Malicious advertisements served inside Microsoft Bing’s synthetic intelligence (AI) chatbot are getting used to distribute malware when trying to find fashionable instruments.
The findings come from Malwarebytes, which revealed that unsuspecting customers may be tricked into visiting booby-trapped websites and putting in malware immediately from Bing Chat conversations.
Launched by Microsoft in February 2023, Bing Chat is an interactive search expertise that is powered by OpenAI’s giant language mannequin known as GPT-4. A month later, the tech big started exploring putting advertisements within the conversations.
However the transfer has additionally opened the doorways for menace actors who resort to malvertising techniques and propagate malware.
“Adverts may be inserted right into a Bing Chat dialog in numerous methods,” Jérôme Segura, director of menace intelligence at Malwarebytes, stated. “A type of is when a consumer hovers over a hyperlink and an advert is displayed first earlier than the natural consequence.”

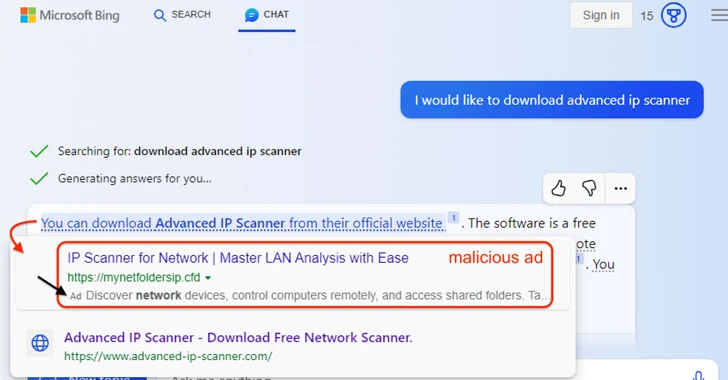
In an instance highlighted by the cybersecurity vendor, a Bing Chat question to obtain a official software program known as Superior IP Scanner returned a hyperlink that, when hovered, displayed a malicious advert pointing to a fraudulent hyperlink earlier than the official website internet hosting the software.
Clicking the hyperlink takes the consumer to a visitors course system (TDS) that fingerprints and determines if the request is definitely originating from an actual human (versus a bot, crawler, or sandbox), earlier than taking them to a decoy web page containing the rogue installer.
The installer is configured to run a Visible Fundamental Script that beacons to an exterior server with the probably aim of receiving the next-stage payload. The precise nature of the malware delivered is presently unknown.
A notable side of the marketing campaign is that the menace actor managed to infiltrate the advert account of a official Australian enterprise and create the advertisements.
“Menace actors proceed to leverage search advertisements to redirect customers to malicious websites internet hosting malware,” Segura stated. “With convincing touchdown pages, victims can simply be tricked into downloading malware and be none the wiser.”
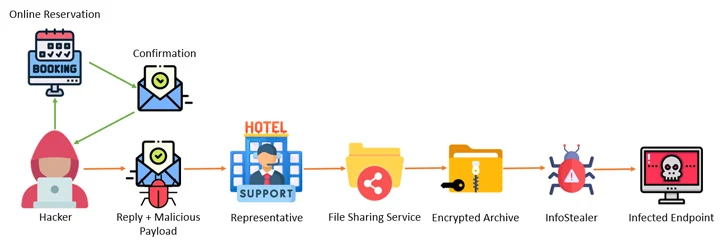
The revelation comes as Akamai and Notion Level uncovered a multi-step marketing campaign that entails attacking the programs of inns, reserving websites, and journey businesses with info stealer malware after which leveraging the entry to the accounts to go after monetary knowledge belonging to clients utilizing pretend reservation pages.
“The attacker, masquerading because the resort, reaches out to the shopper by way of the reserving website, urging the shopper to ‘re-confirm their bank card,’ then steals the shopper’s info,” Akamai researcher Shiran Guez stated, noting how the assaults prey on the sufferer’s sense of urgency to tug off the operation.
Battle AI with AI — Battling Cyber Threats with Subsequent-Gen AI Instruments
Able to sort out new AI-driven cybersecurity challenges? Be part of our insightful webinar with Zscaler to handle the rising menace of generative AI in cybersecurity.
Cofense, in a report printed this week, stated the hospitality sector has been on the receiving finish of a “well-crafted and revolutionary social engineering assault” that is designed to ship stealer malware resembling Lumma Stealer, RedLine Stealer, Stealc, Spidey Bot, and Vidar.
“As of now, the marketing campaign solely targets the hospitality sector, primarily concentrating on luxurious resort chains and resorts, and makes use of lures relative to that sector resembling reserving requests, reservation adjustments, and particular requests,” Cofense stated.
“The lures for each the reconnaissance and phishing emails match accordingly and are properly thought out.”
The enterprise phishing menace administration agency stated it additionally noticed malicious HTML attachments meant to hold out Browser-in-the-Browser (BitB) assaults by serving seemingly innocuous pop-up home windows that entice electronic mail recipients into offering their Microsoft credentials.
The discoveries are an indication that menace actors are continually discovering new methods to infiltrate unwitting targets. Customers ought to keep away from clicking on unsolicited hyperlinks, even when they give the impression of being official, be suspicious of pressing or threatening messages asking for quick motion, and examine URLs for indicators of deception.