ESET Analysis has been monitoring assaults involving the just lately found ToolShell zero-day vulnerabilities
24 Jul 2025
•
,
5 min. learn

On July 19th, 2025, Microsoft confirmed {that a} set of zero-day vulnerabilities in SharePoint Server referred to as ToolShell is being exploited within the wild. ToolShell is comprised of CVE-2025-53770, a distant code execution vulnerability, and CVE‑2025‑53771, a server spoofing vulnerability. These assaults goal on-premises Microsoft SharePoint servers, particularly these working SharePoint Subscription Version, SharePoint 2019, or SharePoint 2016. SharePoint On-line in Microsoft 365 will not be impacted. Exploiting these vulnerabilities permits risk actors to achieve entry to restricted techniques and steal delicate data.
Ranging from July 17th, ToolShell has been extensively exploited by all kinds of risk actors, from petty cybercriminals to nation-state APT teams. Since SharePoint is built-in with different Microsoft providers, akin to Workplace, Groups, OneDrive, and Outlook, this compromise can present the attackers a staggering stage of entry throughout the affected community.
As a part of the assault, the risk actors typically chain collectively 4 vulnerabilities: the beforehand patched CVE‑2025‑49704 and CVE-2025-49706, alongside the already talked about CVE-2025-53770 and CVE-2025-53771. As of July 22, CVE‑2025‑53770 and CVE-2025-53771 have additionally been patched.
Webshell payloads
Exploiting ToolShell permits the attackers to bypass multi-factor authentication (MFA), and single sign-on (SSO). After getting contained in the focused server, attackers had been seen deploying malicious webshells to extract data from the compromised system. One of many scripts steadily used for this objective is called spinstall0.aspx, which we monitor as MSIL/Webshell.JS.
Moreover, on July 22nd, 2025, we noticed that attackers tried to deploy different easy ASP webshells able to executing attacker-supplied instructions by way of cmd.exe. These webshells had been deployed utilizing the next filenames: ghostfile346.aspx, ghostfile399.aspx, ghostfile807.aspx, ghostfile972.aspx, and ghostfile913.aspx.
ESET merchandise first detected an try to take advantage of a part of the execution chain – the Sharepoint/Exploit.CVE-2025-49704 vulnerability – on July 17th in Germany. Nonetheless, as a result of this try was blocked, the ultimate webshell payload was not delivered to the focused system. The primary time we registered the payload itself was on July 18th on a server in Italy. As seen in Determine 1, we now have since noticed lively ToolShell exploitation all around the world, with the US (13.3% of assaults) being probably the most focused nation in line with our telemetry knowledge.
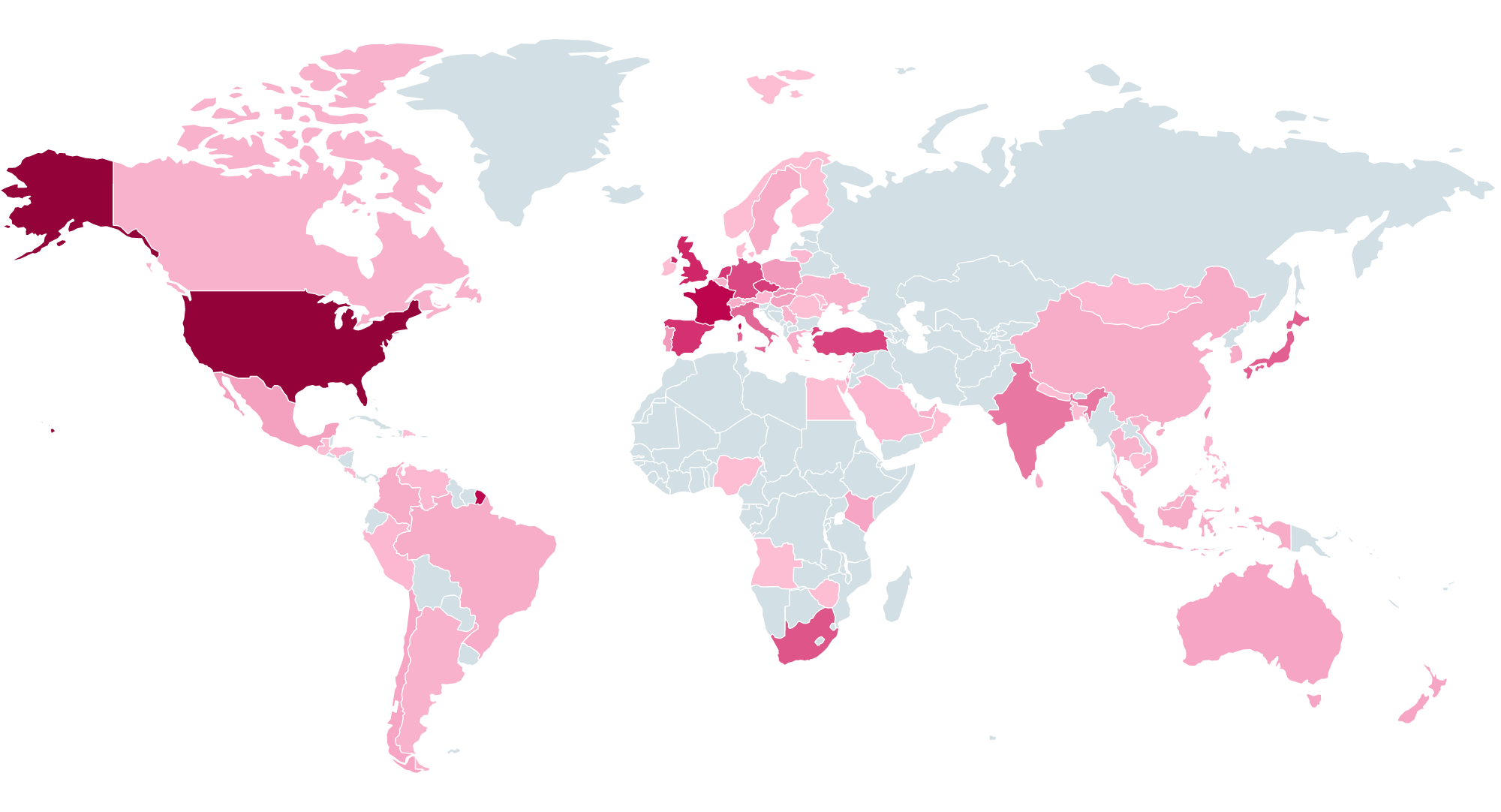
Assault monitoring
Our monitoring of the ToolShell assaults from July 17th to July 22nd revealed that they had been coming from the IP addresses proven in Desk 1 (all instances are in UTC).
Desk 1. Attacker IP addresses
| IP tackle | Assault begin date | Assault finish date |
| 96.9.125[.]147 | 2025-07-17 09:00 | 2025-07-17 16:00 |
| 107.191.58[.]76 | 2025-07-18 14:00 | 2025-07-18 20:00 |
| 104.238.159[.]149 | 2025-07-19 04:00 | 2025-07-19 09:00 |
| 139.59.11[.]66 | 2025-07-21 11:00 | 2025-07-21 16:00 |
| 154.223.19[.]106 | 2025-07-21 13:00 | 2025-07-22 18:00 |
| 103.151.172[.]92 | 2025-07-21 14:00 | 2025-07-21 16:00 |
| 45.191.66[.]77 | 2025-07-21 14:00 | 2025-07-22 07:00 |
| 83.136.182[.]237 | 2025-07-21 14:00 | 2025-07-21 16:00 |
| 162.248.74[.]92 | 2025-07-21 14:00 | 2025-07-21 17:00 |
| 38.54.106[.]11 | 2025-07-21 15:00 | 2025-07-21 15:00 |
| 206.166.251[.]228 | 2025-07-21 16:00 | 2025-07-22 16:00 |
| 45.77.155[.]170 | 2025-07-21 16:00 | 2025-07-21 19:00 |
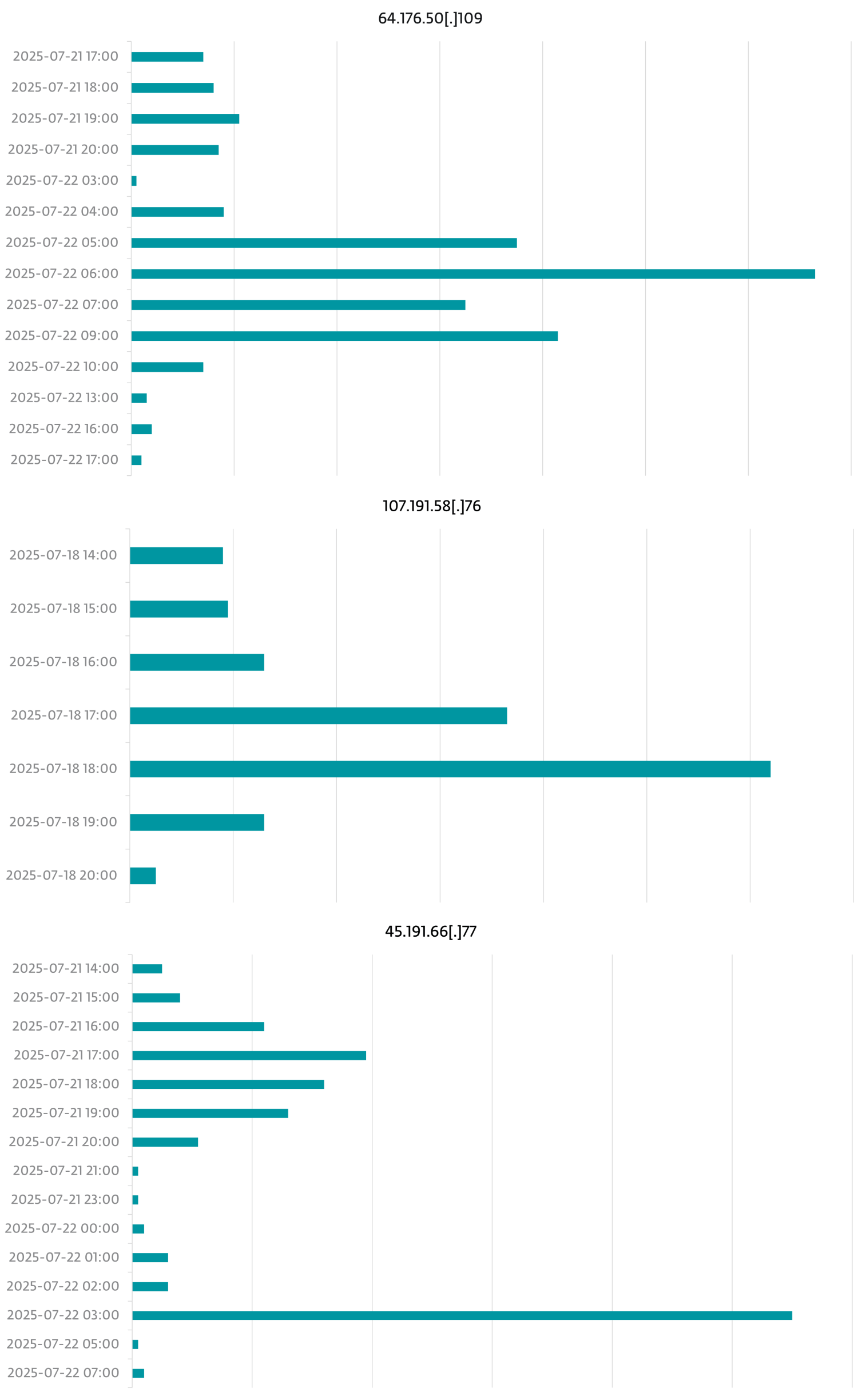
| 64.176.50[.]109 | 2025-07-21 17:00 | 2025-07-22 17:00 |
| 149.28.17[.]188 | 2025-07-22 03:00 | 2025-07-22 03:00 |
| 173.239.247[.]32 | 2025-07-22 05:00 | 2025-07-22 05:00 |
| 109.105.193[.]76 | 2025-07-22 05:00 | 2025-07-22 16:00 |
| 2.56.190[.]139 | 2025-07-22 06:00 | 2025-07-22 07:00 |
| 141.164.60[.]10 | 2025-07-22 07:00 | 2025-07-22 18:00 |
| 124.56.42[.]75 | 2025-07-22 13:00 | 2025-07-22 18:00 |
Determine 2 reveals the timeline of the assaults coming from the three most lively IP addresses.
Concerningly, Microsoft has reported that a number of China-aligned risk actors have joined in on the exploitation makes an attempt. From our facet, we detected a backdoor related to LuckyMouse – a cyberespionage group that targets primarily governments, telecommunications corporations, and worldwide organizations – on a machine in Vietnam focused by way of ToolShell. At this stage, it stays unclear whether or not the system had been beforehand compromised or if the backdoor was launched throughout the present assault.
However, China-aligned APT teams have definitely seized the chance so as to add the exploit chain to their arsenals: in line with our telemetry, the victims of the ToolShell assaults embrace a number of high-value authorities organizations which have been long-standing targets of those teams.
Because the cat is out of the bag now, we count on many extra opportunistic attackers to make the most of unpatched techniques. The exploit makes an attempt are ongoing and can absolutely proceed. Due to this fact, if you’re utilizing SharePoint Server, the next is beneficial (as per steering from Microsoft):
- use solely supported variations,
- apply the newest safety updates,
- be sure that Antimalware Scan Interface is turned on and configured correctly, with an acceptable cybersecurity answer, and
- rotate SharePoint Server ASP.NET machine keys.
For any inquiries about our analysis revealed on WeLiveSecurity, please contact us at threatintel@eset.com.ESET Analysis gives non-public APT intelligence stories and knowledge feeds. For any inquiries about this service, go to the ESET Menace Intelligence web page.
IoCs
A complete listing of indicators of compromise (IoCs) and samples will be present in our GitHub repository.
Recordsdata
| SHA-1 | Filename | Detection | Description |
| F5B60A8EAD96703080E7 | spinstall0.aspx | MSIL/Webshell.JS | Webshell deployed by way of SharePoint vulnerabilities |
Community
| IP | Area | Internet hosting supplier | First seen | Particulars |
| 96.9.125[.]147 | N/A | BL Networks | 2025-07-17 | IP tackle exploiting SharePoint vulnerabilities. |
| 107.191.58[.]76 | N/A | The Fixed Firm, LLC | 2025-07-18 | IP tackle exploiting SharePoint vulnerabilities. |
| 104.238.159[.]149 | N/A | The Fixed Firm, LLC | 2025-07-19 | IP tackle exploiting SharePoint vulnerabilities. |
| 139.59.11[.]66 | N/A | DigitalOcean, LLC | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 154.223.19[.]106 | N/A | Kaopu Cloud HK Restricted | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 103.151.172[.]92 | N/A | IKUUU NETWORK LTD | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 45.191.66[.]77 | N/A | VIACLIP INTERNET E TELECOMUNICAÇÕES LTDA | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 83.136.182[.]237 | N/A | Alina Gatsaniuk | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 162.248.74[.]92 | N/A | xTom GmbH | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 38.54.106[.]11 | N/A | Kaopu Cloud HK Restricted | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 206.166.251[.]228 | N/A | BL Networks | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 45.77.155[.]170 | N/A | Vultr Holdings, LLC | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 64.176.50[.]109 | N/A | The Fixed Firm, LLC | 2025-07-21 | IP tackle exploiting SharePoint vulnerabilities. |
| 149.28.17[.]188 | N/A | The Fixed Firm, LLC | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
| 173.239.247[.]32 | N/A | GSL Networks Pty LTD | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
| 109.105.193[.]76 | N/A | Haruka Community Restricted | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
| 2.56.190[.]139 | N/A | Alina Gatsaniuk | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
| 141.164.60[.]10 | N/A | The Fixed Firm, LLC | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
| 124.56.42[.]75 | N/A | IP Supervisor | 2025-07-22 | IP tackle exploiting SharePoint vulnerabilities. |
MITRE ATT&CK strategies
This desk was constructed utilizing model 17 of the MITRE ATT&CK framework.
| Tactic | ID | Title | Description |
| Preliminary Entry | T1190 | Exploit Public-Going through Software | Menace actors exploited CVE-2025-49704, CVE-2025-49706, CVE-2025-53770, and CVE‑2025-53771 to compromise on-premises Microsoft SharePoint servers. |
| Execution | T1059.003 | Command and Scripting Interpreter: Home windows Command Shell | The deployed webshells execute attacker-supplied instructions by way of cmd.exe. |
| Persistence | T1505.003 | Server Software program Part: Net Shell | Menace actors deployed webshells to compromised servers. |
| Assortment | T1005 | Knowledge from Native System | The deployed webshells permit the attackers to extract data from the compromised techniques. |





