
A brand new FileFix assault permits executing malicious scripts whereas bypassing the Mark of the Internet (MoTW) safety in Home windows by exploiting how browsers deal with saved HTML webpages.
The approach, was devised by safety researcher mr.d0x Final week, the researcher confirmed how the first FileFix methodology labored as an alternative choice to ‘ClickFix’ assaults by tricking customers into pasting a disguised PowerShell command into the File Explorer handle bar.
The assault entails a phishing web page to trick the sufferer into copying a malicious PowerShell command. As soon as they previous it into File Explorer, Home windows executes the PowerShell, making it a really delicate assault.
With the new FileFix assault, an attacker would use social engineering to trick the person into saving an HTML web page (utilizing Ctrl+S) and renaming it to .HTA, which auto-executes embedded JScript through mshta.exe.
HTML Functions (.HTA) are thought-about legacy expertise. This Home windows file sort can be utilized to execute HTML and scripting content material utilizing the professional mshta.exe within the context of the present person.
The researcher discovered that when HTML information are saved as “Webpage, Full” (with MIME sort textual content/html), they don’t obtain the MoTW tag, permitting script execution with out warnings for the person.
When the sufferer opens the .HTA file, the embedded malicious script runs instantly with none warning.
The best-friction a part of the assault is the social engineering step, the place victims have to be tricked into saving a webpage and renaming it.
A method round that is by designing a simpler bait, equivalent to malicious web site prompting customers to save lots of multi-factor authentication (MFA) codes to take care of future entry to a service.
The web page would instruct the person to press Ctrl+S (Save As), select “Webpage, Full,” and save the file as ‘MfaBackupCodes2025.hta.’
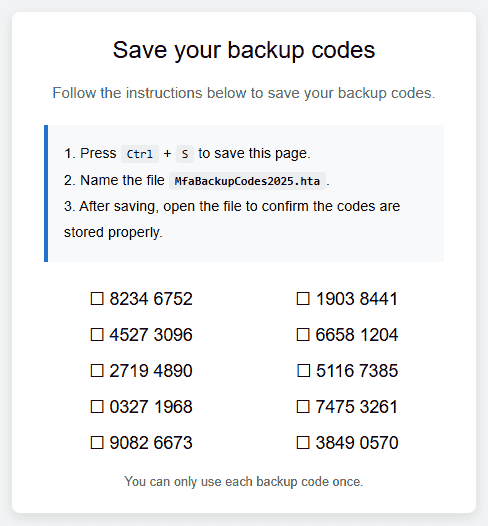
Supply: mr.d0x
Though this require extra interplay, if the malicious webpage appears real and the person does not have a deep understanding of file extensions and safety warnings, they might nonetheless fall for it.
An efficient protection technique towards this variant of the FileFix assault is to disable or take away the ‘mshta.exe’ binary out of your setting (present in C:WindowsSystem32 and C:WindowsSysWOW64).
Moreover, take into account enabling file extension visibility on Home windows and blocking HTML attachments on e-mail.



