
The newest variant of the MacSync info stealer concentrating on macOS programs is delivered by way of a digitally signed, notarized Swift utility.
Safety researchers at Apple gadget administration platform Jamf say that the distribution methodology constitutes a big evolution from previous iterations that used much less subtle “drag-to-Terminal” or ClickFix techniques.
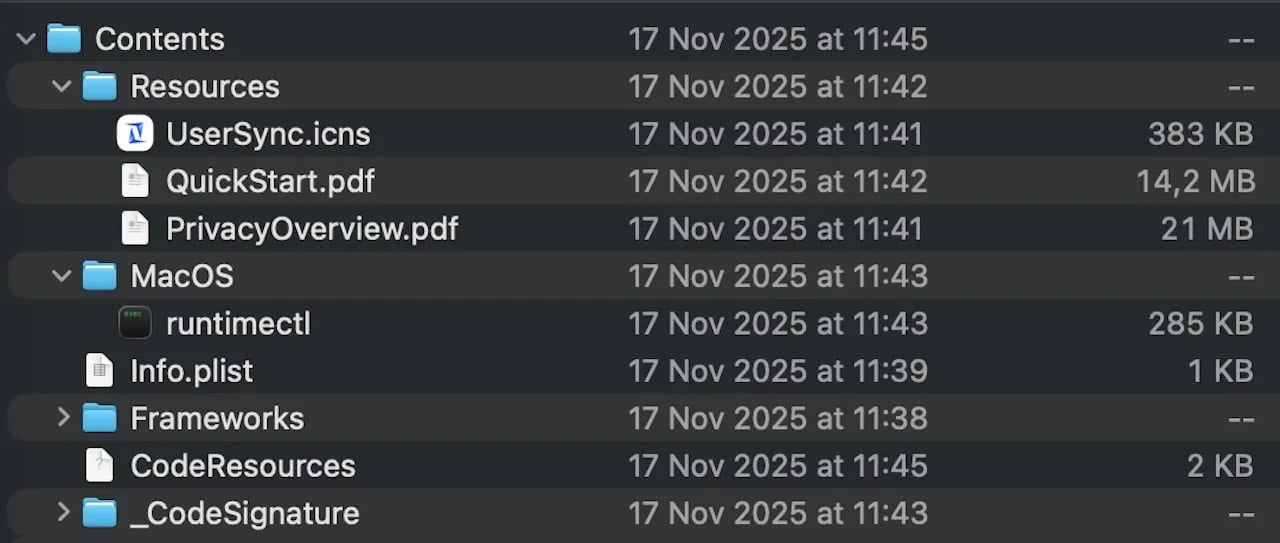
“Delivered as a code-signed and notarized Swift utility inside a disk picture named zk-call-messenger-installer-3.9.2-lts.dmg, distributed through https://zkcall.internet/obtain, it removes the necessity for any direct terminal interplay,” the researchers say in a report immediately.

Supply: Jamf
On the time of the evaluation, Jamf says that the most recent MacSync variant had a sound signature and will bypass checks from Gatekeeper, the safety system in macOS.
“After inspecting the Mach-O binary, which is a common construct, we confirmed that it’s each code-signed and notarized. The signature is related to the Developer Workforce ID GNJLS3UYZ4,” Jamf explains.
Nonetheless, following a direct report of the certificates to Apple, it has now been revoked.
The malware is delivered on the system by way of a dropper in encoded type. After decoding the payload, researchers found the same old indicators of the MacSync Stealer.
.jpg)
Supply: Jamf
The researchers famous that the stealer options a number of evasion mechanisms, together with inflating the DMG file to 25.5MB by embedding decoy PDFs, wiping the scripts used within the execution chain, and performing web connectivity checks earlier than execution to evade sandboxed environments.
Supply: Jamf
The stealer emerged in April 2025 as Mac.C by a menace actor named ‘Mentalpositive’. It gained traction by July, becoming a member of the much less crowded however nonetheless worthwhile house of macOS stealers alongside AMOS and Odyssey.
A earlier evaluation of Mac.C by MacPaw Moonlock signifies that it could steal iCloud keychain credentials, passwords saved on internet browsers, system metadata, cryptocurrency pockets information, and recordsdata from the filesystem.
Curiously, in an interview that Mentalpositive gave to researcher g0njxa in September, the malware creator acknowledged that the introduction of a tighter app notarization coverage in macOS 10.14.5 and later had the strongest affect on their growth plans, which is mirrored within the newest variations caught within the wild.
Damaged IAM is not simply an IT downside – the influence ripples throughout your complete enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with trendy calls for, examples of what “good” IAM seems to be like, and a easy guidelines for constructing a scalable technique.




