
Massive community scans have been concentrating on Cisco ASA units, prompting warnings from cybersecurity researchers that it may point out an upcoming flaw within the merchandise.
GreyNoise has recorded two important scanning spikes in late August, with as much as 25,000 distinctive IP addresses probing ASA login portals and in addition Cisco IOS Telnet/SSH.
The second wave, logged on August 26, 2025, was largely (80%) pushed by a Brazilian botnet, utilizing roughly 17,000 IPs.
In each instances, the risk actors used overlapping Chrome-like consumer brokers, suggesting a standard origin.
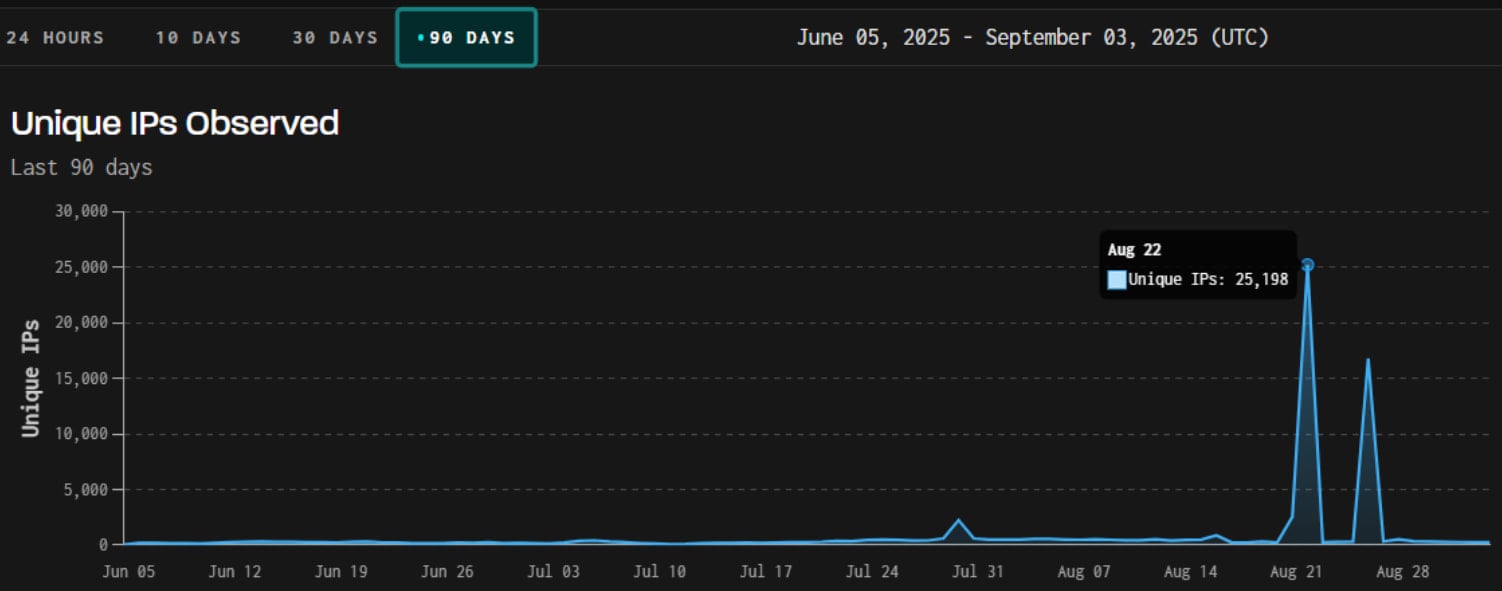
The scanning exercise predominantly focused america, whereas the UK and Germany have been additionally focused.
GreyNoise has beforehand defined that such reconnaissance exercise precedes the disclosure of latest vulnerabilities on the scanned merchandise in 80% of instances.
Statistically, this correlation was weaker for Cisco, in comparison with different distributors, however details about such spikes can nonetheless be to useful to defenders in enhancing their monitoring and proactive measures.
These scans are generally failed exploitation makes an attempt of already-patched bugs, however they will also be enumeration and mapping efforts in preparation for exploiting new flaws.
A separate report printed earlier by system administrator ‘NadSec – Rat5ak’ stories overlapping exercise that began on July 31 with low opportunistic scans that escalated in mid-August and culminated on August 28.
Rat5ak noticed 200,000 hits on Cisco ASA endpoints inside 20 hours, with a uniform 10k/IP visitors that appeared extremely automated.
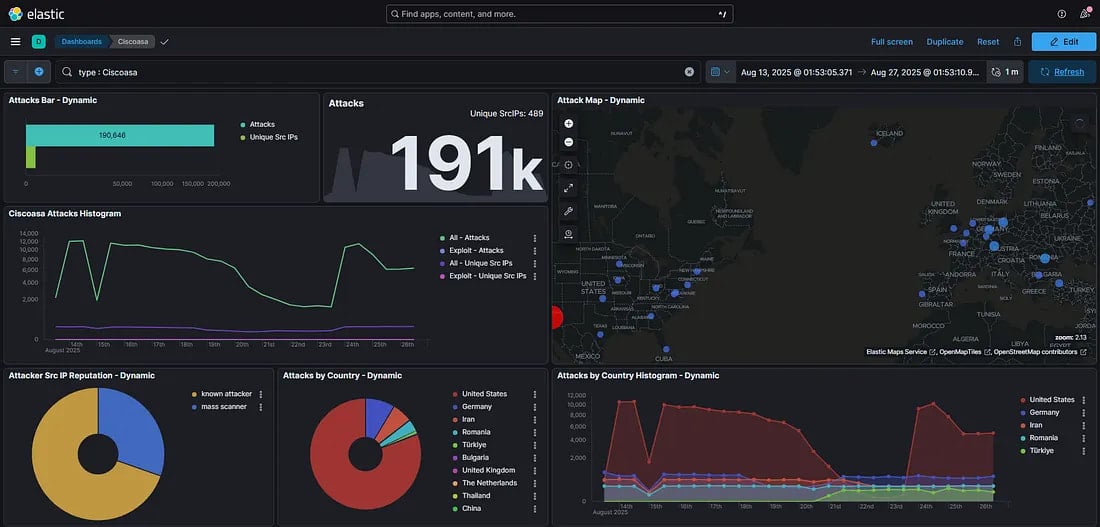
The administrator stories that the exercise got here from three ASNs, particularly Nybula, Cheapy-Host, and World Connectivity Options LLP.
System directors are suggested to use the most recent safety updates on Cisco ASA to patch identified vulnerabilities, implement multi-factor authentication (MFA) for all distant ASA logins, and keep away from exposing /+CSCOE+/logon.html, WebVPN, Telnet, or SSH straight.
If exterior entry is required, a VPN concentrator, reverse proxy, or entry gateway must be used to implement further entry controls.
Lastly, use the scanning exercise indicators shared in GreyNoise and Rat5ak’s stories to preemptively block these makes an attempt, or use geo-blocking and charge limiting for areas far out of your group.
BleepingComputer has contacted Cisco for a touch upon the noticed exercise, and we are going to replace this publish after we hear again from them.


