A prolific cybercriminal group that calls itself “Scattered LAPSUS$ Hunters” has dominated headlines this yr by recurrently stealing knowledge from and publicly mass extorting dozens of main firms. However the tables appear to have turned considerably for “Rey,” the moniker chosen by the technical operator and public face of the hacker group: Earlier this week, Rey confirmed his actual life identification and agreed to an interview after KrebsOnSecurity tracked him down and contacted his father.
Scattered LAPSUS$ Hunters (SLSH) is considered an amalgamation of three hacking teams — Scattered Spider, LAPSUS$ and ShinyHunters. Members of those gangs hail from lots of the identical chat channels on the Com, a principally English-language cybercriminal group that operates throughout an ocean of Telegram and Discord servers.
In Might 2025, SLSH members launched a social engineering marketing campaign that used voice phishing to trick targets into connecting a malicious app to their group’s Salesforce portal. The group later launched a knowledge leak portal that threatened to publish the inner knowledge of three dozen corporations that allegedly had Salesforce knowledge stolen, together with Toyota, FedEx, Disney/Hulu, and UPS.
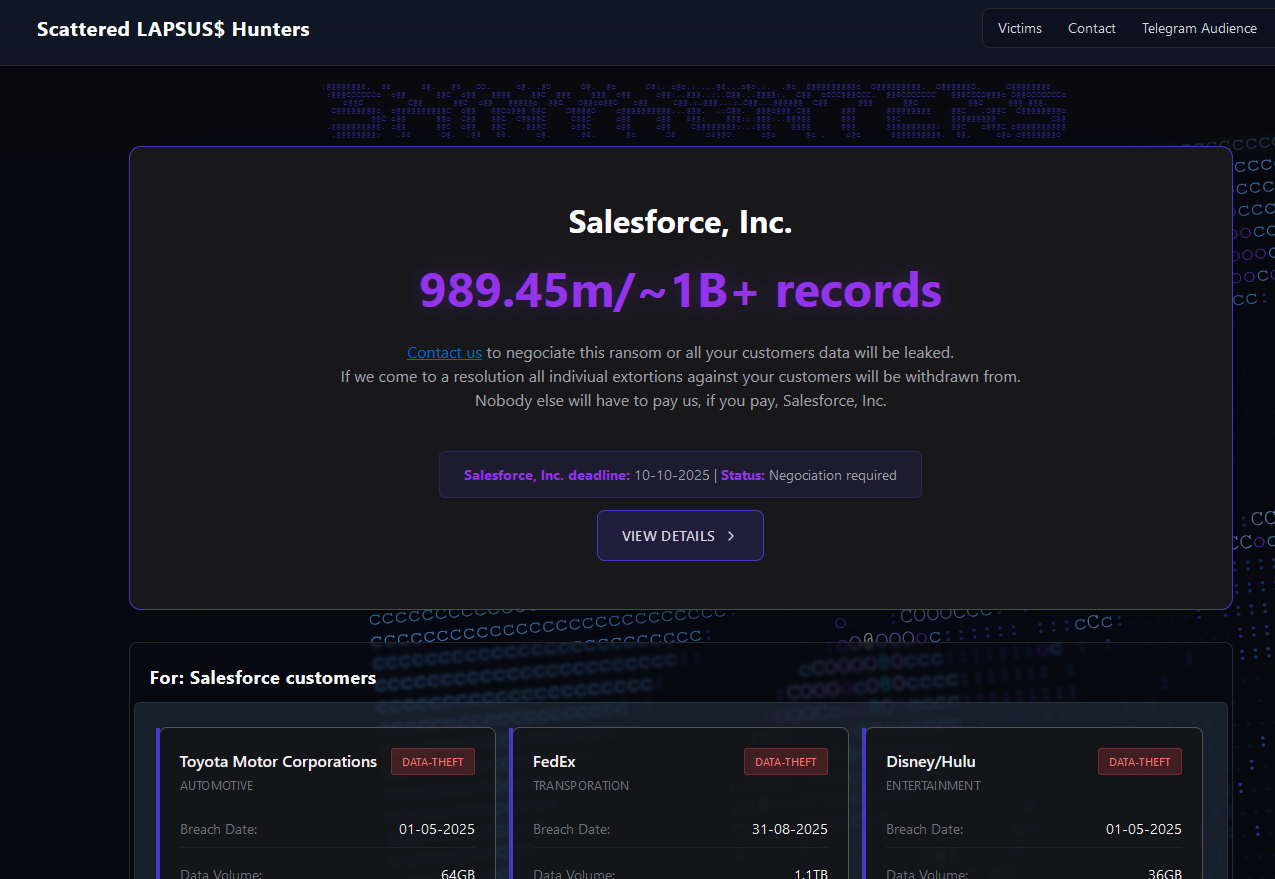
The brand new extortion web site tied to ShinyHunters, which threatens to publish stolen knowledge except Salesforce or particular person sufferer corporations comply with pay a ransom.
Final week, the SLSH Telegram channel featured a suggestion to recruit and reward “insiders,” staff at massive corporations who comply with share inner entry to their employer’s community for a share of no matter ransom cost is finally paid by the sufferer firm.
SLSH has solicited insider entry beforehand, however their newest name for disgruntled staff began making the rounds on social media on the identical time information broke that the cybersecurity agency Crowdstrike had fired an worker for allegedly sharing screenshots of inner programs with the hacker group (Crowdstrike mentioned their programs have been by no means compromised and that it has turned the matter over to legislation enforcement companies).
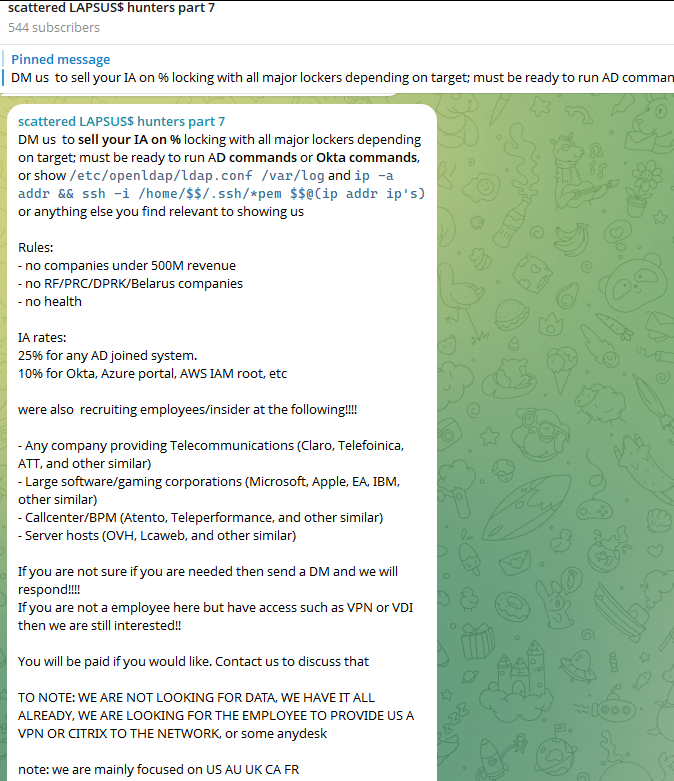
The Telegram server for the Scattered LAPSUS$ Hunters has been making an attempt to recruit insiders at massive corporations.
Members of SLSH have historically used different ransomware gangs’ encryptors in assaults, together with malware from ransomware affiliate packages like ALPHV/BlackCat, Qilin, RansomHub, and DragonForce. However final week, SLSH introduced on its Telegram channel the discharge of their very own ransomware-as-a-service operation known as ShinySp1d3r.
The person chargeable for releasing the ShinySp1d3r ransomware providing is a core SLSH member who goes by the deal with “Rey” and who’s at the moment one in every of simply three directors of the SLSH Telegram channel. Beforehand, Rey was an administrator of the information leak web site for Hellcat, a ransomware group that surfaced in late 2024 and was concerned in assaults on corporations together with Schneider Electrical, Telefonica, and Orange Romania.
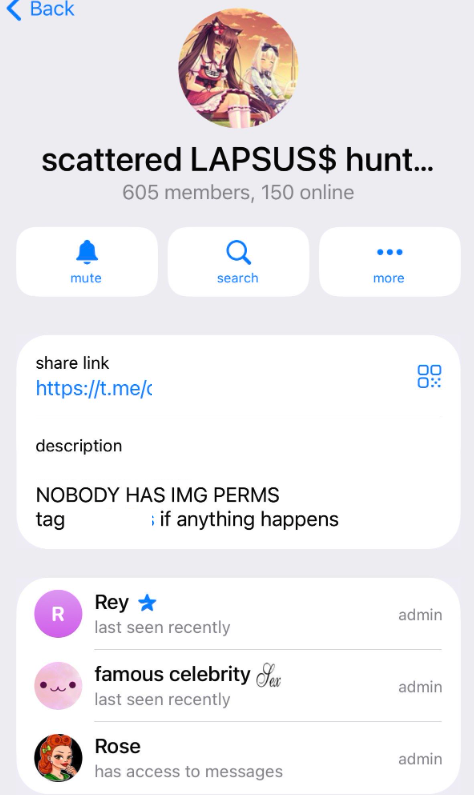
A current, barely redacted screenshot of the Scattered LAPSUS$ Hunters Telegram channel description, displaying Rey as one in every of three directors.
Additionally in 2024, Rey would take over as administrator of the most up-to-date incarnation of BreachForums, an English-language cybercrime discussion board whose domains have been seized on a number of events by the FBI and/or by worldwide authorities. In April 2025, Rey posted on Twitter/X about one other FBI seizure of BreachForums.
On October 5, 2025, the FBI introduced it had as soon as once more seized the domains related to BreachForums, which it described as a significant felony market utilized by ShinyHunters and others to visitors in stolen knowledge and facilitate extortion.
“This takedown removes entry to a key hub utilized by these actors to monetize intrusions, recruit collaborators, and goal victims throughout a number of sectors,” the FBI mentioned.
Extremely, Rey would make a collection of important operational safety errors final yr that offered a number of avenues to determine and ensure his real-life identification and site. Learn on to study the way it all unraveled for Rey.
WHO IS REY?
In response to the cyber intelligence agency Intel 471, Rey was an lively consumer on numerous BreachForums reincarnations over the previous two years, authoring greater than 200 posts between February 2024 and July 2025. Intel 471 says Rey beforehand used the deal with “Hikki-Chan” on BreachForums, the place their first publish shared knowledge allegedly stolen from the U.S. Facilities for Illness Management and Prevention (CDC).
In that February 2024 publish concerning the CDC, Hikki-Chan says they might be reached on the Telegram username @wristmug. In Might 2024, @wristmug posted in a Telegram group chat known as “Pantifan” a duplicate of an extortion electronic mail they mentioned they obtained that included their electronic mail deal with and password.
The message that @wristmug lower and pasted seems to have been a part of an automated electronic mail rip-off that claims it was despatched by a hacker who has compromised your laptop and used your webcam to document a video of you when you have been watching porn. These missives threaten to launch the video to all of your contacts except you pay a Bitcoin ransom, and so they usually reference an actual password the recipient has used beforehand.
“Noooooo,” the @wristmug account wrote in mock horror after posting a screenshot of the rip-off message. “I have to be executed guys.”
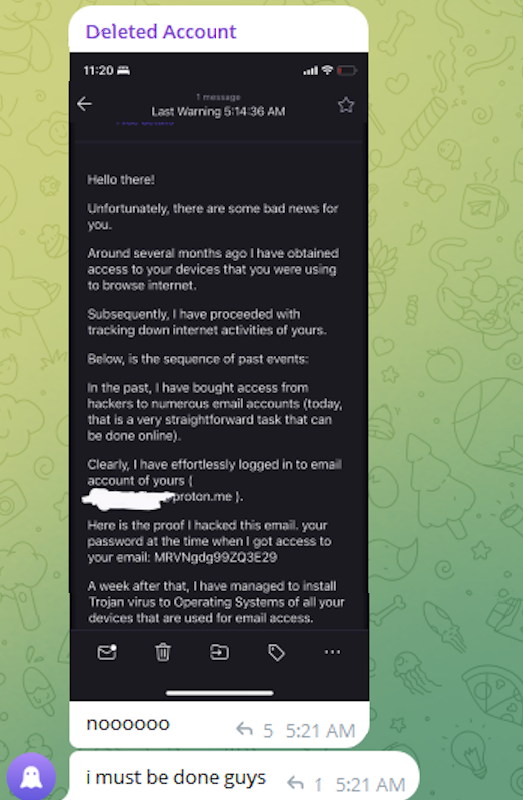
A message posted to Telegram by Rey/@wristmug.
In posting their screenshot, @wristmug redacted the username portion of the e-mail deal with referenced within the physique of the rip-off message. Nonetheless, they didn’t redact their previously-used password, and so they left the area portion of their electronic mail deal with (@proton.me) seen within the screenshot.
O5TDEV
Looking out on @wristmug’s reasonably distinctive 15-character password within the breach monitoring service Spycloud finds it’s recognized to have been utilized by only one electronic mail deal with: cybero5tdev@proton.me. In response to Spycloud, these credentials have been uncovered at the least twice in early 2024 when this consumer’s gadget was contaminated with an infostealer trojan that siphoned all of its saved usernames, passwords and authentication cookies (a discovering that was initially revealed in March 2025 by the cyber intelligence agency KELA).
Intel 471 exhibits the e-mail deal with cybero5tdev@proton.me belonged to a BreachForums member who glided by the username o5tdev. Looking out on this nickname in Google brings up at the least two web site defacement archives displaying {that a} consumer named o5tdev was beforehand concerned in defacing websites with pro-Palestinian messages. The screenshot beneath, for instance, exhibits that 05tdev was a part of a gaggle known as Cyb3r Drag0nz Workforce.

Rey/o5tdev’s defacement pages. Picture: archive.org.
A 2023 report from SentinelOne described Cyb3r Drag0nz Workforce as a hacktivist group with a historical past of launching DDoS assaults and cyber defacements in addition to participating in knowledge leak exercise.
“Cyb3r Drag0nz Workforce claims to have leaked knowledge on over 1,000,000 of Israeli residents unfold throughout a number of leaks,” SentinelOne reported. “Up to now, the group has launched a number of .RAR archives of purported private data on residents throughout Israel.”
The cyber intelligence agency Flashpoint finds the Telegram consumer @05tdev was lively in 2023 and early 2024, posting in Arabic on anti-Israel channels like “Ghost of Palestine” [full disclosure: Flashpoint is currently an advertiser on this blog].
‘I’M A GINTY’
Flashpoint exhibits that Rey’s Telegram account (ID7047194296) was notably lively in a cybercrime-focused channel known as Jacuzzi, the place this consumer shared a number of private particulars, together with that their father was an airline pilot. Rey claimed in 2024 to be 15 years outdated, and to have household connections to Eire.
Particularly, Rey talked about in a number of Telegram chats that he had Irish heritage, even posting a graphic that exhibits the prevalence of the surname “Ginty.”
Rey, on Telegram claiming to have affiliation to the surname “Ginty.” Picture: Flashpoint.
Spycloud listed a whole bunch of credentials stolen from cybero5dev@proton.me, and people particulars point out that Rey’s laptop is a shared Microsoft Home windows gadget positioned in Amman, Jordan. The credential knowledge stolen from Rey in early 2024 present there are a number of customers of the contaminated PC, however that each one shared the identical final title of Khader and an deal with in Amman, Jordan.
The “autofill” knowledge lifted from Rey’s household PC accommodates an entry for a 46-year-old Zaid Khader that claims his mom’s maiden title was Ginty. The infostealer knowledge additionally exhibits Zaid Khader steadily accessed inner web sites for workers of Royal Jordanian Airways.
MEET SAIF
The infostealer knowledge makes clear that Rey’s full title is Saif Al-Din Khader. Having no luck contacting Saif instantly, KrebsOnSecurity despatched an electronic mail to his father Zaid. The message invited the daddy to reply by way of electronic mail, telephone or Sign, explaining that his son gave the impression to be deeply enmeshed in a critical cybercrime conspiracy.
Lower than two hours later, I obtained a Sign message from Saif, who mentioned his dad suspected the e-mail was a rip-off and had forwarded it to him.
“I noticed your electronic mail, sadly I don’t suppose my dad would reply to this as a result of they suppose its some ‘rip-off electronic mail,’” mentioned Saif, who instructed me he turns 16 years outdated subsequent month. “So I made a decision to speak to you instantly.”
Saif defined that he’d already heard from European legislation enforcement officers, and had been making an attempt to extricate himself from SLSH. When requested why then he was concerned in releasing SLSH’s new ShinySp1d3r ransomware-as-a-service providing, Saif mentioned he couldn’t simply instantly stop the group.
“Properly I cant simply dip like that, I’m making an attempt to wash up all the things I’m related to and transfer on,” he mentioned.

The previous Hellcat ransomware web site. Picture: Kelacyber.com
He additionally shared that ShinySp1d3r is only a rehash of Hellcat ransomware, besides modified with AI instruments. “I gave the supply code of Hellcat ransomware out mainly.”
Saif claims he reached out on his personal just lately to the Telegram account for Operation Endgame, the codename for an ongoing legislation enforcement operation focusing on cybercrime companies, distributors and their clients.
“I’m already cooperating with legislation enforcement,” Saif mentioned. “The truth is, I’ve been speaking to them since at the least June. I’ve instructed them practically all the things. I haven’t actually executed something like breaching right into a corp or extortion associated since September.”
Saif recommended {that a} story about him proper now may endanger any additional cooperation he could possibly present. He additionally mentioned he wasn’t positive if the U.S. or European authorities had been in touch with the Jordanian authorities about his involvement with the hacking group.
“A narrative would carry a lot undesirable warmth and would make issues very troublesome if I’m going to cooperate,” Saif mentioned. “I’m uncertain whats going to occur they mentioned they’re in touch with a number of international locations relating to my request however its been like a whole week and I bought no updates from them.”
Saif shared a screenshot that indicated he’d contacted Europol authorities late final month. However he couldn’t title any legislation enforcement officers he mentioned have been responding to his inquiries, and KrebsOnSecurity was unable to confirm his claims.
“I don’t actually care I simply wish to transfer on from all these items even when its going to be jail time or no matter they gonna say,” Saif mentioned.


