
Over the weekend, Google’s risk intelligence workforce linked 5 extra Chinese language hacking teams to assaults exploiting the maximum-severity “React2Shell” distant code execution vulnerability.
Tracked as CVE-2025-55182, this actively exploited flaw impacts the React open-source JavaScript library and permits unauthenticated attackers to execute arbitrary code in React and Subsequent.js purposes with a single HTTP request.
Whereas a number of React packages (i.e., react-server-dom-parcel, react-server-dom-turbopack, and react-server-dom-webpack) are weak of their default configurations, the vulnerability solely impacts React variations 19.0, 19.1.0, 19.1.1, and 19.2.0 launched over the previous 12 months.
After the assaults started, Palo Alto Networks reported that dozens of organizations had been breached, together with incidents linked to Chinese language state-backed risk actors. The attackers are exploiting the flaw to execute instructions and steal AWS configuration information, credentials, and different delicate data.
The Amazon Internet Companies (AWS) safety workforce additionally warned that the China-linked Earth Lamia and Jackpot Panda risk actors had begun exploiting React2Shell inside hours of the vulnerability’s disclosure.
5 extra Chinese language hacking teams linked to assaults
On Saturday, the Google Risk Intelligence Group (GTIG) reported detecting a minimum of 5 extra Chinese language cyber-espionage teams becoming a member of ongoing React2Shell assaults that began after the flaw was disclosed on December 3.
The record of state-linked risk teams exploiting the flaw now additionally contains UNC6600 (which deployed MINOCAT tunneling software program), UNC6586 (the SNOWLIGHT downloader), UNC6588 (the COMPOOD backdoor payload), UNC6603 (an up to date model of the HISONIC backdoor), and UNC6595 (ANGRYREBEL.LINUX Distant Entry Trojan).
“On account of using React Server Parts (RSC) in standard frameworks like Subsequent.js, there are a big variety of uncovered methods weak to this subject,” GTIG researchers mentioned.
“GTIG has additionally noticed quite a few discussions concerning CVE-2025-55182 in underground boards, together with threads by which risk actors have shared hyperlinks to scanning instruments, proof-of-concept (PoC) code, and their experiences utilizing these instruments.”
Whereas investigating these assaults, GTIG additionally noticed Iranian risk actors focusing on the flaw and financially motivated attackers deploying XMRig cryptocurrency mining software program on unpatched methods.
Shadowserver Web watchdog group is presently monitoring over 116,000 IP addresses weak to React2Shell assaults, with over 80,000 in the US.
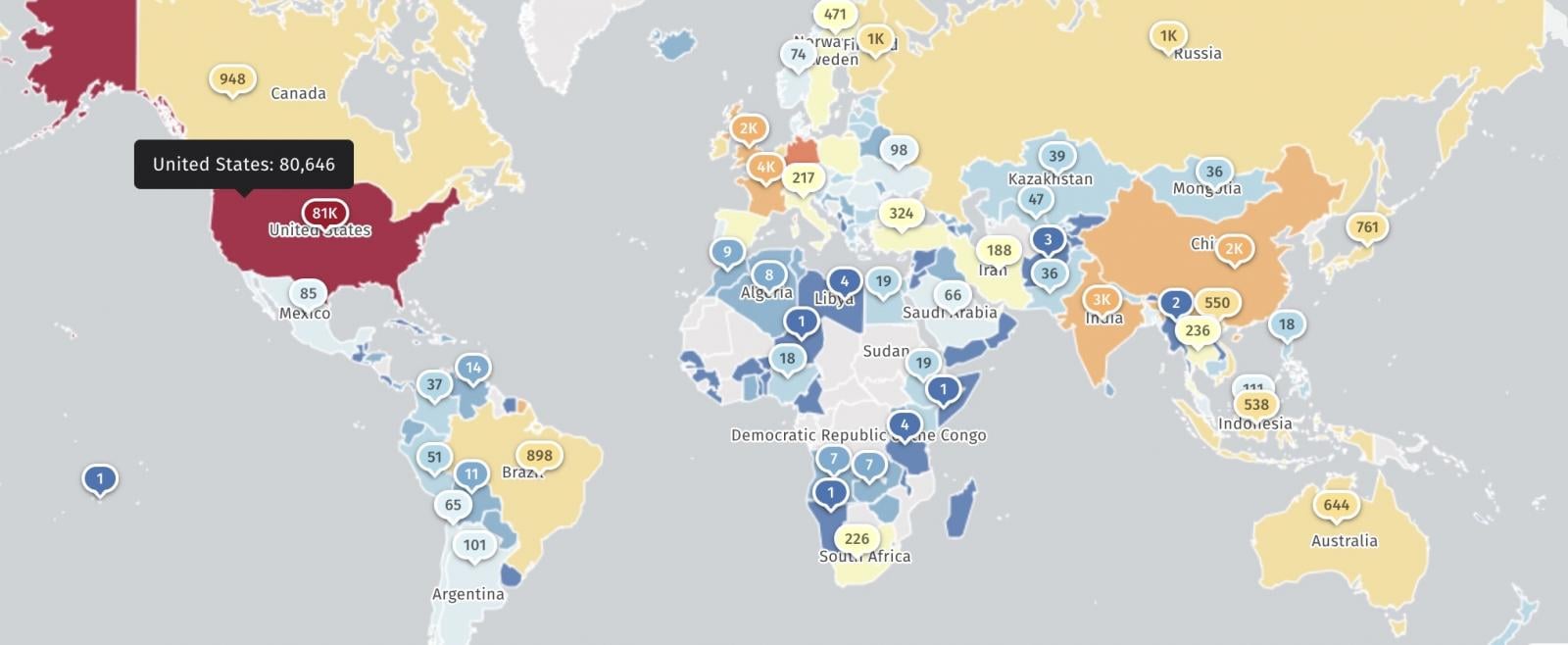
GreyNoise has additionally noticed over 670 IP addresses trying to take advantage of the React2Shell distant code execution flaw over the previous 24 hours, primarily originating from the US, India, France, Germany, the Netherlands, Singapore, Russia, Australia, the UK, and China.
On December 5, Cloudflare linked a international web site outage to emergency mitigations for the React2Shell vulnerability.
Damaged IAM is not simply an IT downside – the influence ripples throughout your entire enterprise.
This sensible information covers why conventional IAM practices fail to maintain up with fashionable calls for, examples of what “good” IAM appears to be like like, and a easy guidelines for constructing a scalable technique.



