
Constructing automation big Johnson Controls is notifying people whose knowledge was stolen in an enormous ransomware assault that impacted the corporate’s operations worldwide in September 2023.
Johnson Controls is a multinational conglomerate that develops and manufactures industrial management techniques, safety gear, HVAC techniques, and hearth security gear for buildings. The corporate employs over 100,000 folks via its company operations and subsidiaries throughout 150 nations, reporting gross sales of $27.4 billion in 2024.
As BleepingComputer first reported, Johnson Controls was hit by a ransomware assault in September 2023, following a breach of the corporate’s Asian places of work in February 2023 and subsequent lateral motion via its community.
“Primarily based on our investigation, we decided that an unauthorized actor accessed sure Johnson Controls techniques from February 1, 2023 to September 30, 2023 and took info from these techniques,” the corporate says in knowledge breach notification letters filed with California’s Legal professional Common, redacted to hide what info was stolen within the assault.
“After turning into conscious of the incident, we terminated the unauthorized actor’s entry to the affected techniques. As well as, we engaged third-party cybersecurity specialists to additional examine and resolve the incident. We additionally notified legislation enforcement and publicly disclosed the incident in filings on September 27, 2023; November 13, 2023; and December 14, 2023.”
The cyberattack pressured Johnson Controls to close down massive parts of its IT infrastructure after the risk actors encrypted many units, which affected its operations worldwide and customer-facing techniques.
Johnson Controls confirmed in a January 2024 SEC submitting that the cyberattack was orchestrated by a ransomware gang that additionally stole paperwork from compromised techniques through the breach.
Whereas the agency did not attribute the incident to a selected ransomware operation, the assault was linked to the Darkish Angels ransomware group based mostly on a pattern of a VMware ESXi encryptor deployed through the breach, which said that it was used towards Johnson Controls.
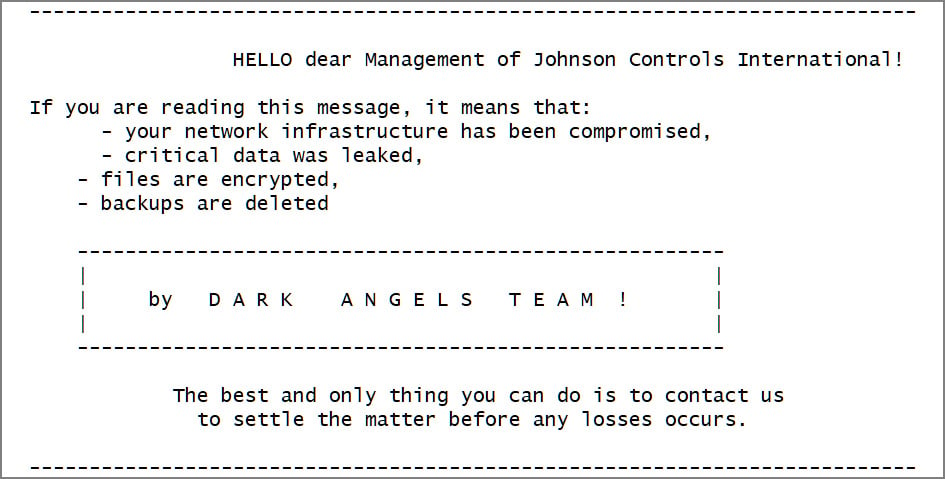
BleepingComputer was additionally instructed that the ransom be aware linked to a negotiation chat the place the ransomware gang demanded $51 million for a decryptor and to delete knowledge stolen from Johnson Controls’ community.
The ransomware operators additionally encrypted the corporate’s VMware ESXi digital machines through the assault and claimed to have stolen over 27 TB of paperwork containing company knowledge.
On the time, the corporate said that bills associated to incident response and remediation had already reached $27 million, but in addition famous that it anticipated this quantity to extend because the investigation and remediation efforts progressed.
Darkish Angels, the ransomware operation behind Johnson Controls’ 2023 breach, surfaced in Might 2022 when it started focusing on organizations worldwide in double-extortion assaults. In these assaults, the group steals delicate knowledge and makes use of it to strain victims below the specter of publishing it on-line on its darkish net leak web site, referred to as Dunghill Leaks.
In addition they deploy ransomware to encrypt all units on the community after getting access to the Home windows area controller, utilizing Home windows and VMware ESXi encryptors based mostly on leaked Babuk ransomware supply code.
Nonetheless, cybersecurity researcher MalwareHunterTeam instructed BleepingComputer that the Linux encryptor used within the Johnson Controls assault was the identical as others utilized by Ragnar Locker ransomware since 2021.



