
Safety researchers found a multi-step data stealing marketing campaign the place hackers breach the techniques of lodges, reserving websites, and journey businesses after which use their entry to go after monetary knowledge belonging to prospects.
By utilizing this oblique strategy and a pretend Reserving.com cost web page, cybercriminals have discovered a mixture that ensures a considerably higher success price at accumulating bank card data.
Subsequent-level phishing
Usually, researchers noticed info-stealer campaigns that focused the hospitality business (e.g. Accommodations, journey businesses) utilizing “superior social engineering strategies” to ship info-stealing malware.
It begins with a easy question to make a reservation, or it refers to an current one, researchers at cybersecurity Notion Level say in a report earlier this month.
After establishing communication with the lodge, the criminals invoke a motive, resembling a medical situation or a particular request for one of many vacationers, to ship necessary paperwork through a URL.
The URL results in info-stealing malware that “is designed to function stealthily” and collects delicate knowledge like credentials or monetary data.
In a brand new report this week, researchers at web firm Akamai say that the assault goes past the step described above and strikes to focus on the purchasers of the compromised entity.
“After the infostealer is executed on the unique goal (the lodge), the attacker can entry messaging with respectable prospects” – Shiran Guez, data safety senior supervisor at Akamai
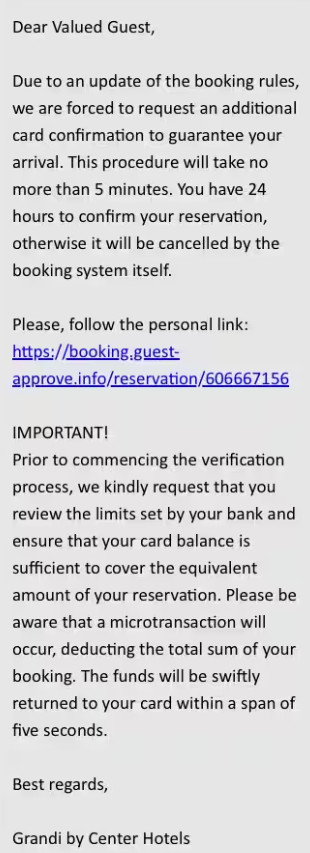
Having a direct and trusted communication channel with the ultimate sufferer, cybercriminals can ship their phishing message disguised as a respectable request from the now-compromised lodge, reserving service, or journey company.
The message asks for an extra bank card verification and depends on the frequent substances of a phishing textual content: requires instant motion and makes use of sound rationale to elucidate it.
Guez notes that the message “is written professionally and modeled after real lodge interactions with their company,” which eliminates all suspicion of a ploy.
supply: Akamai
“You will need to keep in mind that this message comes from throughout the reserving website’s message platform itself,” the researcher highlights.
For the reason that communication comes from the reserving website by way of the official channel, the goal has no motive to doubt its legitimacy.
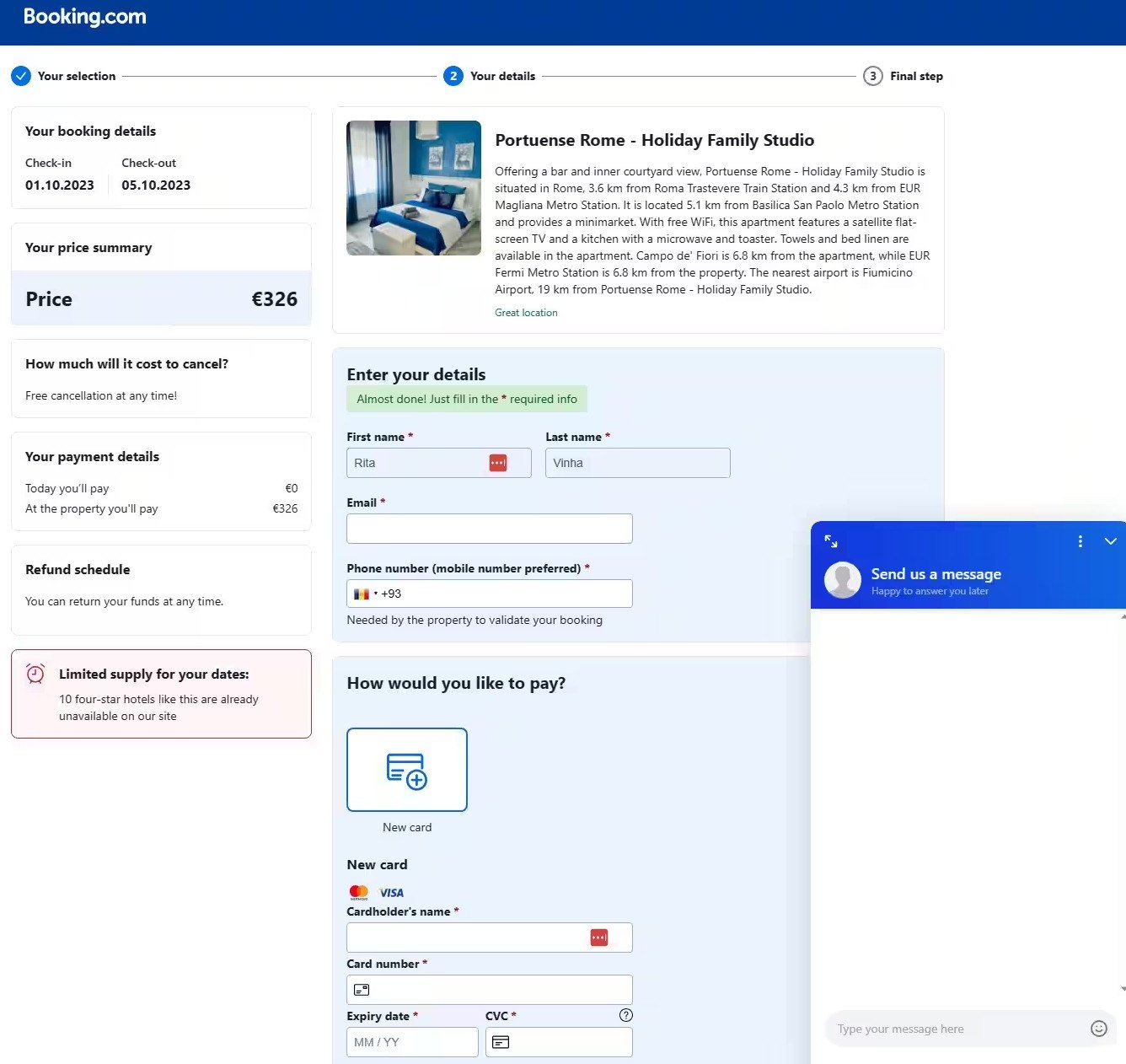
Pretend Reserving.com web page
Guez says that the sufferer receives a hyperlink for the alleged card verification to maintain the reservation. The hyperlink triggers on the sufferer machine an executable that’s encoded in a fancy JavaScript base64 script.
The researcher stresses that the script’s function is to detect details about the looking atmosphere and it’s designed to make evaluation considerably harder.
The attacker additionally included a number of safety validation and anti-analysis strategies to guarantee that solely potential victims attain the following stage of the rip-off, which reveals a pretend Reserving.com cost web page.
supply: Akamai
Regardless of the extra refined strategy that makes the trick very tough to identify, Guez says that the common indicators indicating a possible rip-off might nonetheless reveal the fraud.
Customers ought to keep away from clicking on unsolicited hyperlinks, even when they appear respectable, be suspicious of pressing or threatening messages asking for instant motion, and verify URLs for indicators of deception.
Nevertheless, to make sure you don’t fall sufferer to extra advanced phishing campaigns, the really helpful motion is to contact the corporate straight at an official e-mail tackle or telephone quantity and ask for clarifications concerning the message.


