
An ongoing phishing marketing campaign abuses a little bit‑recognized function in Microsoft 365 known as “Direct Ship” to evade detection by electronic mail safety and steal credentials.
Direct Ship is a Microsoft 365 function that permits on‑premises units, functions, or cloud providers to ship emails via a tenant’s good host as in the event that they originated from the group’s area. It’s designed to be used by printers, scanners, and different units that must ship messages on behalf of the corporate.
Nevertheless, the function is a recognized safety threat, because it does not require any authentication, permitting distant customers to ship inside‑trying emails from the corporate’s area.
Microsoft recommends that solely superior clients make the most of the function, as its security is determined by whether or not Microsoft 365 is configured accurately and the good host is correctly locked down..
“We suggest Direct Ship just for superior clients prepared to tackle the tasks of electronic mail server admins,” explains Microsoft.
“You must be accustomed to organising and following finest practices for sending electronic mail over the web. When accurately configured and managed, Direct Ship is a safe and viable choice. However clients run the chance of misconfiguration that disrupts mail movement or threatens the safety of their communication.”
The corporate has shared methods to disable the function, that are defined later within the article, and says they’re engaged on a method to deprecate the function.
Direct Ship abused in a phishing marketing campaign
The phishing marketing campaign was found by the Varonis Managed Knowledge Detection and Response (MDDR) group, who instructed BleepingComputer that it’s concentrating on greater than 70 organizations throughout all industries, with 95% of the victims based mostly in america.
Varonis says the marketing campaign began in Could 2025, with over 95% of the focused firms based mostly in america.
“Victims occupy all kinds of enterprise verticals however over 90% of recognized targets function throughout the Monetary Companies, Development, Engineering, Manufacturing, Healthcare, and Insurance coverage house,” Joseph Avanzato, Safety Operations and Forensics Group Chief, instructed BleepingComputer.
“Monetary Companies had been the commonest goal adopted by Manufacturing, Development/Engineering and Healthcare/Insurance coverage.”
The Varonis report explains that the assaults are delivered through PowerShell utilizing a focused firm’s good host (company-com.mail.safety.outlook.com), making it attainable for an attacker to ship inside‑trying messages from exterior IP addresses.
An instance PowerShell command that may ship emails through the Direct Ship function is:
Ship‑MailMessage -SmtpServer firm‑com.mail.safety.outlook.com -To joe@firm.com -From joe@firm.com -Topic "New Missed Fax‑msg" -Physique "You've acquired a name! Click on on the hyperlink to hearken to it. Pay attention Now" -BodyAsHtmlThis methodology works as a result of utilizing Direct Ship with the good host does not require authentication and treats the sender as inside, permitting risk actors to bypass SPF, DKIM, DMARC, and different filtering guidelines.
The e-mail campaigns impersonate voicemail or fax notifications with electronic mail topics of “Caller Left VM Message.” Hooked up to the emails are PDF attachments titled ‘Fax-msg’, ‘Caller left VM Message’, ‘Play_VM-Now’, or ‘Pay attention’.
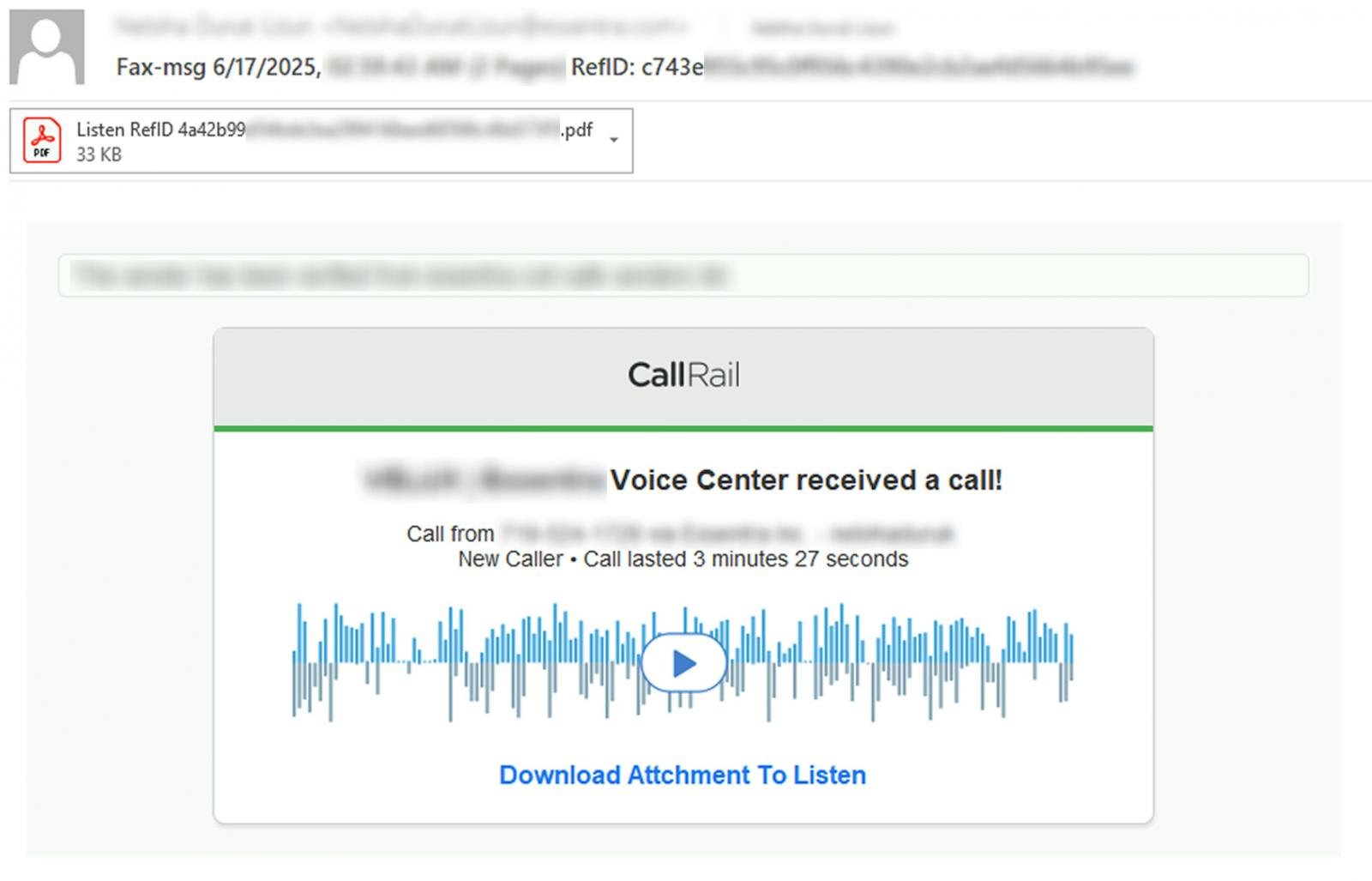
Supply: Varonis
What’s uncommon in regards to the marketing campaign is that PDF attachments don’t comprise hyperlinks to the phishing pages.
As an alternative, the paperwork instruct targets to scan a QR code with their smartphone digital camera to hearken to the voicemail. The PDF paperwork are additionally branded with the corporate emblem to make them seem extra reliable.
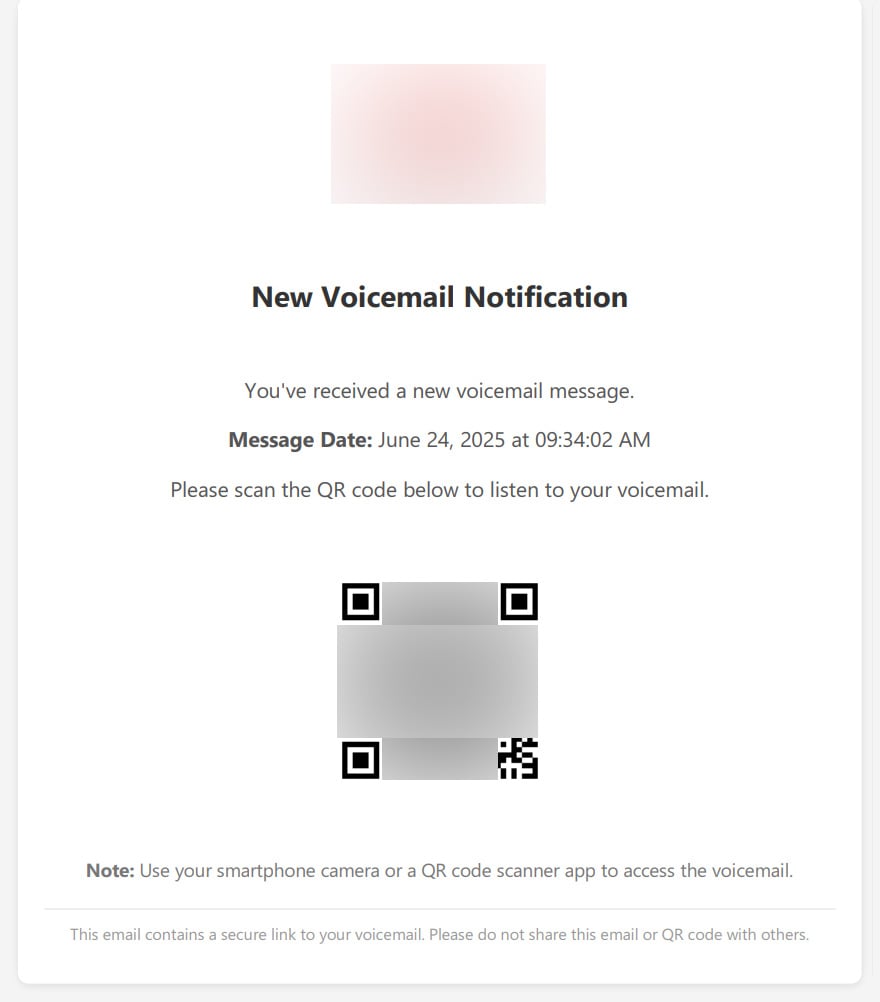
Supply: BleepingComputer
Scanning the QR code and opening the hyperlink brings you to a phishing website that shows a faux Microsoft login type, which might be used to steal the worker’s credentials.
In a single case seen by Varonis, the place an organization acquired irregular conduct alerts, the risk actors used PowerShell to ship emails via the good host from a Ukrainian IP handle of 139.28.36[.]230 and others in the identical vary.
These messages failed SPF and DMARC checks, however they had been handled as trusted inside site visitors as a result of they got here via the inner good host.
In one other electronic mail from this marketing campaign seen by BleepingComputer, the e-mail appeared to come back from an inside electronic mail handle and was delivered through the group’s good host regardless of additionally failing SPF, DKIM, and DMARC. This electronic mail originated from the IP handle 51.89.86[.]105.
Varonis shared additional indicators of compromise (IOCs) of their report, together with domains which are used within the marketing campaign.
Mitigating Direct Ship phishing assaults
To mitigate this risk, Varonis recommends enabling the “Reject Direct Ship” setting within the Change Admin Heart, which Microsoft launched in April 2025.
Microsoft launched this function as they usually counsel firms allow SPF soft-fail to stop potential routing errors. Nevertheless, this made it not possible to dam electronic mail despatched through Direct Ship.
“Whereas SPF offers safety from spoofing of your domains, we suggest clients use a Comfortable Fail SPF configuration attributable to the potential of legitimate routing eventualities falling foul of SPF failures,” explains Microsoft.
“As such, no function existed to dam Direct Ship site visitors for the various clients who haven’t any want to make use of it. To this finish we’ve got developed the Reject Direct Ship setting for Change On-line and are asserting the Public Preview for this function right this moment.”
Varonis additionally recommends implementing a strict DMARC coverage (p=reject), flagging unauthenticated inside messages for assessment or quarantine, imposing SPF hardfail inside Change On-line Safety, enabling Anti‑Spoofing insurance policies, and coaching staff to identify QR phishing makes an attempt.
“Direct Ship is a robust function, however within the improper fingers it turns into a harmful assault vector,” concludes Varonis.
“For those who’re not actively monitoring spoofed inside emails or have not enabled these protections, now could be the time. Do not assume inside means secure.”


