
The Crypto24 ransomware group has been utilizing customized utilities to evade safety options on breached networks, exfiltrate knowledge, and encrypt information.
The menace group’s earliest exercise was reported on BleepingComputer boards in September 2024, although it by no means reached notable ranges of notoriety.
In accordance with Pattern Micro researchers monitoring Crypto24’s operations, the hackers have hit a number of massive organizations in the USA, Europe, and Asia, specializing in high-value targets within the finance, manufacturing, leisure, and tech sectors.
The safety researchers report that Crypto24 seems to be educated and well-versed, suggesting a excessive probability that it was shaped by former core members of now-defunct ransomware operations.
Put up-compromise exercise
After gaining preliminary entry, Crypto24 hackers activate default administrative accounts on Home windows programs inside enterprise environments or create new native consumer accounts for stealthy, persistent entry.
Following a reconnaissance part utilizing a customized batch file and instructions that enumerate accounts, profile system {hardware}, and the disk structure, the attacker creates malicious Home windows companies and scheduled duties for persistence.
The primary is WinMainSvc, a keylogger service, and the second is MSRuntime, a ransomware loader.
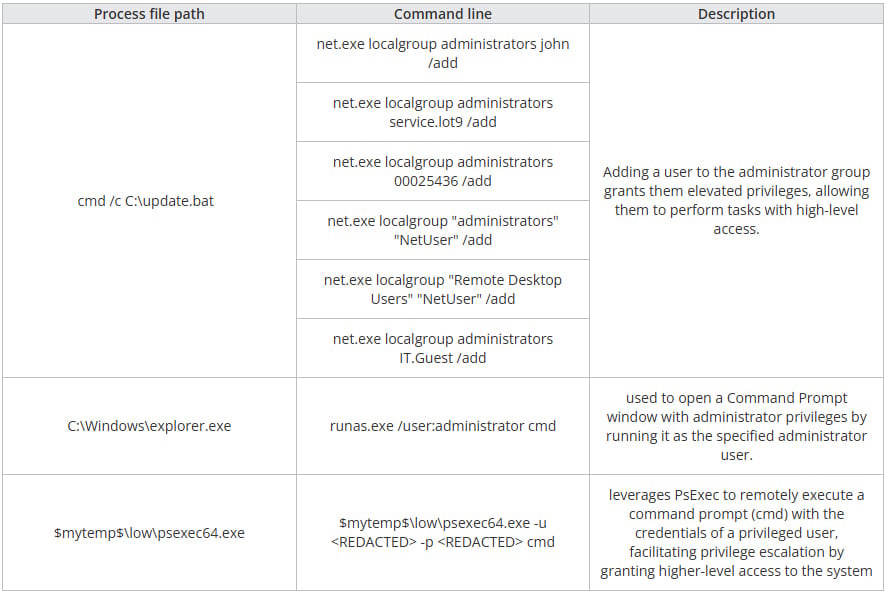
Supply: Pattern Micro
Subsequent, Crypto24 operators use a customized variant of the open-source instrument RealBlindingEDR, which targets safety brokers from a number of distributors by disabling their kernel drivers:
- Pattern Micro
- Kaspersky
- Sophos
- SentinelOne
- Malwarebytes
- Cynet
- McAfee
- Bitdefender
- Broadcom (Symantec)
- Cisco
- Fortinet
- Acronis
Crypto24’s customized RealBlindingEDR extracts the corporate identify from the driving force’s metadata, compares it to a hardcoded listing, and if there’s a match, it disables kernel-level hooks/callbacks to “blind” detection engines.
Regarding Pattern Micro merchandise particularly, the report mentions that, if the attacker has administrator privileges, they run a batch script that invokes the reliable ‘XBCUninstaller.exe’ to uninstall Pattern Imaginative and prescient One.
“We noticed circumstances the place attackers executed the Pattern Imaginative and prescient One uninstaller, XBCUninstaller.exe, through gpscript.exe,” Pattern Micro researchers say.
“The file in query is a reliable instrument supplied by Pattern Micro for troubleshooting, particularly to resolve points akin to fixing inconsistent brokers inside Pattern Imaginative and prescient One deployments.”
“Its meant use is to cleanly uninstall Endpoint BaseCamp when required for upkeep or help.”
This instrument basically prevents the detection of follow-on payloads just like the keylogger (WinMainSvc.dll) and the ransomware (MSRuntime.dll), each customized instruments.
The keylogger, which masquerades as “Microsoft Assist Supervisor,” logs each energetic window titles and keypresses, together with management keys (Ctrl, Alt, Shift, operate keys).
The attackers additionally use SMB shares for lateral motion and staging information for extraction.
All stolen knowledge is exfiltrated to Google Drive utilizing a customized instrument that leverages the WinINET API to work together with Google’s service.
The ransomware payload executes after deleting quantity shadow copies on Home windows programs to stop simple restoration.
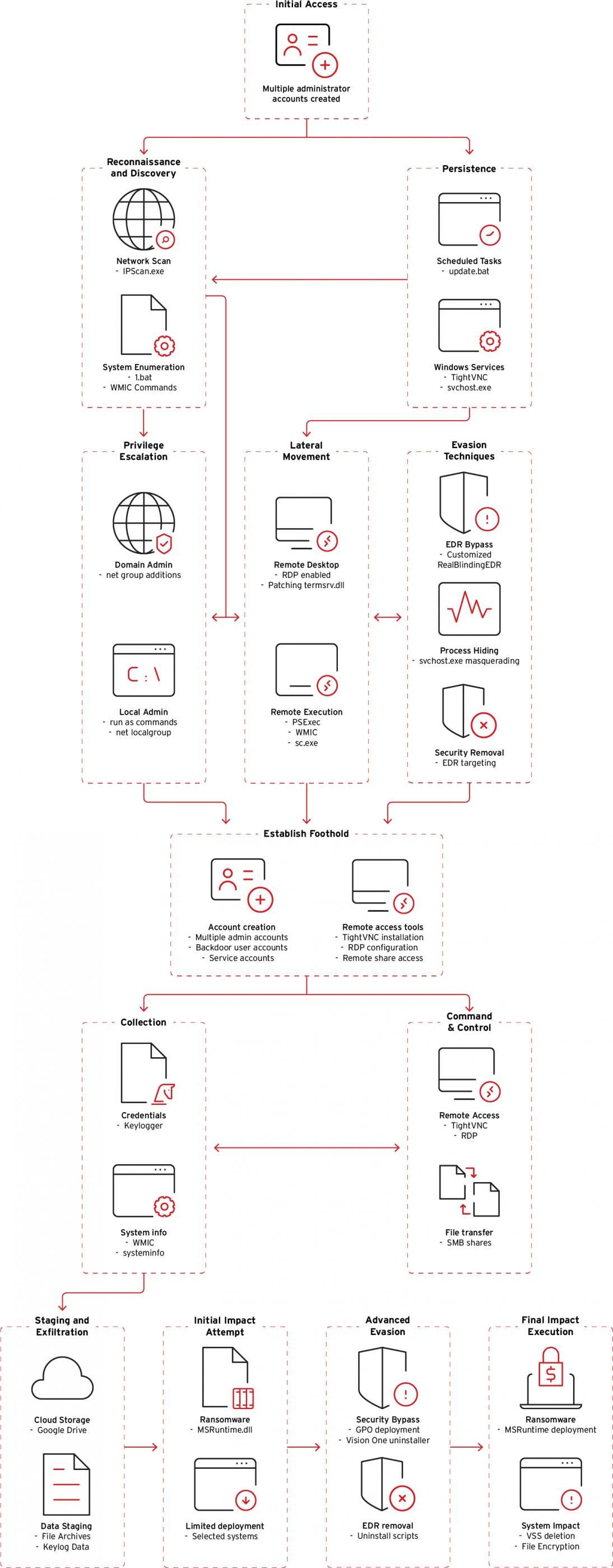
Supply: Pattern Micro
Pattern Micro doesn’t present any particulars concerning the ransomware a part of the assault, akin to encryption scheme, the ransom notes, communication strategies, focused file paths, language, or branding clues.
The cybersecurity firm has shared on the finish of the report a listing of indicators of compromise that different defenders can use to detect and block Crypto24 ransomware assaults earlier than they attain the final word phases.



