
A brand new Endpoint Detection and Response (EDR) killer that’s thought of to be the evolution of ‘EDRKillShifter,’ developed by RansomHub, has been noticed in assaults by eight completely different ransomware gangs.
Such instruments assist ransomware operators flip off safety merchandise on breached programs to allow them to deploy payloads, escalate privileges, try lateral motion, and finally encrypt gadgets on the community with out being detected.
In line with Sophos safety researchers, the brand new instrument, which wasn’t given a particular identify, is utilized by RansomHub, Blacksuit, Medusa, Qilin, Dragonforce, Crytox, Lynx, and INC.
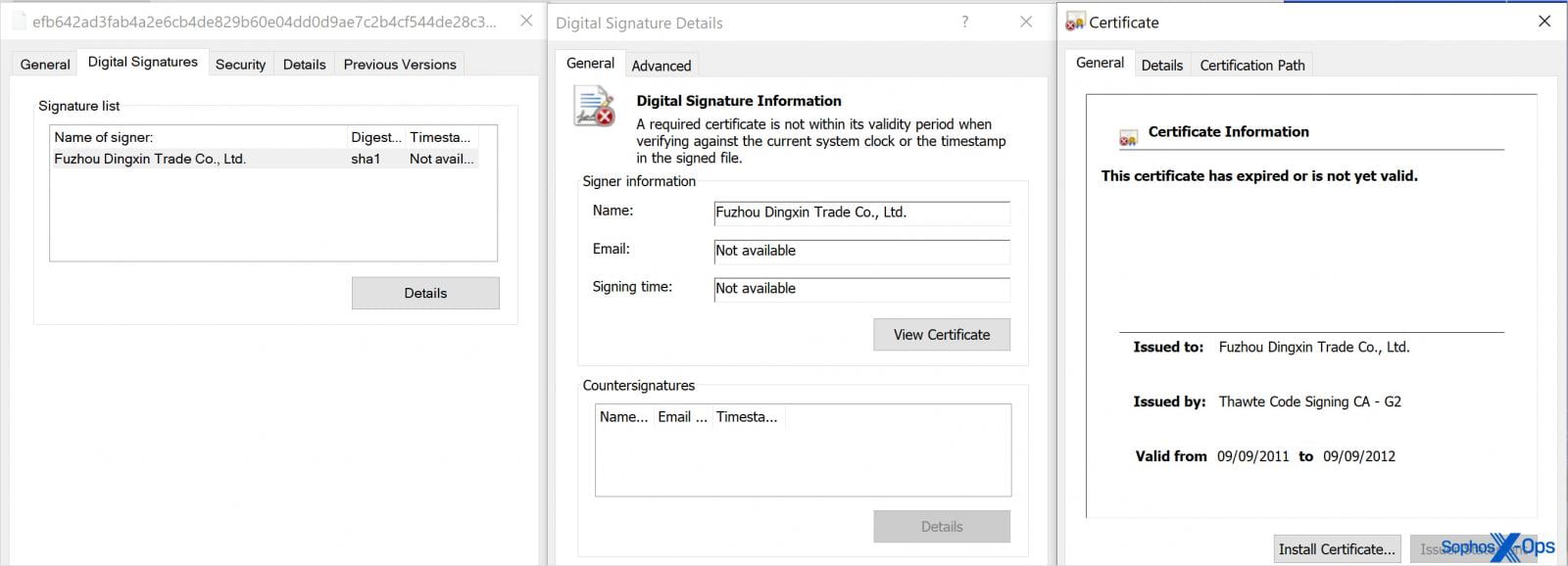
The brand new EDR killer instrument makes use of a closely obfuscated binary that’s self-decoded at runtime and injected into authentic purposes.
The instrument searches for a digitally signed (stolen or expired certificates) driver with a random five-character identify, which is hardcoded into the executable.
Supply: Sophos
If discovered, the malicious driver is loaded into the kernel, as required to carry out a ‘convey your individual weak driver’ (BYOVD) assault and obtain kernel privileges required to show off safety merchandise.
The motive force masquerades as a authentic file such because the CrowdStrike Falcon Sensor Driver, however as soon as lively, it kills AV/EDR-related processes and stops companies related to safety instruments.
The focused distributors embrace Sophos, Microsoft Defender, Kaspersky, Symantec, Development Micro, SentinelOne, Cylance, McAfee, F-Safe, HitmanPro, and Webroot.
Though variants of the brand new EDR killer instrument differ in driver names, focused AVs, and construct traits, all of them use HeartCrypt for packing, and proof suggests information and gear sharing amongst even competing risk teams.
Sophos particularly notes that it is unlikely the instrument was leaked after which reused by different risk actors, however is moderately developed by way of a shared and collaborative framework.
“To be clear, it is not {that a} single binary of the EDR killer leaked out and was shared between risk actors. As an alternative, every assault used a unique construct of the proprietary instrument,” defined Sophos.
This tactic of instrument sharing, particularly in what issues EDR killers, is frequent within the ransomware house.
Other than EDRKillShifter, Sophos additionally found one other instrument known as AuKill, which Medusa Locker and LockBit utilized in assaults.
SentinelOne additionally reported final 12 months about FIN7 hackers promoting their customized “AvNeutralizer” instrument to a number of ransomware gangs, together with BlackBasta, AvosLocker, MedusaLocker, BlackCat, Trigona, and LockBit.
The entire indicators of compromise related to this new EDR killer instrument are accessible on this GitHub repository.


