
Two malicious RubyGems packages posing as standard Fastlane CI/CD plugins redirect Telegram API requests to attacker-controlled servers to intercept and steal information.
RubyGems is the official bundle supervisor for the Ruby programming language, used for distributing, putting in, and managing Ruby libraries (gems), just like npm for JavaScript and PyPI for Python.
The packages intercept delicate information, together with chat IDs and message content material, hooked up information, proxy credentials, and even bot tokens that can be utilized for hijacking Telegram bots.
The provision chain assault was found by Socket researchers, who warned the Ruby builders group concerning the danger through a report.
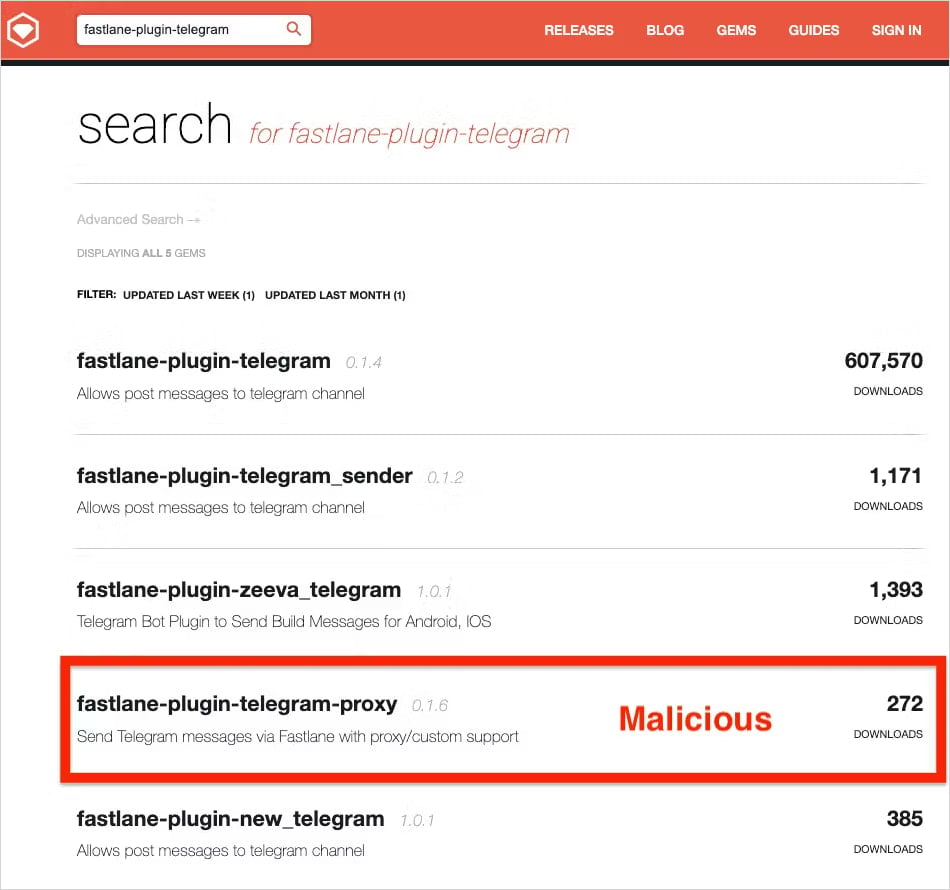
The 2 packages that typosquat Fastlane are nonetheless dwell on RubyGems beneath the next names:
- fastlane-plugin-telegram-proxy: Revealed on Could 30, 2025, has 287 downloads
- fastlane-plugin-proxy_teleram: Revealed on Could 24, 2025, has 133 downloads
Quick lane to information theft
Fastlane is a respectable open-source plugin that serves as an automation device for cell app builders. It’s used for code signing, compiling builds, app retailer importing, notification supply, and metadata administration.
The ‘fastlane-plugin-telegram’ is a respectable plugin that permits Fastlane to ship notifications over Telegram utilizing a Telegram bot that posts on a specified channel.
That is useful for builders who want real-time updates on CI/CD pipelines inside their Telegram workspace, permitting them to maintain observe of key occasions with out having to test dashboards.
Supply: Socket
The malicious gems found by Socket are practically an identical to the respectable plugin, that includes the identical public API, readme file, documentation, and core performance.
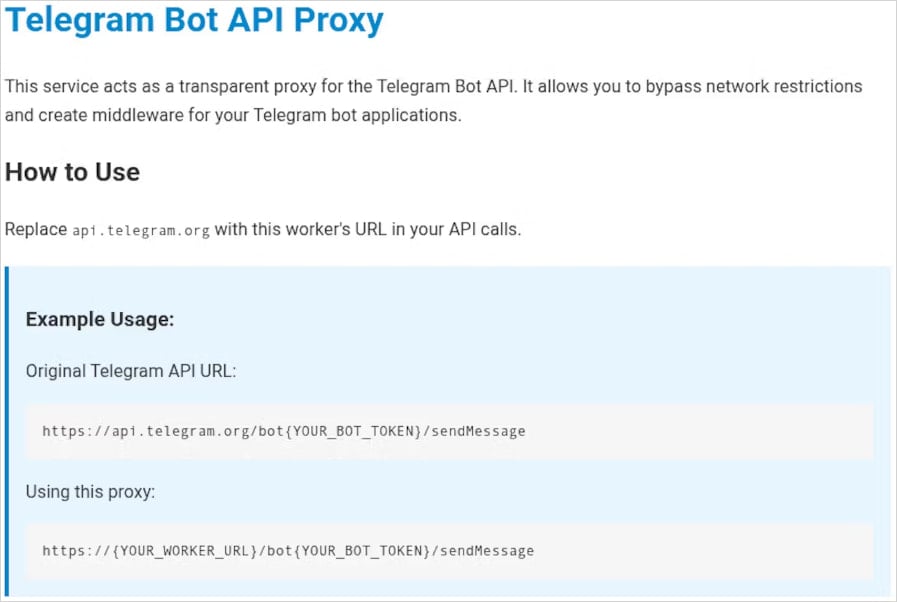
The one distinction, albeit an important one, is swapping out the respectable Telegram API endpoint (https://api.telegram.org/) with the attacker’s proxy-controlled endpoint (rough-breeze-0c37[.]buidanhnam95[.]staff[.]dev), in order that delicate data is intercepted (and really doubtless collected).
Supply: Socket
Stolen information contains the bot token, the message information, any uploaded information, and proxy credentials if configured.
The attacker has ample alternative for exploitation and persistence as a result of Telegram bot tokens stay legitimate till manually revoked by the sufferer.
Socket notes that the gems’ touchdown pages point out that the proxy “doesn’t retailer or modify your bot tokens,” nevertheless, there isn’t any approach to confirm this declare.
“Cloudflare Employee scripts will not be publicly seen, and the risk actor retains full capability to log, examine, or alter any information in transit,” explains Socket.
“Using this proxy, mixed with the typosquatting of a trusted Fastlane plugin, clearly signifies intent to exfiltrate tokens and message information beneath the guise of regular CI conduct.”
“Furthermore, the risk actor has not printed the Employee’s supply code, leaving its implementation completely opaque.”
Builders who’ve put in the 2 malicious gems ought to take away them instantly and rebuild any cell binaries produced after the set up date. Additionally, all bot tokens used with Fastlane ought to be rotated as they’ve been compromised.
Socket additionally suggests blocking visitors to ‘*.staff[.]dev’ except explicitly wanted.



