
The U.S. Treasury’s Workplace of Overseas Belongings Management (OFAC) has sanctioned two people and two firms related to North Korean IT employee schemes that function on the expense of American organizations.
These schemes contain inserting in U.S. companies expert tech employees with stolen or fabricated identities and utilizing so-called “laptop computer farms” to cover the true location of the staff.
The employees funnel their earnings to the DPRK regime to fund the regime’s weapons program. Additionally they usually steal delicate information or plant malware to create disruption when their cowl is blown.
Within the context of cracking down on these operations, U.S. authorities have now sanctioned the next people and corporations:
- Vitaliy Sergeyevich Andreyev – A Russian nationwide who has labored with DPRK officers since not less than December 2024 to facilitate monetary transfers supporting the Chinyong Info Expertise Cooperation Firm. He transformed cryptocurrency into almost $600,000, offering materials help to the DPRK’s abroad IT employee delegations working in Russia and Laos.
- Kim Ung Solar – A DPRK financial and commerce consular official primarily based in Russia who collaborated with Andreyev to channel funds for the sanctioned IT employee community. He’s designated to behave on behalf of the Authorities of North Korea in reference to these revenue-generating actions.
- Shenyang Geumpungri Community Expertise Co., Ltd – A Chinese language entrance firm tied to Chinyong and composed of a delegation of DPRK IT employees. Since 2021, it has earned over $1 million in income for each Chinyong and Korea Sinjin Buying and selling Company, serving to funnel illicit revenues to the DPRK’s weapons packages.
- Korea Sinjin Buying and selling Company – A DPRK firm subordinate to the Ministry of Individuals’s Armed Forces Basic Political Bureau, already underneath U.S. sanctions. It receives directives from DPRK officers concerning the deployment of abroad IT employees and advantages from their earnings.
Blockchain intelligence agency Chainalysis additionally printed particulars on Andreyev’s Bitcoin pockets, which was used as a deposit deal with on a mainstream alternate to launder proceeds from DPRK IT employees.
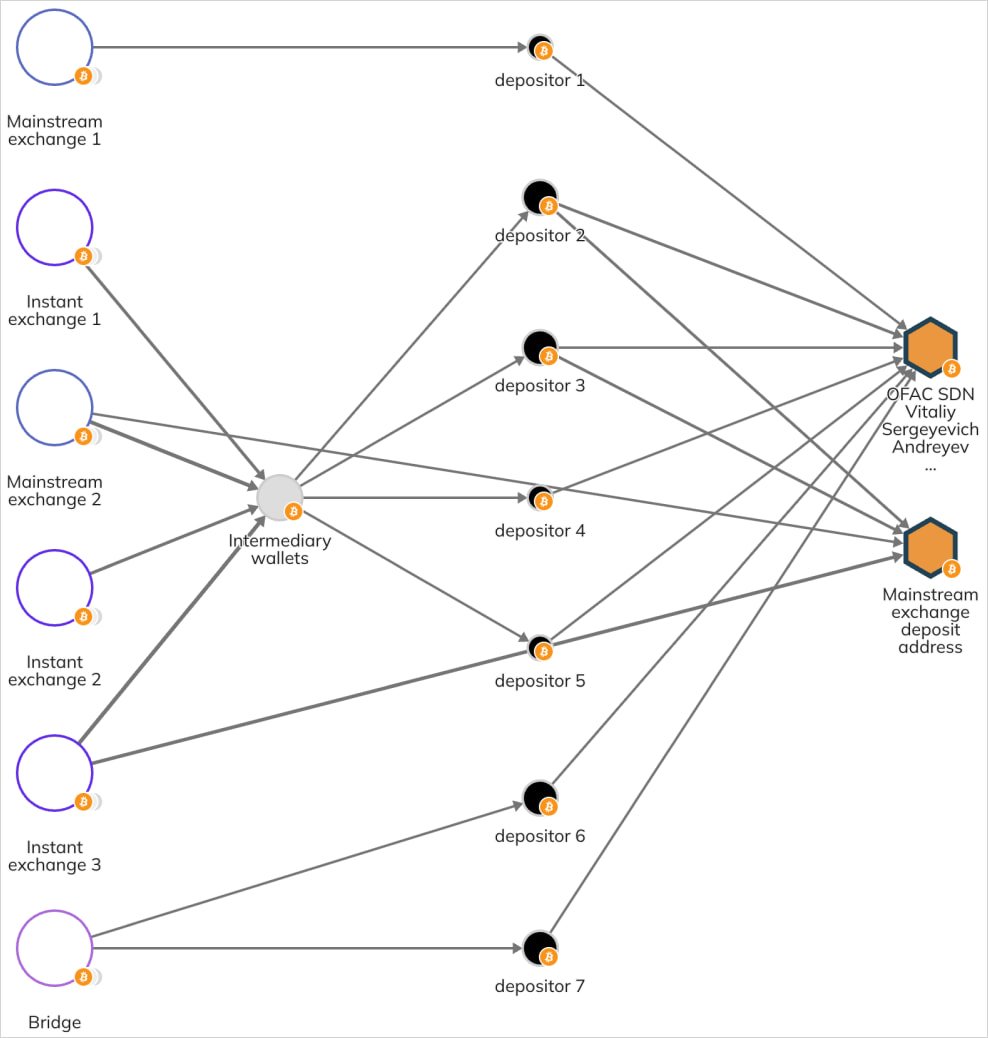
Supply: Chainalysis
The impact of those sanctions is a freeze on U.S.-based belongings for the designated entities, and all Americans and companies are prohibited from partaking in any transactions with them.
This extends as a deterrence outdoors the U.S., as entities threat being sanctioned or restricted themselves in the event that they select to conduct transactions on behalf of designated individuals and corporations.
OFAC is more and more focusing on infrastructure and monetary facilitators who assist DPRK convert cryptocurrency into usable funds.
Final July, the U.S. authorities sanctioned, charged, or indicted a complete of 20 people and eight firms in three separate waves of enforcement (1, 2, 3).



