One of many unhappy truths about this world of seemingly countless hacks and information breaches is that corporations simply will not apologise.
Even when prospects, companions, and staff are left questioning when their information will probably be revealed by malicious hackers on the darkish internet, breached organisations will seemingly do every part they’ll to keep away from saying what appears to be the toughest phrase of all: sorry.
Hacked companies will stall, waffle, and conceal behind phrases like “out of an abundance of warning” and “we take your safety and beforehand severely.”
What they usually is not going to do is admit they goofed up, confess to their errors, and promise to make issues higher.
It is as if attorneys whispering of their ears to “admit nothing” in concern of a category motion swimsuit has gained, and by no means thoughts constructing belief along with your shoppers, enterprise companions, and employees.
And the unhappy reality is that each hour of hiding behind bland safety advisories about “incidents” damages belief excess of a transparent apology ever would.
Which is why I discovered it so refreshing to learn a weblog publish by cost processing service Checkout.com.
It seems that the ShinyHunters hacking group are accountable for a heist which accessed information from a legacy third-party cloud storage system operated by Checkout.com.
In line with Mariano Albera, CTO of Checkout.com, it’s thought that “lower than 25%” of the corporate’s present service provider base was affected by the information breach of a system that “was used for inside operational paperwork and service provider onboarding supplies at the moment.”
Properly, it’s definitely excellent news to listen to that it was not Checkout.com’s stay cost platform that was compromised, and cost card info was not taken by the hackers, and that as an alternative it was an previous system used “in 2020 and prior.”
Checkout.com obtained a ransom demand from the hackers (who had exfitrated information somewhat than encrypted it), who threatened to publish the stolen info on the darkish internet if cost was not obtained.
It was Checkout.com’s response that I actually appreciated, and that’s so uncommon to listen to from hacked companies as we speak. Checkout.com did not give excuses. As a substitute, it publicly disclosed the incident, and apologised,
Sure, they really stated the phrase “sorry.”
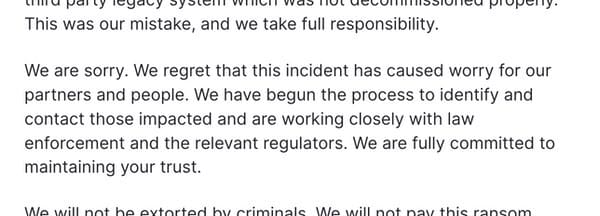
This was our mistake, and we take full accountability. We’re sorry.
Wow – that feels good to listen to!
However Checkout.com went additional…
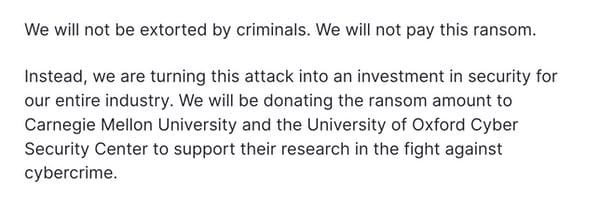
We is not going to be extorted by criminals. We is not going to pay this ransom… We will probably be donating ransom quantity to Carnegie Mellon College and the College of Oxford Safety Middle to assist their analysis within the battle towards cybercrime.
How sensible is that? And what an excellent distinction to the everyday “We’re investigating,” “We take safety severely,” and “We now have no additional remark presently…”
However good as that is, let’s not get carried away simply but.
As a result of the uncomfortable reality is that though Checkout.com communicated rapidly amd clearly, and took accountability for what had occurred, it doesn’t erase their safety failure.
The info was discovered by the hackers on a legacy system that the corporate had seemingly not used since 2020. Legacy methods are a legal responsibility – typically left nonetheless accessible, unmonitored, misconfigured, and unpatched.
Finally the explanation that this information breach occurred was as a result of a legacy information storage system had not been absolutely decomissioned. For all of the plaudits I’m giving Checkout.com for its dealing with of the breach, there’s nonetheless proof of a course of failure.
Different corporations can keep away from falling into the sort of situation themselves by on the lookout for potential issues earlier than they’re discovered by malicious hackers.
As a substitute of ready for incidents to happen, safety groups ought to conduct pre-mortem workout routines – exploring what methods exist that groups have forgotten about, which legacy platforms nonetheless have legitimate credentials, what could be best for an attacker to search out, and what information exists in methods which at present fall exterior safety monitoring.
Be extra proactive in your angle to securing your information, determine the vulnerabilities earlier than they change into breaches, and your organization will not be the one questioning if it’s time to say “sorry” or not.