authentication makes an attempt that show MFA challenges. Whereas the menace actors are nonetheless on the telephone with their goal, they’ll direct the particular person to enter their MFA TOTP codes on the phishing web site, that are then intercepted and used to log in to their accounts.
Okta says these platforms can bypass trendy push-based MFA, together with quantity matching, as a result of attackers inform victims which quantity to pick out. On the similar time, the phishing package C2 causes the web site to show an identical immediate within the browser.
Okta recommends that prospects use phishing-resistant MFA akin to Okta FastPass, FIDO2 safety keys, or passkeys.
Assaults used for knowledge theft
This advisory comes after BleepingComputer discovered that Okta privately warned its prospects’ CISOs earlier this week concerning the ongoing social engineering assaults.
On Monday, BleepingComputer contacted Okta after studying that menace actors had been calling focused firms’ staff to steal their Okta SSO credentials.
Okta is a cloud-based id supplier that acts as a central login system for lots of the most generally used enterprise internet providers and cloud platforms.
Its single sign-on (SSO) service permits staff to authenticate as soon as with Okta after which acquire entry to different platforms utilized by their firm with out having to log in once more.
Platforms that combine with Okta SSO embody Microsoft 365, Google Workspace, Dropbox, Salesforce, Slack, Zoom, Field, Atlassian Jira and Confluence, Coupa, and lots of extra.
As soon as logged in, Okta SSO customers are given entry to a dashboard that lists all of their firm’s providers and platforms, permitting them to click on and entry them. This makes Okta SSO act as a gateway to an organization’s business-wide providers.

Supply: Okta
On the similar time, this makes the platform extraordinarily precious for menace actors, who now have entry to the corporate’s extensively used cloud storage, advertising and marketing, growth, CRM, and knowledge analytics platforms.
BleepingComputer has discovered that the social engineering assaults start with menace actors calling staff and impersonating IT workers from their firm. The menace actors provide to assist the worker arrange passkeys for logging into the Okta SSO service.
The attackers trick staff into visiting a specifically crafted adversary-in-the-middle phishing web site that captures their SSO credentials and TOTP codes, with a number of the assaults relayed in actual time by a Socket.IO server beforehand hosted at inclusivity-team[.]onrender.com.
The phishing web sites are named after the corporate, and generally comprise the phrase “inside” or “my”.
For instance, if Google had been focused, the phishing websites could be named googleinternal[.] com or mygoogle[.]com.
As soon as an worker’s credentials are stolen, the attacker logs in to the Okta SSO dashboard to see which platforms they’ve entry to after which proceeds to steal knowledge from them.
“We gained unauthorized entry to your assets by utilizing a social-engineering-based phishing assault to compromise an worker’s SSO credentials,” reads a safety report despatched by the menace actors to the sufferer and seen by BleepingComputer.
“We contacted varied staff and satisfied one to offer their SSO credentials, together with TOTPs.”
“We then regarded by varied apps on the worker’s Okta dashboard that that they had entry to searching for ones that handled delicate info. We primarily exfiltrated from Salesforce as a consequence of how straightforward it’s to exfiltrate knowledge from Salesforce. We extremely counsel you to stray away from Salesforce, use one thing else.”
As soon as they’re detected, the menace actors instantly ship extortion emails to the corporate, demanding cost to stop the publication of information.
Sources inform BleepingComputer that a number of the extortion calls for despatched by the menace actors are signed by ShinyHunters, a well known extortion group behind a lot of final 12 months’s knowledge breaches, together with the widespread Salesforce knowledge theft assaults.
BleepingComputer requested ShinyHunters to substantiate in the event that they had been behind these assaults however they declined to remark.
Presently, BleepingComputer has been informed that the menace actors are nonetheless actively focusing on firms within the Fintech, Wealth administration, monetary, and advisory sectors.
Okta shared the next assertion with BleepingComputer concerning our questions on these assaults.
“Conserving prospects safe is our prime precedence. Okta’s Defensive Cyber Operations staff routinely identifies phishing infrastructure configured to mimic an Okta sign-in web page and proactively notifies distributors of their findings,” reads a press release despatched to BleepingComputer.
“It’s clear how refined and insidious phishing campaigns have develop into and it’s essential that firms take all crucial measures to safe their programs and proceed to coach their staff on vigilant safety finest practices.”
“We offer our prospects finest practices and sensible steering to assist them establish and forestall social engineering assaults, together with the suggestions detailed on this safety weblog https://www.okta.com/weblog/threat-intelligence/help-desks-targeted-in-social-engineering-targeting-hr-applications/ and the weblog we revealed as we speak https://www.okta.com/weblog/threat-intelligence/phishing-kits-adapt-to-the-script-of-callers/.”




