
The North Korean ‘Lazarus’ hacking group focused workers of an aerospace firm positioned in Spain with faux job alternatives to hack into the company community utilizing a beforehand unknown ‘LightlessCan’ backdoor.
The hackers utilized their ongoing “Operation Dreamjob” marketing campaign, which entails approaching a goal over LinkedIn and interesting in a faux worker recruitment course of that, sooner or later, required the sufferer to obtain a file.
The worker did so on an organization’s laptop, permitting the North Korean hackers to breach the company community to conduct cyber espionage.
ESET investigated the incident and will reconstruct the preliminary entry and retrieve elements of Lazarus’ toolset, together with a beforehand undocumented backdoor, which they named ‘LightlessCan.’
Lazarus assault chain
The Operation Dreamjob assault reconstructed by ESET began with a LinkedIn message by the Lazarus actor pretending to be a recruiter from Meta (Fb) named Steve Dawson.
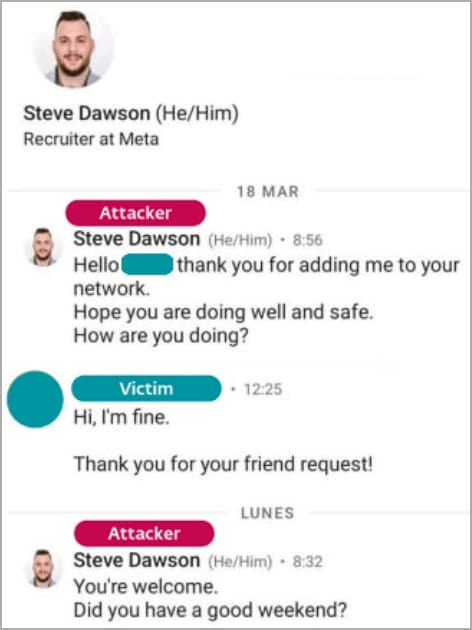
Supply: ESET
At later phases of the dialogue, the sufferer was requested to show their proficiency in C++ programming by downloading some quizzes that had been shared as executables inside ISO recordsdata.
As soon as these executables had been launched, an extra payload from the ISO photographs was silently dropped onto the sufferer’s machine through DLL side-loading (mscoree.dll) utilizing a legit program (PresentationHost.exe).
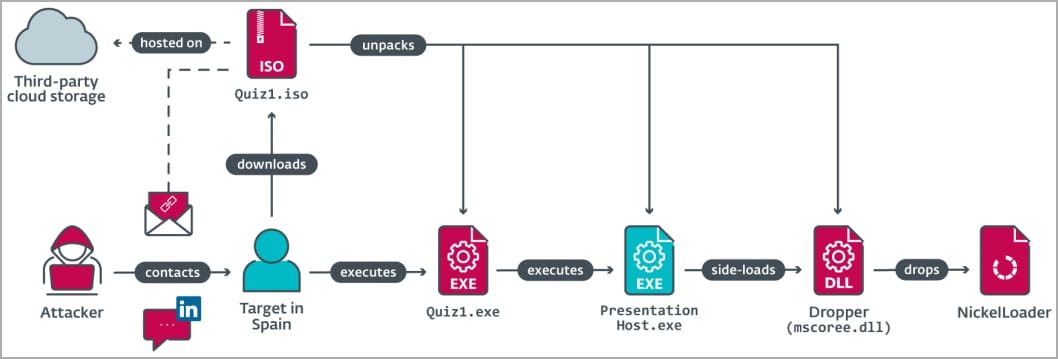
Supply: ESET
That payload is the NickelLoader malware loader, seen deploying two backdoors, a variant of BlindingCan with toned-down performance (miniBlindingCan) and LightlessCan.
The instructions supported by miniBlindingCan are:
- Ship system particulars (laptop title, Home windows model, code web page).
- Replace communication interval (worth from C2 server).
- Cease command execution.
- Ship 9,392-byte configuration to C2 server.
- Replace encrypted 9,392-byte configuration on file system.
- Watch for the following command.
- Replace communication interval (from configuration).
- Obtain & decrypt recordsdata from C2 server.
- Execute the supplied shellcode.
The LightlessCan backdoor
ESET says LightlessCan is a successor to BlindingCan, based mostly on supply code and command ordering similarities, that includes a extra subtle code construction, completely different indexing, and enhanced performance.
The model sampled from the assault on the Spanish aerospace group is 1.0, that includes assist for 43 instructions. Nevertheless, ESET says there are one other 25 instructions within the code which haven’t been carried out but.
The malware replicates many native Home windows instructions like ping, ipconfig, netstant, mkdir, schstasks, systeminfo, and so forth., so it could execute them with out showing within the system console for higher stealthiness in opposition to real-time monitoring instruments.
Since these instructions are closed-source, ESET feedback that Lazarus has both managed to reverse engineer the code or drew inspiration from the open-source variations.
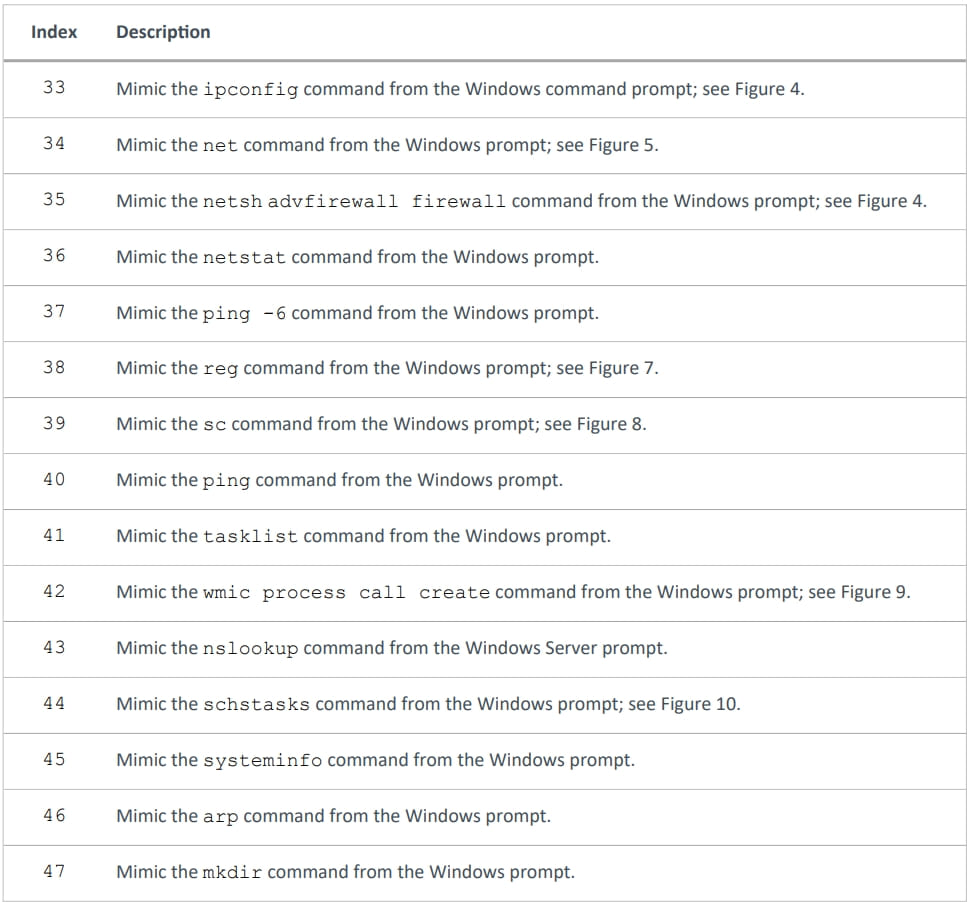
Supply: ESET
One other attention-grabbing facet reported by ESET is that one of many LightlessCan payloads they sampled was encrypted and will solely be decrypted utilizing a key depending on the goal’s surroundings.
That is an lively safety measure to stop outdoors entry to the sufferer’s laptop, for instance, by safety researchers or analysts.
This discovery underscores that Lazarus’ Operation Dreamjob is just not solely pushed by monetary aims, akin to cryptocurrency theft, but additionally encompasses espionage objectives.
Additionally, the introduction of a brand new subtle payload, the LightlessCan, is a regarding growth for organizations that may discover themselves within the cross-hairs of the North Korean risk group.


