
The Matanbuchus malware loader has been seen being distributed via social engineering over Microsoft Groups calls impersonating IT helpdesk.
Matanbuchus is a malware-as-a-service operation seen promoted on the darkish net first in early 2021. It was marketed as a $2,500 Home windows loader that executes malicious payloads instantly in reminiscence to evade detection.
In June 2022, menace analyst Brad Duncan reported that the malware loader was getting used to ship Cobalt Strike beacons in a large-scale malspam marketing campaign.
Researchers at Morphisec endpoint menace prevention firm discovered that the newest analyzed model of Matanbuchus consists of enhanced evasion, obfuscation, and post-compromise capabilities.
Microsoft Groups abuse
Microsoft Groups has been abused over the previous years to breach organizations utilizing social engineering to ship the primary stage malware.
Usually, attackers infiltrate the chat and trick customers into downloading a malicious file that then introduces the preliminary payload on system.
In 2023, a researcher created a specialised software that exploited bugs within the software program to permit malware supply from exterior accounts.
Final yr, DarkGate malware operators abused Microsoft Groups to ship their loader onto targets who used lax ‘Exterior Entry’ settings.
Based on Morphisec, operators of the newest Matanbuchus variant, 3.0, additionally present a choice for Microsoft Groups for preliminary entry.
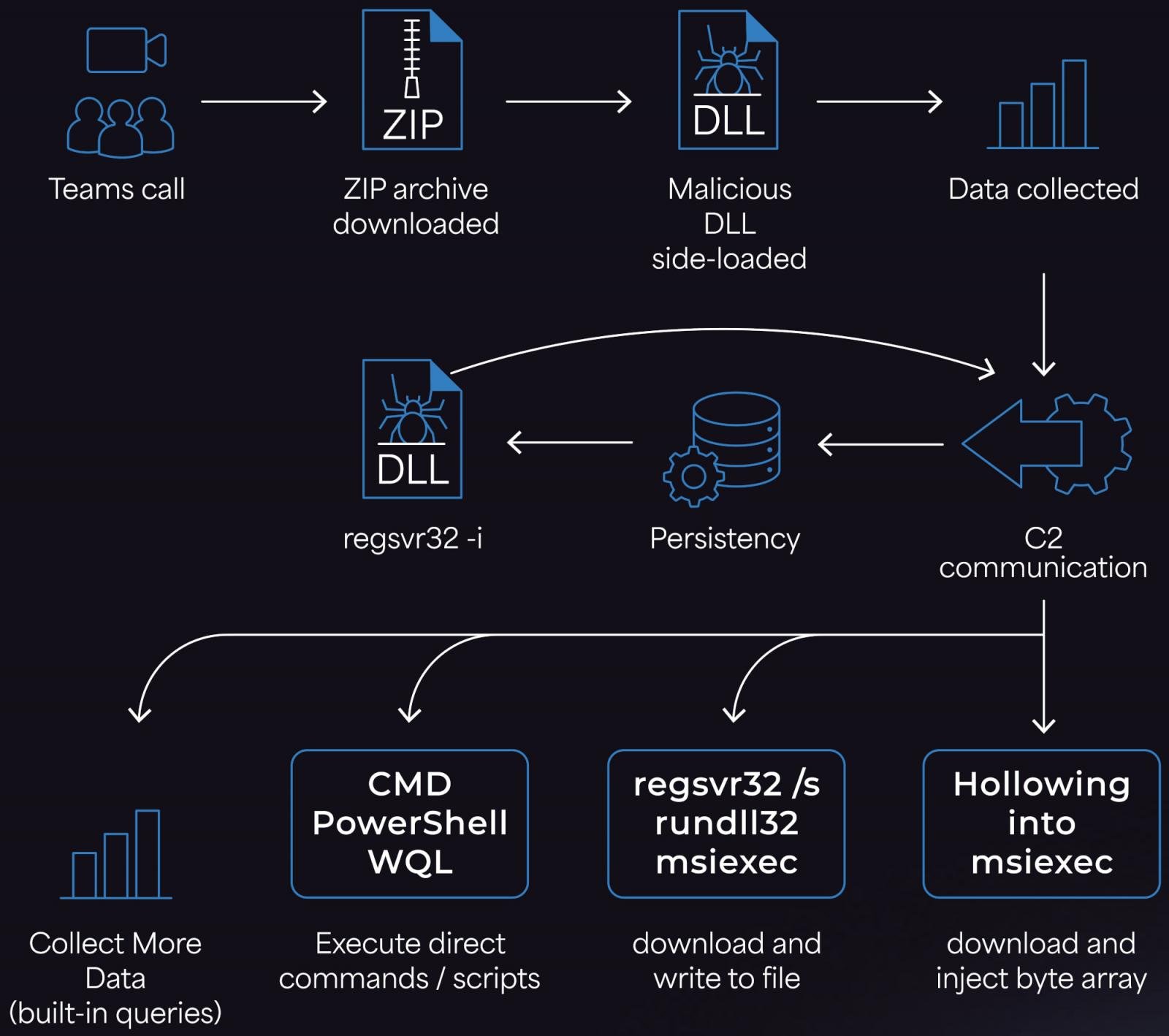
The attacker initiates an exterior Microsoft Groups name, posing as a professional IT helpdesk, convincing the goal to launch Fast Help, the distant help software constructed into Home windows.
Fast Help permits the attacker to achieve interactive distant entry and comply with up by instructing the consumer to execute a PowerShell script.
This script downloads and extracts a ZIP archive with three information which can be used to launch the Matanbuchus loader on the gadget through DLL side-loading.
Supply: Morphisec
Matanbuchus 3.0
Morphisec stories that Matanbuchus 3.0 introduces a number of new options and enhancements. The builders switched the command-and-control (C2) communication and string obfuscation from RC4 to Salsa20
The payloads are actually launched in reminiscence, and there’s a new anti-sandbox verification routine to make it possible for the malware runs solely on the outlined locales.
As an alternative of calling Home windows API capabilities, the malware now executes syscalls through customized shellcode that bypasses Home windows API wrappers and EDR hooks, hiding actions which can be generally monitored by safety instruments.
API calls are additional obfuscated through the use of the ‘MurmurHash3’ non-cryptographic hash operate, which makes reverse engineering and static evaluation harder.
Concerning Matanbuchus 3.0 post-infection capabilities, it might execute CMD instructions, PowerShell, or EXE, DLL, MSI, and shellcode payloads.
The malware collects particulars akin to username, area, OS construct info, operating EDR/AV processes, and the elevation standing of its course of (admin or common consumer).
Morphisec’s anlysis discovered that the malware checks the operating processes to determine safety instruments on the system, noting that the exection strategies despatched again from the C2 “are probably depending on the present safety stack of the sufferer.”
The researchers printed a detailed technical evaluation of the malware and say that Matanbuchus has developed “into a complicated menace.”
In addition they present indicators of compromise that embody malware samples and domains utilized by the malware.


