
Over 29,000 Change servers uncovered on-line stay unpatched in opposition to a high-severity vulnerability that may let attackers transfer laterally in Microsoft cloud environments, probably main to finish area compromise.
The safety flaw (tracked as CVE-2025-53786) helps risk actors who acquire administrative entry to on-premises Change servers to escalate privileges throughout the group’s related cloud setting by forging or manipulating trusted tokens or API calls, with out leaving simply detectable traces and making it laborious to detect exploitation.
CVE-2025-53786 impacts Change Server 2016, Change Server 2019, and Microsoft Change Server Subscription Version, which replaces the perpetual license mannequin with a subscription-based one, in hybrid configurations.
The flaw was disclosed after Microsoft launched steerage and an Change server hotfix in April 2025 as a part of its Safe Future Initiative, which helps a brand new structure utilizing a devoted hybrid app that replaces the insecure shared identification beforehand utilized by on-premises Change Server and Change On-line.
Whereas Redmond has not but discovered proof of abuse in assaults, the vulnerability was nonetheless tagged as “Exploitation Extra Possible” as a result of Redmond considers that exploit code permitting constant exploitation may very well be developed, growing its attractiveness to attackers.
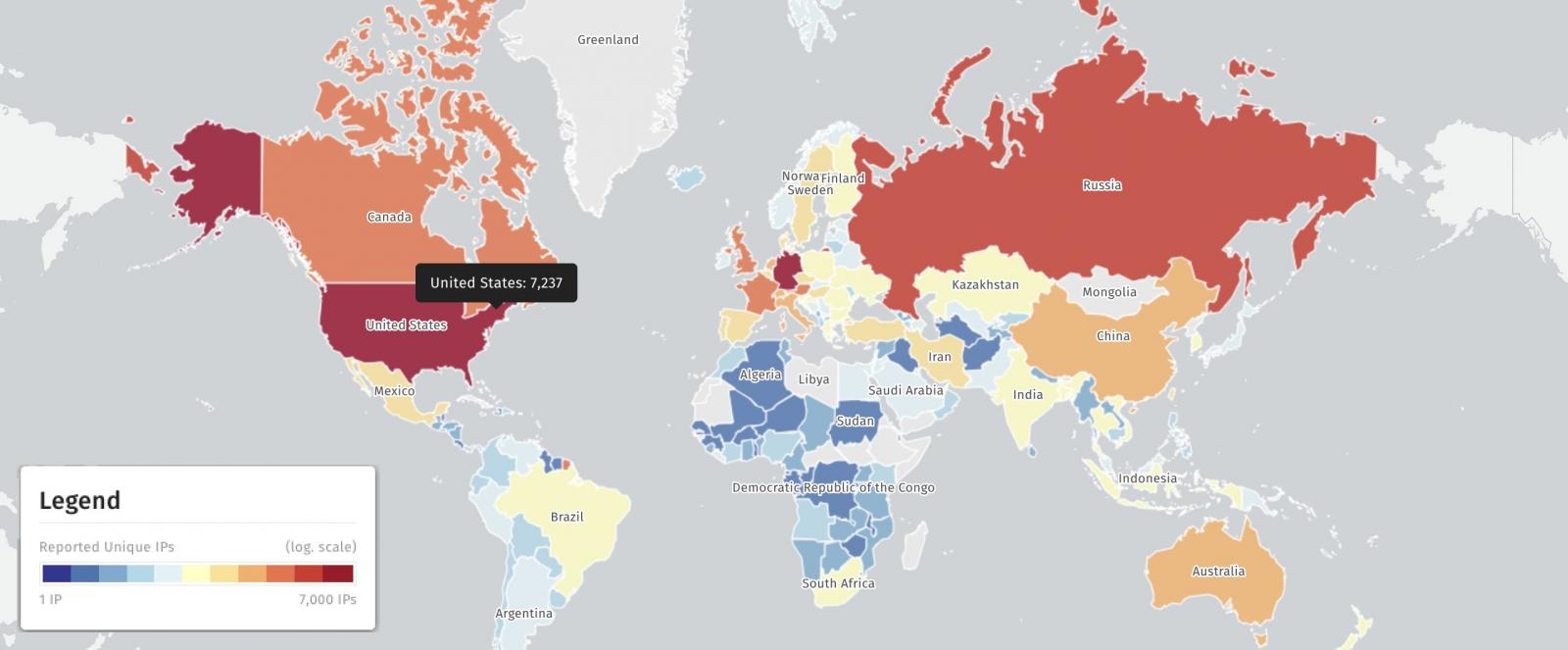
In keeping with scans from the safety risk monitoring platform Shadowserver, greater than 29,000 Change servers are nonetheless unpatched in opposition to potential CVE-2025-53786 assaults.
Out of a complete of 29,098 unpatched servers detected on August 10, over 7,200 IP addresses have been present in the USA, greater than 6,700 in Germany, and over 2,500 in Russia.
Federal companies ordered to mitigate over the weekend
Sooner or later after Microsoft disclosed the vulnerability, CISA issued Emergency Directive 25-02, ordering all Federal Civilian Govt Department (FCEB) companies, together with the Division of Homeland Safety, the Division of the Treasury, and the Division of Power, to mitigate this high-severity Microsoft Change vulnerability by Monday at 9:00 AM ET.
Federal companies should mitigate the flaw by first taking a list of their Change environments utilizing Microsoft’s Well being Checker script and disconnecting public-facing servers which might be now not supported by the April 2025 hotfix from the web, like end-of-life (EOL) or end-of-service variations of Change Server.
All remaining servers need to be up to date to the most recent cumulative updates (CU14 or CU15 for Change 2019, and CU23 for Change 2016) and patched with Microsoft’s April hotfix.
In a separate advisory issued on Thursday, the U.S. cybersecurity company warned that failing to mitigate CVE-2025-53786 may lead “to a hybrid cloud and on-premises complete area compromise.”
Whereas non-government organizations are usually not required to take motion beneath Emergency Directive 25-02, CISA urged all organizations to take the identical measures to safe their programs in opposition to potential assaults.
“The dangers related to this Microsoft Change vulnerability lengthen to each group and sector utilizing this setting,” mentioned CISA Appearing Director Madhu Gottumukkala.
“Whereas federal companies are mandated, we strongly urge all organizations to undertake the actions on this Emergency Directive.”



