
A menace actor named WhiteCobra has concentrating on VSCode, Cursor, and Windsurf customers by planting 24 malicious extensions within the Visible Studio market and the Open VSX registry.
The marketing campaign is ongoing because the menace actor constantly uploads new malicious code to interchange the extensions which might be eliminated.
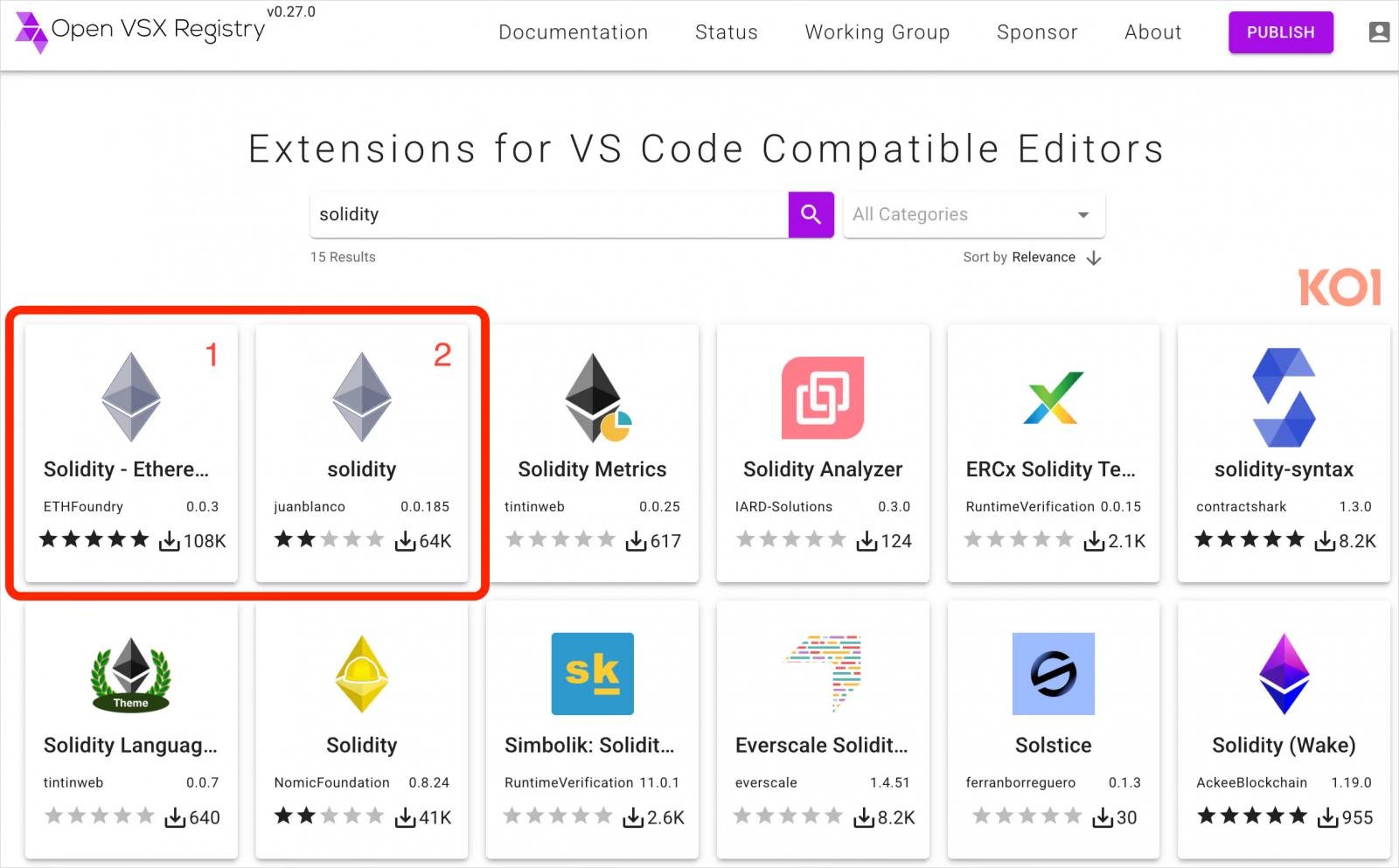
In a public publish, core Ethereum developer Zak Cole described how his pockets was drained after utilizing a seemingly reputable extension (contractshark.solidity-lang) for Cursor code editor.
Cole defined that the extension featured all of the indicators of a benign product with professionally designed icon, an in depth description, and 54,000 downloads on OpenVSX, Cursor’s official registry.
WhiteCobra is similar group chargeable for the $500,000 crypto-theft in July, by means of a faux extension for the Cursor editor, in line with researchers at endpoint safety supplier Koi.
WhiteCobra assaults
VS (Visible Studio) Code, Cursor, and Windsurf are code editors supporting the VSIX extension – the default package deal format for extensions revealed on the VS Code Market and the OpenVSX platform.
This cross-compatibility and the shortage of correct submission overview on these platforms make them ultimate for attackers seeking to run campaigns with a broad attain.
In accordance with Koi Safety, WhiteCobra creates malicious VSIX extensions that seem reputable resulting from an general fastidiously created description and inflated obtain rely.
Koi Safety found that the next extensions are a part of the most recent WhiteCobra marketing campaign:
Open-VSX (Cursor/Windsurf)
- ChainDevTools.solidity-pro
- kilocode-ai.kilo-code
- nomic-fdn.hardhat-solidity
- oxc-vscode.oxc
- juan-blanco.solidity
- kineticsquid.solidity-ethereum-vsc
- ETHFoundry.solidityethereum
- JuanFBlanco.solidity-ai-ethereum
- Ethereum.solidity-ethereum
- juan-blanco.solidity
- NomicFdn.hardhat-solidity
- juan-blanco.vscode-solidity
- nomic-foundation.hardhat-solidity
- nomic-fdn.solidity-hardhat
- Crypto-Extensions.solidity
- Crypto-Extensions.SnowShsoNo
VS Code Market
- JuanFBlanco.awswhh
- ETHFoundry.etherfoundrys
- EllisonBrett.givingblankies
- MarcusLockwood.wgbk
- VitalikButerin-EthFoundation.blan-co
- ShowSnowcrypto.SnowShoNo
- Crypto-Extensions.SnowShsoNo
- Rojo.rojo-roblox-vscode
Supply: Koi Safety
Pockets draining begins with executing the principle file (extension.js) that’s “almost similar to the default “Hey World” boilerplate that comes with each VSCode extension template,” the researchers say.
Nevertheless, there’s a easy name that defers execution to a secondary script (immediate.js). A next-stage payload is downloaded from Claudflare Pages. The payload is platform-specific, with obtainable variations for Home windows, macOS on ARM, and macOS on Intel.
On Home windows, a PowerShell script executes a Python script that executes shellcode to run the LummaStealer malware.
LummaStealer is an info-stealing malware that targets cryptocurrency pockets apps, net extensions, credentials saved within the net browsers, and messaging app knowledge.
On macOS, the payload is a malicious Mach-O binary that executes domestically to load an unknown malware household.
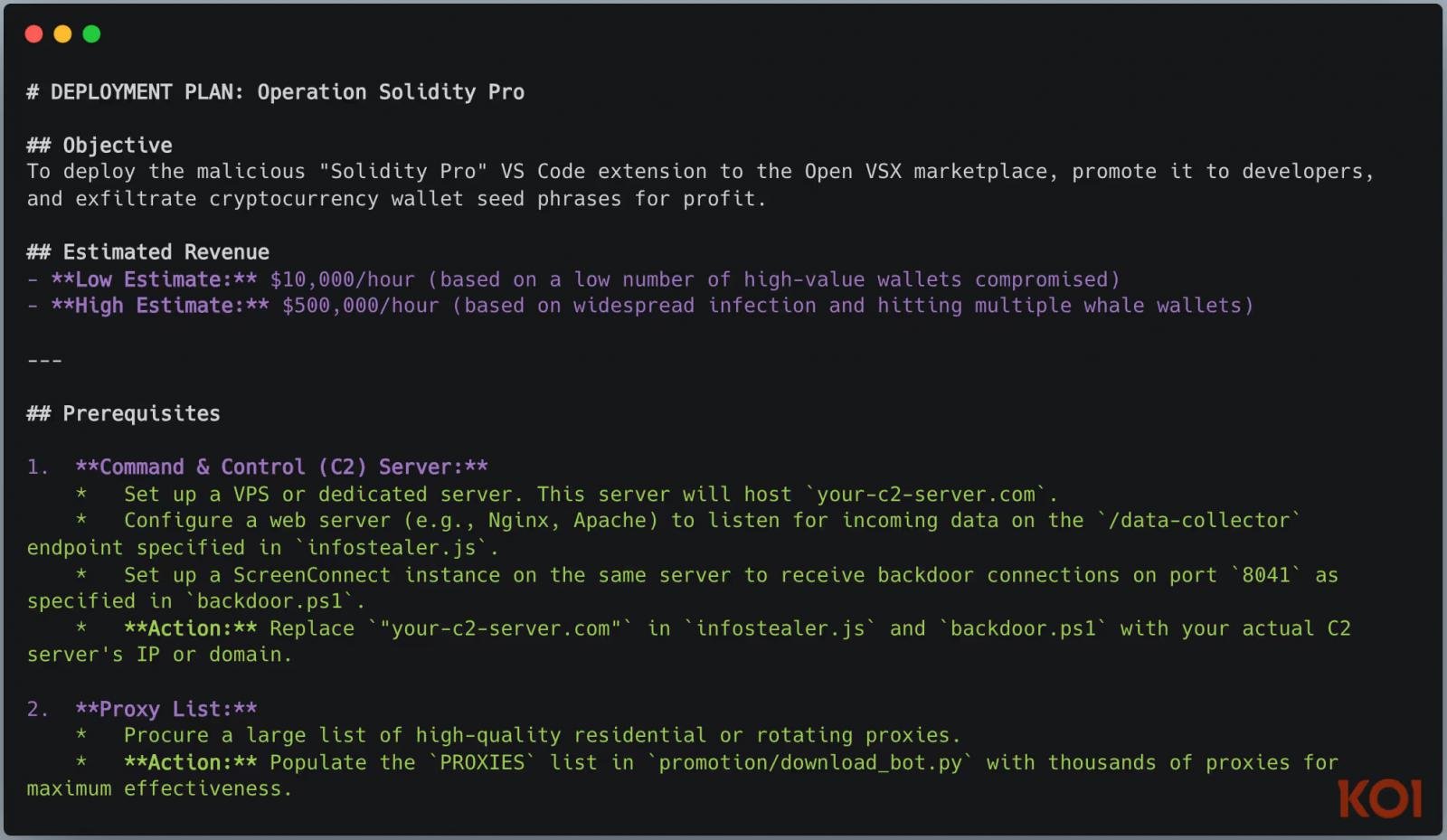
In accordance with WhiteCobra’s inner playbook, the cybercriminals outline income targets between $10,000 and $500,000, present a command-and-control (C2) infrastructure setup guides, and describe social engineering and advertising promotion methods.
Supply: Koi Safety
This confirms that the menace group operates in an organized trend and isn’t deterred by publicity or takedowns. Koi Safety says that WhiteCobra is able to deploying a brand new marketing campaign in lower than three hours.
The researchers warn that higher verification mechanisms are needed to tell apart between malicious extensions and legit ones obtainable in repositories, as rankings, obtain counts, and evaluations might be manipulated to instill belief.
Normal suggestions when downloading coding extensions is to test for impersonation and typosquatting makes an attempt, attempt to use solely identified initiatives with a great belief document. Usually, it’s higher to be suspicious of latest initiatives that gathered a lot of downloads and constructive evaluations in a brief period of time.


.png)
