
The Python Software program Basis workforce has invalidated all PyPI tokens stolen within the GhostAction provide chain assault in early September, confirming that the menace actors did not abuse them to publish malware.
These tokens are used to publish packages on the Python Package deal Index (PyPI), a software program repository that acts because the default supply for Python’s package deal administration instruments and hosts a whole bunch of 1000’s of packages.
As PyPI admin Mike Fiedler defined, a GitGuardian worker reported on September fifth that malicious GitHub Actions workflows (like FastUUID) tried to exfiltrate PyPI tokens to a distant server. One other GitGuardian researcher emailed PyPI Safety with extra findings the identical day, however their message ended up within the spam folder, delaying the incident response till September tenth.
As quickly because it uncovered the complete scope of the provision chain assault, GitGuardian opened GitHub points in over 570 impacted repositories and notified the safety groups of GitHub, npm, and PyPI.
Many mission maintainers rotated their PyPI tokens, reverted modifications to actions workflows, or eliminated affected workflows after being notified by GitGuardian of the incident. Whereas the PyPI workforce discovered no proof of compromised PyPI repositories through the investigation, it invalidated all affected publishing tokens and contacted mission homeowners to help in securing their accounts.
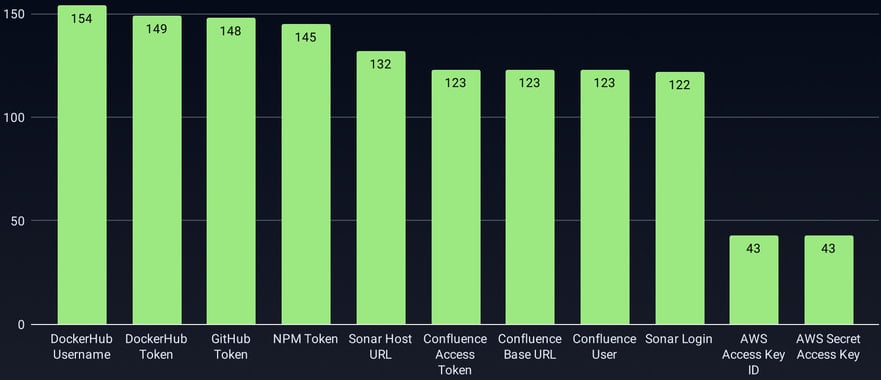
Nonetheless, GitGuardian estimated on the time that over 3,3000 secrets and techniques had been stolen within the GhostAction marketing campaign, together with PyPI, npm, DockerHub, GitHub, and Cloudflare API tokens, in addition to AWS entry keys and database credentials.
“This evaluation revealed compromised tokens throughout a number of package deal ecosystems, together with Rust crates and npm packages,” GitGuardian mentioned. “A number of firms had been discovered to have their whole SDK portfolio compromised, with malicious workflows affecting their Python, Rust, JavaScript, and Go repositories concurrently.”
On Tuesday, Fiedler suggested PyPI package deal maintainers who use GitHub Actions to switch long-lived tokens with short-lived Trusted Publishers tokens, which might defend towards such a assault. Fiedler additionally urged them to log into their accounts and assessment their safety historical past for any suspicious exercise.
“After confirming that no PyPI accounts had been compromised, on September fifteenth I reached out to the maintainers of the affected tasks to inform them of the state of affairs, to allow them to know that their tokens had been invalidated, and suggest utilizing Trusted Publishers with GitHub Actions to assist shield their tasks sooner or later,” Fiedler mentioned.
“Attackers focused all kinds of repositories, a lot of which had PyPI tokens saved as GitHub secrets and techniques, modifying their workflows to ship these tokens to exterior servers. Whereas the attackers efficiently exfiltrated some tokens, they don’t seem to have used them on PyPI.”
In August, attackers exploited a flawed GitHub Actions workflow utilized by the Nx repository (a extremely popular construct system and monorepo administration device) as a part of one other provide chain assault (dubbed s1ngularity), which affected 2,180 accounts and seven,200 repositories.
One month earlier, the Python Software program Basis additionally warned customers {that a} phishing marketing campaign was trying to steal their credentials utilizing a pretend Python Package deal Index (PyPI) web site.


