
A newly found phishing-as-a-service (PhaaS) platform, named VoidProxy, targets Microsoft 365 and Google accounts, together with these protected by third-party single sign-on (SSO) suppliers equivalent to Okta.
The platform makes use of adversary-in-the-middle (AitM) ways to steal credentials, multi-factor authentication (MFA) codes, and session cookies in actual time.
VoidProxy was found by Okta Menace Intelligence researchers, who describe it as scalable, evasive, and complicated.
The assault begins with emails from a compromised accounts at electronic mail service suppliers, like Fixed Contact, Energetic Marketing campaign, and NotifyVisitors, whicch embrace shortened hyperlinks that ship recipients to phishing websites after a a number of redirections.
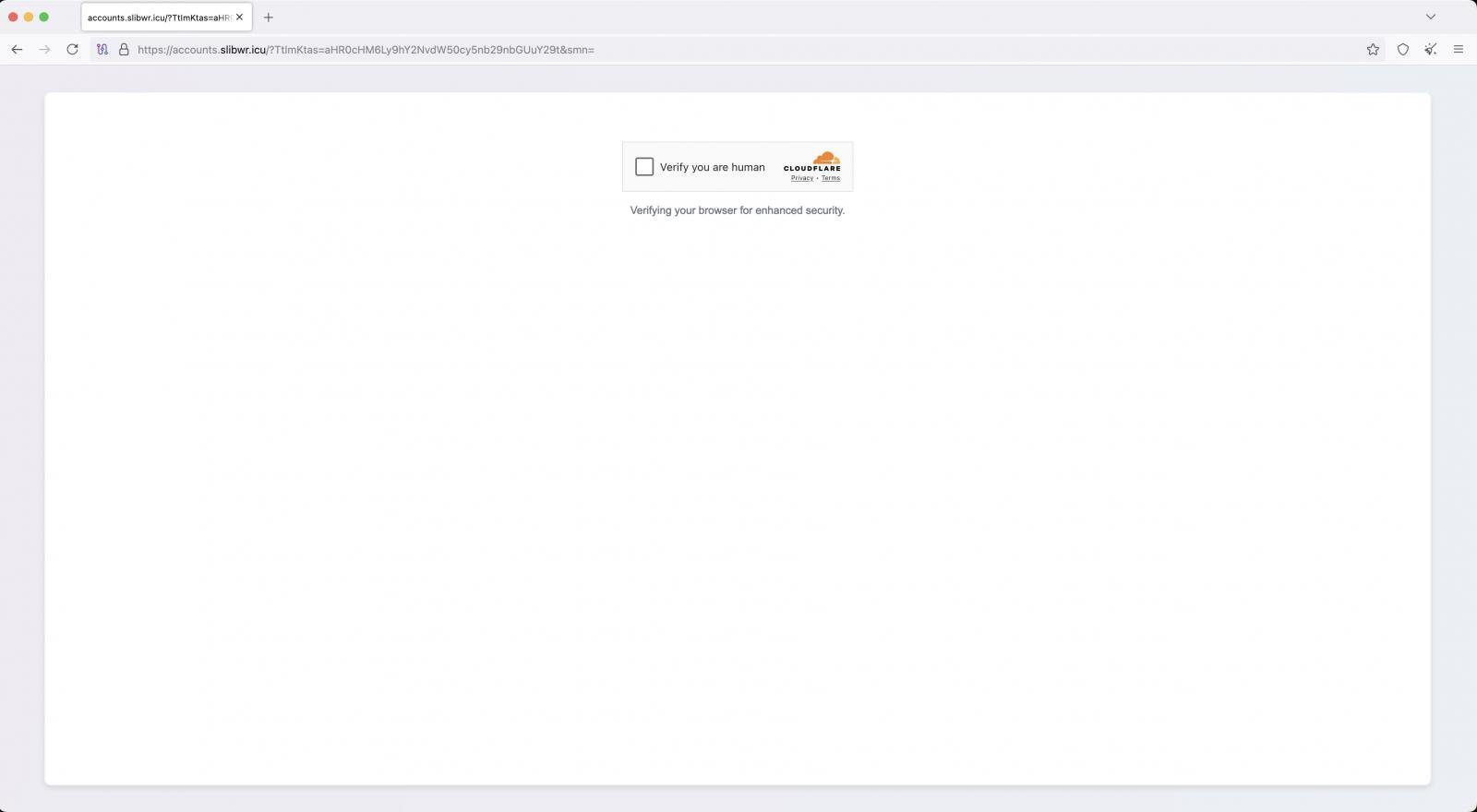
The malicious websites are hosted on disposable low-cost domains on .icu, .sbs, .cfd, .xyz, .prime, and .dwelling, that are protected by Cloudflare to cover their actual IPs.
Guests are first served a Cloudflare CAPTCHA problem to filter out bots and enhance the sense of legitimacy, whereas a Cloudflare Employee surroundings is used to filter site visitors and cargo pages.
Supply: Okta
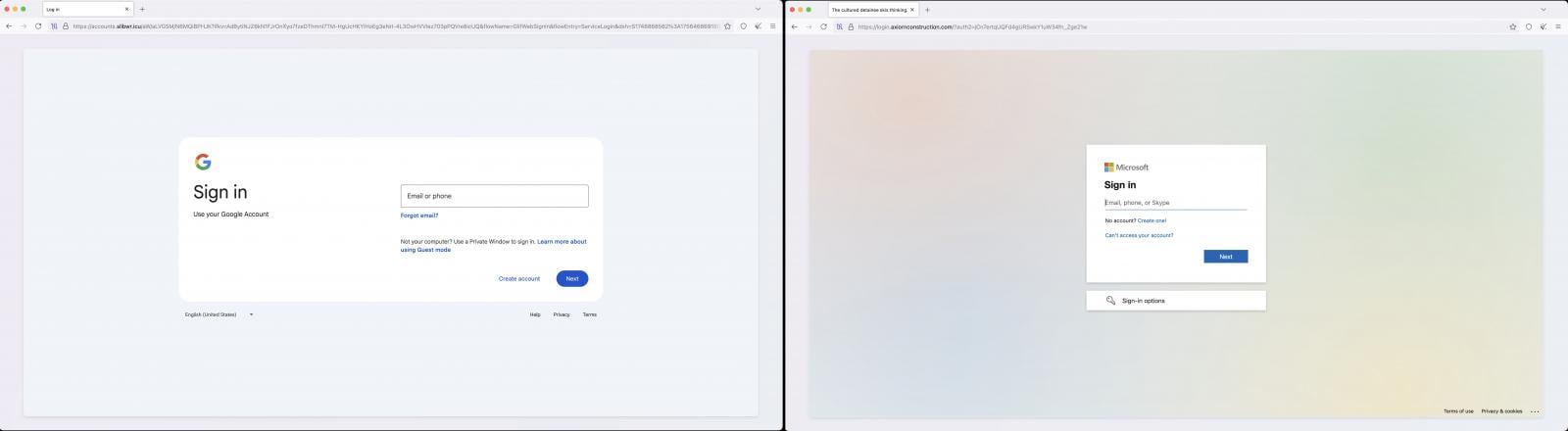
Chosen targets revceive a web page that mimics a Microsoft or Google login, whereas the remaining are funneled to a generic and “Welcome” web page that presents no menace.
If credentials are typed into the phishing kind, requests are proxied via VoidProxy’s adversary-in-the-middle (AitM) to Google or Microsoft servers.
Supply: Okta
Federated accounts like these utilizing Okta for SSO are redirected to a second-stage phishing web page impersonating Microsoft 365 or Google SSO flows with Okta. These requests have been proxied to Okta servers.
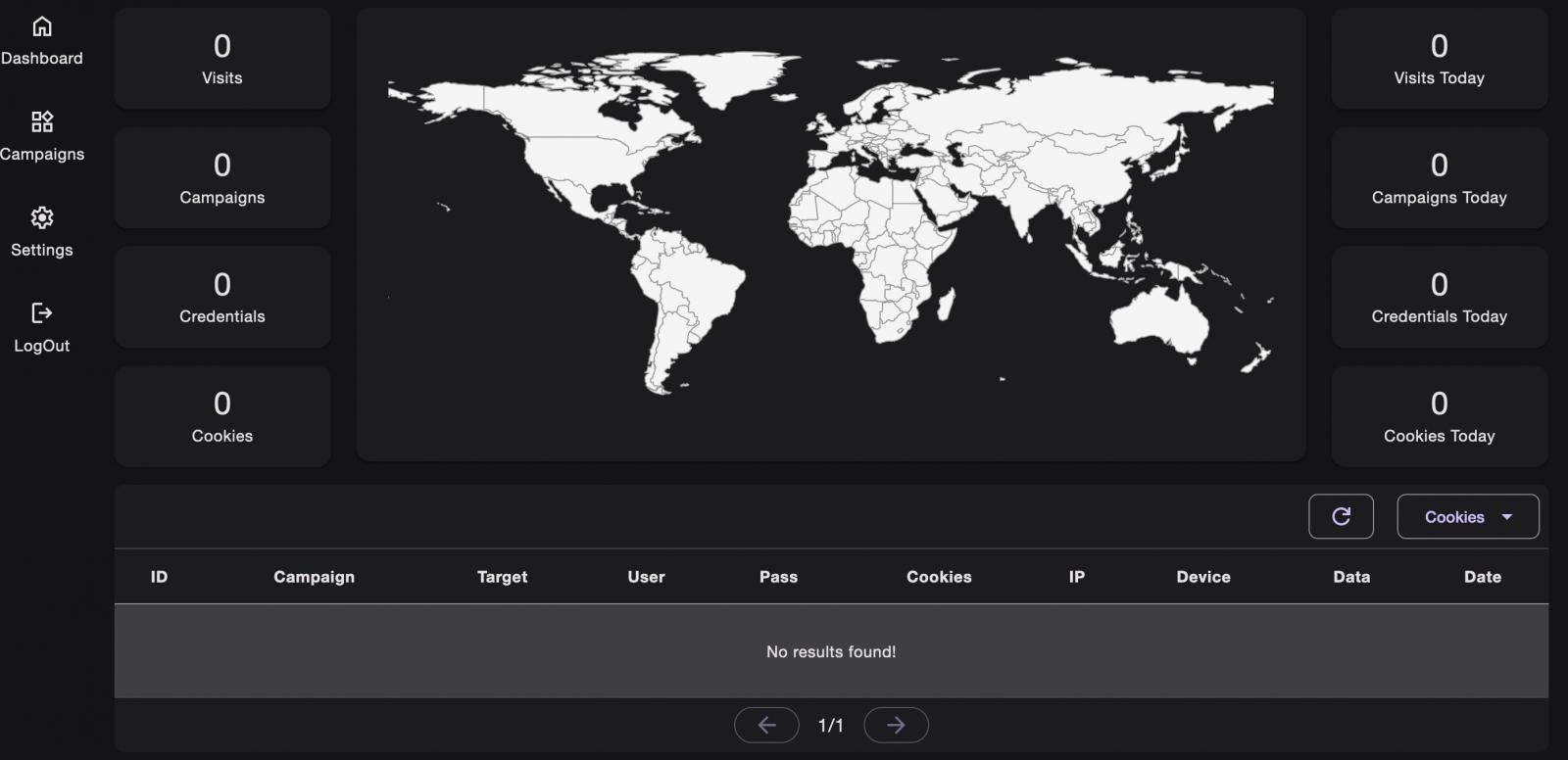
The service’s proxy server relays site visitors between the sufferer and the reputable service whereas capturing usernames, passwords, and MFA codes in transit.
When the reputable service points a session cookie, VoidProxy intercepts it and creates a replica that’s made accessible to the attackers proper on the platform’s admin panel.
Supply: Okta
Okta famous that customers who had enrolled in phishing-resistant authentications like Okta FastPass have been protected against VoidProxy’s assault stream and acquired warnings about their account being below assault.
The researchers suggestions embrace limiting entry of delicate apps solely to managed gadgets, implementing risk-based entry controls, utilizing IP session binding for administrative apps, and forcing re-authentication for admins making an attempt delicate actions.


