
The ransomware scene is re-organizing, with one gang often known as DragonForce working to assemble different operations underneath a cartel-like construction.
DragonForce is now incentivizing ransomware actors with a distributed affiliate branding mannequin, offering different ransomware-as-a-service (RaaS) operations a method to hold out their enterprise with out coping with infrastructure upkeep value and energy.
A bunch’s consultant instructed BleepingComputer that they’re purely financially motivated but in addition comply with an ethical compass and are in opposition to attacking sure healthcare organizations.
Sometimes, a RaaS operation has its personal associates or companions, and the ransomware developer supplies the file-encrypting malware and the infrastructure.
Associates would construct a variant of the encrypting package deal, breach sufferer networks, and deploy the ransomware. They’d additionally handle the decryption keys and normally negotiate with the sufferer for a ransom fee.
The developer additionally maintains a so-called knowledge leak website (DLS) the place they publish data stolen from victims who didn’t pay the attacker.
In alternate for utilizing their malware and infrastructure, the developer prices associates a payment from obtained ransoms that’s usually as much as 30%.
The DragonForce ransomware enterprise
DragonForce now calls itself a “ransomware cartel” and takes 20% of the paid ransoms.
Below its mannequin, associates get entry to the infrastructure (negotiation instruments, storage for stolen knowledge, malware administration), and use the DragonForce encryptor underneath their very own branding.
The group introduced the “new path” in March, saying that associates can create their “personal model underneath the auspices of an already confirmed accomplice.”
Because the submit under says, DragonForce goals to handle “limitless manufacturers” that may goal ESXi, NAS, BSD, and Home windows programs.
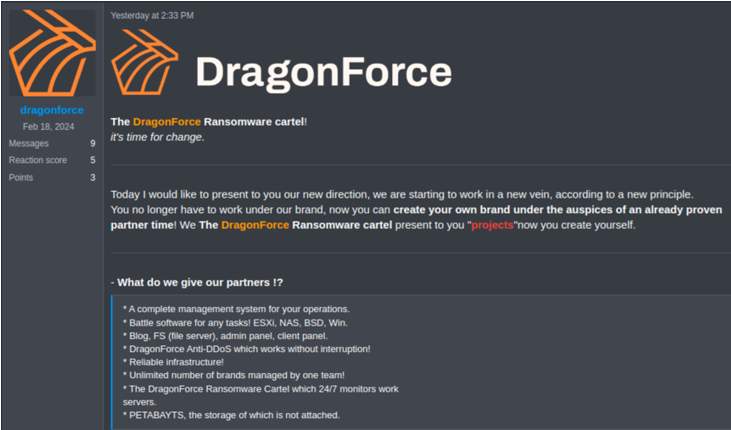
supply: Secureworks
DragonForce instructed BleepingComputer that their construction is that of a market, the place associates can select to deploy assaults underneath the DragonForce model or a distinct one.
Principally, teams of menace actors can use the service and white label underneath their very own identify so it seems they’re their very own model.
In return, they don’t should cope with the headache of working knowledge leak and negotiation websites, develop malware, or cope with negotiations.
There are guidelines to abide by, although, and associates will probably be kicked out on the first misstep. “We’re sincere companions who respect the principles,” the DragonForce consultant instructed us.
“They should comply with the principles, and we will management that as a result of all the things we run is on our servers, in any other case it would not make sense,” DragonForce says.
These guidelines, nevertheless, can be found solely to menace actors embracing the newly proposed ransomware enterprise mannequin.
When requested if hospitals or healthcare organizations are off limits, DragonForce stated that all of it will depend on the kind of hospital, and confirmed what might be described as empathy.
“We do not assault most cancers sufferers or something coronary heart associated, we would slightly ship them cash and assist them. We’re right here for enterprise and cash, I did not come right here to kill folks, and neither did my companions,” the menace actor instructed BleepingComputer.
Researchers at cybersecurity firm Secureworks say that DragonForce’s mannequin could enchantment to a wider vary of associates and entice much less technical menace actors.
“Even subtle menace actors could admire the flexibleness that enables them to deploy their very own malware with out creating and sustaining their very own infrastructure” – Secureworks
By rising the affiliate base, DragonForce may take a look at bigger earnings pushed by the flexibleness of its proposed mannequin.
It’s unclear what number of ransomware associates have contacted DragonForce cartel in regards to the new service mannequin however the menace actor stated that the member record consists of well-known gangs.
“I can not let you know the precise quantity, however we have now gamers who come to us that you simply usually write about and need to cooperate with us,” DragonForce instructed BleepingComputer.
One new ransomware gang referred to as RansomBay has already subscribed to DragonForce’s mannequin.


