
The Lumma information-stealer malware (aka ‘LummaC2’) is selling a brand new function that allegedly permits cybercriminals to revive expired Google cookies, which can be utilized to hijack Google accounts.
Session cookies are particular internet cookies used to permit a searching session to log in to an internet site’s providers routinely. As these cookies enable anybody possessing them to log in to the proprietor’s account, they generally have a restricted lifespan for safety causes to stop misuse if stolen.
Restoring these cookies would enable Lumma operators to achieve unauthorized entry to any Google account even after the reliable proprietor has logged out of their account or their session has expired.
Hudson Rock’s Alon Gal first noticed a discussion board publish by the info-stealer’s builders highlighting an replace launched on November 14, claiming the “skill to revive lifeless cookies utilizing a key from restore information (applies solely to Google cookies).”
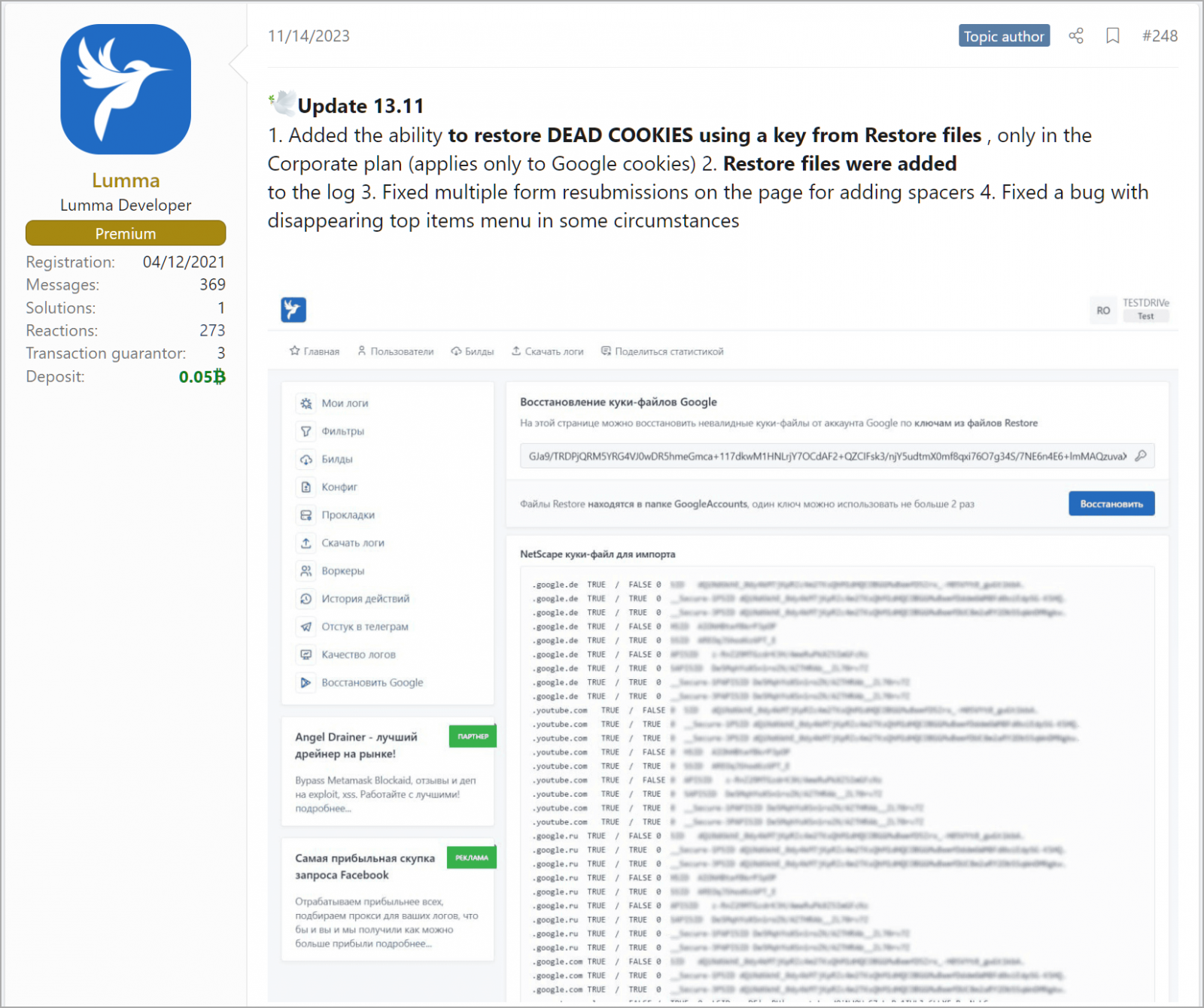
Supply: BleepingComputer
This new function was solely made accessible to subscribers of the highest-tier “Company” plan, which prices cybercriminals $1,000/month.
The discussion board publish additionally clarifies that every key can be utilized twice in order that cookie restoration can work just one time. That might nonetheless be sufficient to launch catastrophic assaults on organizations that in any other case comply with good safety practices.
This new function allegedly launched in current Lumma releases is but to be verified by safety researchers or Google, so whether or not or not it really works as marketed stays unsure.
Nonetheless, it’s price mentioning that one other stealer, Rhadamanthys, introduced an analogous functionality in a current replace, rising the probability that malware authors found an exploitable safety hole.
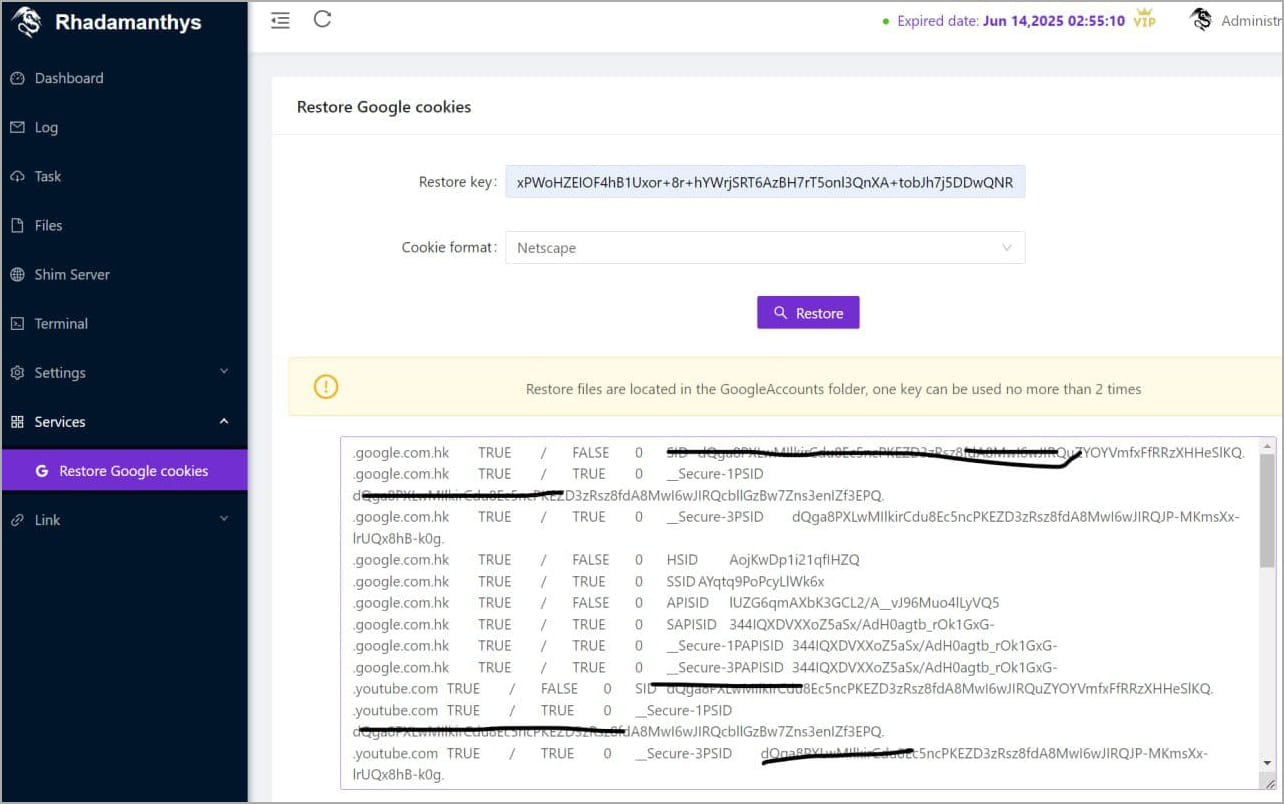
Supply: @g0njxa
BleepingComputer has contacted Google a number of instances requesting a touch upon the potential for malware authors having found a vulnerability in session cookies, however we’ve but to obtain a response.
A number of days after contacting Google, Lumma’s builders launched an replace that claims to be a further repair to bypass newly launched restrictions imposed by Google to stop cookie restoration.
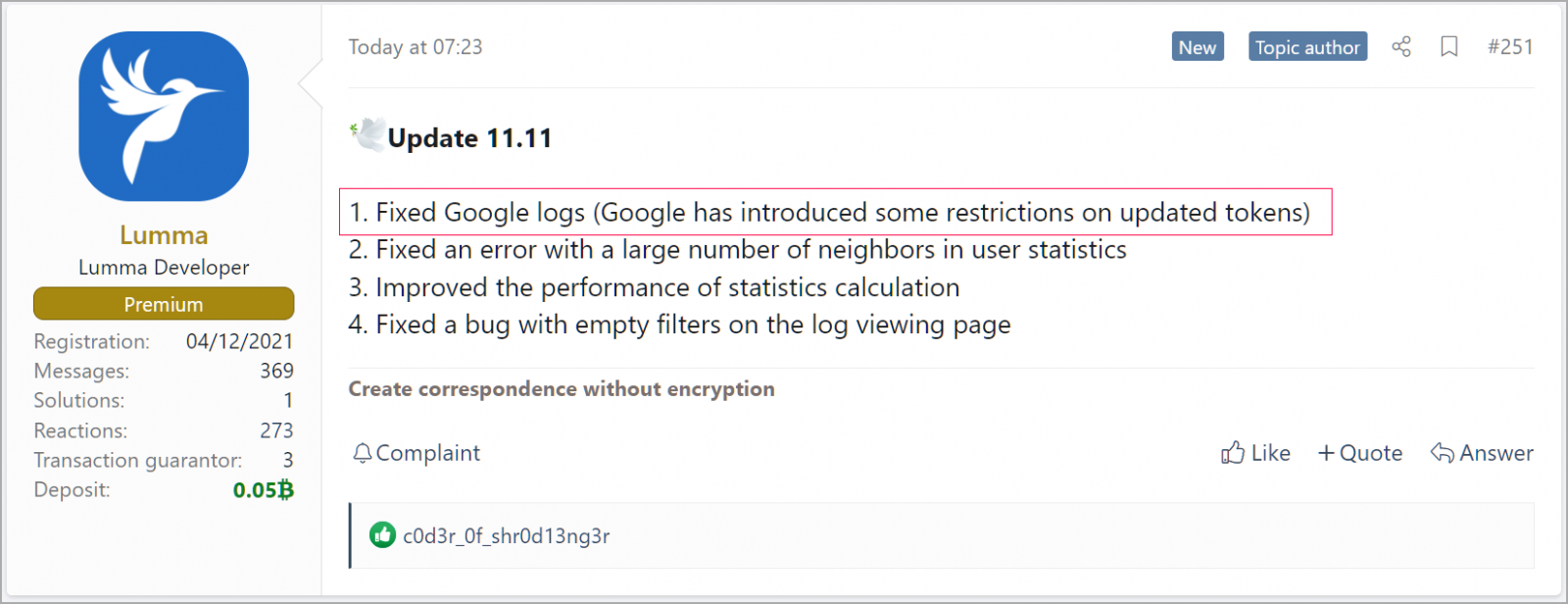
Supply: BleepingComputer
BleepingComputer has additionally tried to study extra about how the function works and what weak point it exploits instantly from Lumma. Nonetheless, a “assist agent” of the malware operation declined to share something about it.
When requested about the same function Rhadamantis added lately, Lumma’s agent advised us their rivals had carelessly copied the function from their stealer.
If information-stealers can certainly restore expired Google cookies as promoted, there’s nothing that customers can do to guard their accounts till Google pushes out a repair moreover stopping the malware an infection that results in the theft of these cookies.
Precautions embody avoiding downloads of torrent information and executables from doubtful web sites and skipping promoted ends in Google Search.


